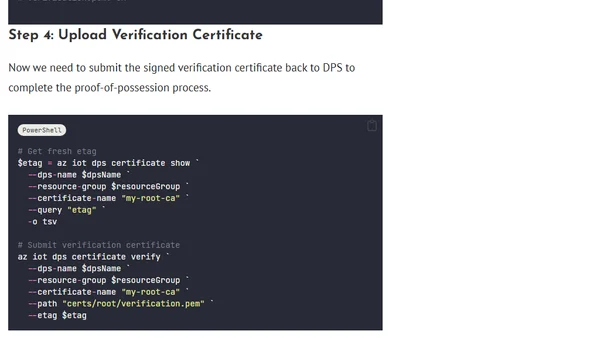
Using Azure Device Provisioning Service with Self Signed X.509 Certificates – Part 5
A technical guide on verifying X.509 certificate ownership for Azure IoT Device Provisioning Service using proof-of-possession.

A technical guide on verifying X.509 certificate ownership for Azure IoT Device Provisioning Service using proof-of-possession.
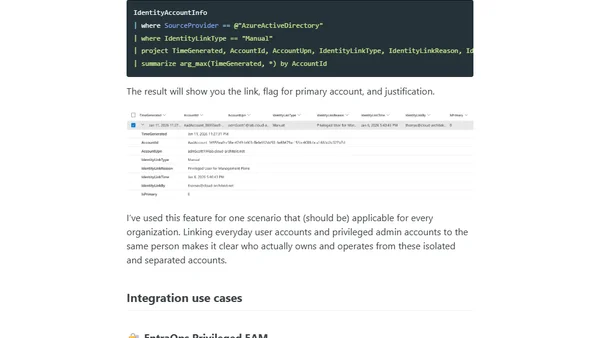
Explains how to link privileged accounts to user identities in Microsoft Defender for Identity to improve security visibility and incident response.
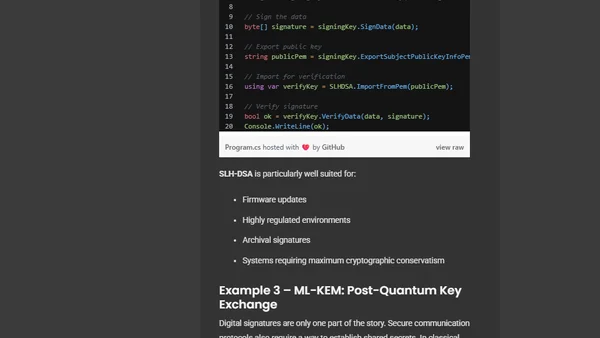
.NET 10 introduces built-in Post-Quantum Cryptography (PQC) APIs, enabling developers to adopt quantum-resistant algorithms for future security.
Anthropic invests $1.5 million in the Python Software Foundation to support Python ecosystem security and core development.
Anthropic invests $1.5 million in the Python Software Foundation to support Python ecosystem security and core development.
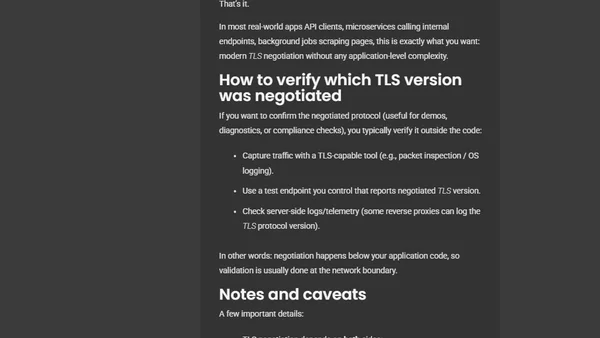
.NET 10 on macOS now automatically uses TLS 1.3 for HTTPS connections, improving security and performance without code changes.
A developer recounts debugging a PostgreSQL container stability issue that turned out to be a hidden security vulnerability, sharing lessons learned.

A developer's 2025 review: transitioning to a DevRel role at Pomerium, diving into security and AI agents via MCP, and giving numerous tech conference talks.
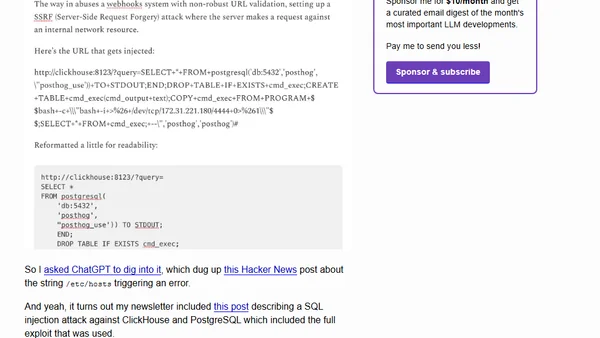
Author details how Substack's content filter blocked a newsletter containing a SQL injection exploit example, citing a 'Network error'.
Microsoft adds a new 'Microsoft 365 Support Engineer' role to Entra, but warns it's not for general use and is likely for internal or partner support.
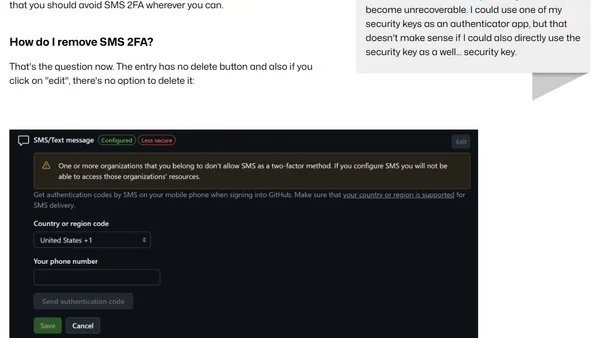
A developer details a frustrating bug in GitHub's 2FA system that prevents removing SMS authentication without adding an authenticator app first.
