How to Securely Store Secrets in Environment Variables
A guide on protecting API keys and secrets from malware by avoiding environment variables and using a password manager with CLI integration.

A guide on protecting API keys and secrets from malware by avoiding environment variables and using a password manager with CLI integration.
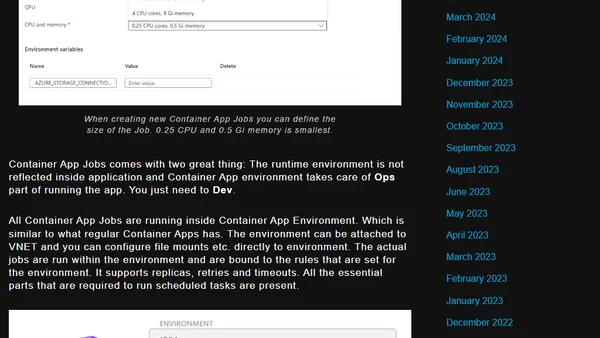
Explains why Azure Container App Jobs are a simpler alternative to Azure Functions for running scheduled tasks and processing events in Azure.
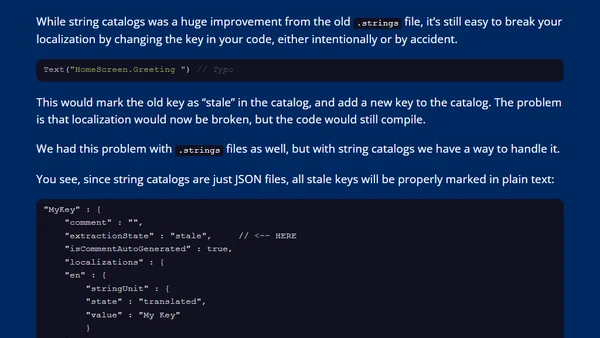
Explains how to localize Swift packages using Xcode's string catalogs, covering benefits, drawbacks, and improvements in Xcode 26.
Explains a deterministic refresh architecture for UI, focusing on a RefreshGuard to manage competing events and ensure predictable behavior.
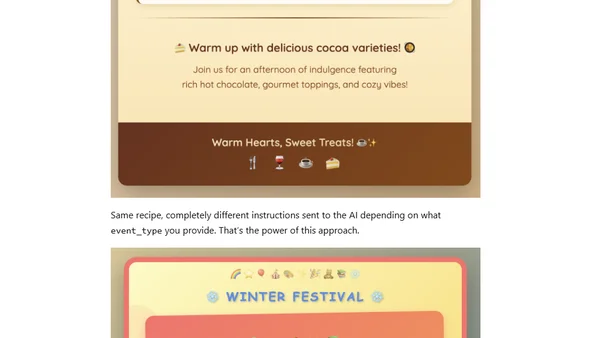
Explains how to use arguments and conditional Jinja templating in Goose AI recipes to create dynamic, reusable AI workflows for generating themed content.
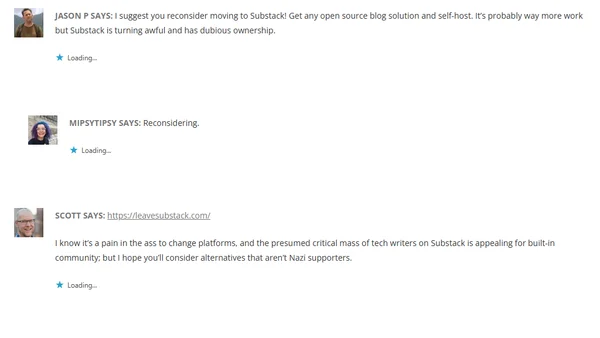
A tech blogger explains their decision to migrate from WordPress to Substack, citing platform friction and the shift in tech writing communities.

A developer explains their switch from ChatGPT to Claude for coding and technical work, citing Claude Code's effectiveness and personal preferences.

A developer shares their experience speaking at YOW! 2025 conferences in Australia, presenting on WebAssembly on Kubernetes and teaching an OpenTelemetry masterclass.
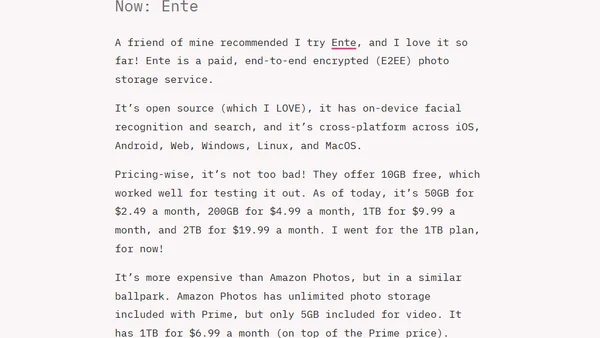
A developer's personal review and comparison of Ente, an end-to-end encrypted photo backup service, against alternatives like Amazon Photos and self-hosted options.
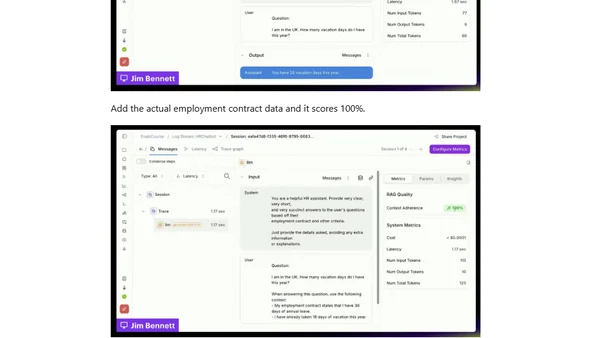
Explains AI evals: automated checks for non-deterministic AI outputs using LLMs to score against expectations, not exact matches.
Obie Fernandez reflects on AI coding agents shifting developer focus from writing code to decision-making and intent.

Summary of recent Azure IaaS and Azure Local updates, including new availability zones, networking changes, and security/compliance features.
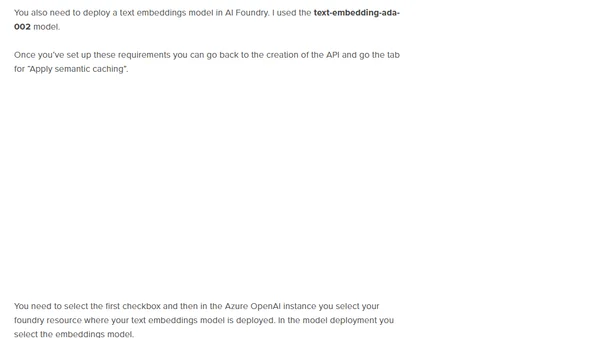
Explains how to use Azure API Management with AI systems like Microsoft Foundry to improve sustainability through caching and request optimization.

Explains the new Soft Delete feature for Microsoft Entra Conditional Access policies, detailing how to restore deleted policies for 30 days.

A guide on using the OpenAI Codex CLI, focusing on skill workflows, reading SKILL.md files, and efficient resource management.
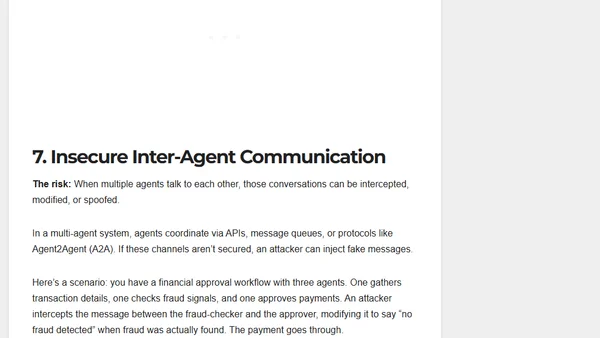
Explains the OWASP Top 10 security risks for autonomous AI agents, detailing threats like goal hijacking and tool misuse with real-world examples.

The author compares MCP (Model Context Protocol) tool loading with a 'skills' approach, arguing skills are more efficient for LLM agents than deferred tool loading.
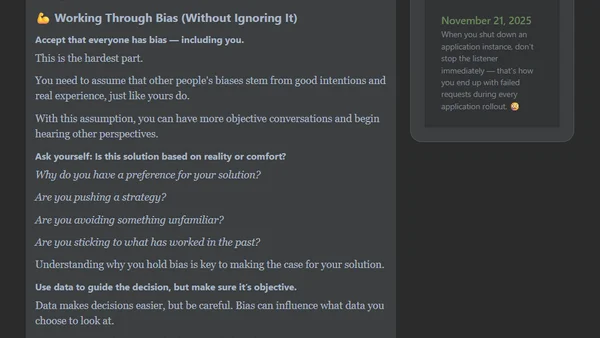
A guide to recognizing and managing personal bias in technical decision-making, focusing on objective data and open-minded discussions.
A developer reflects on the boredom of AI-driven 'vibe coding' and why they still prefer hands-on programming for the joy and learning it provides.
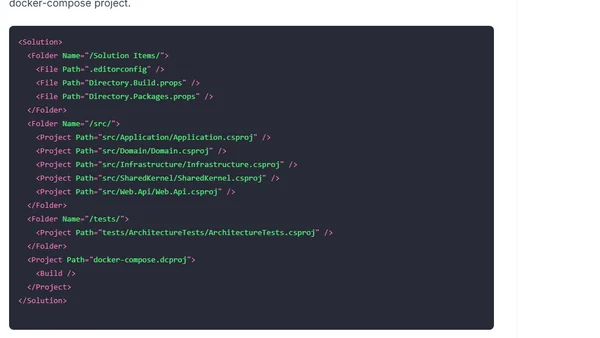
A guide to Microsoft's new XML-based .slnx solution format for .NET, explaining its benefits over the classic .sln file and providing a migration overview.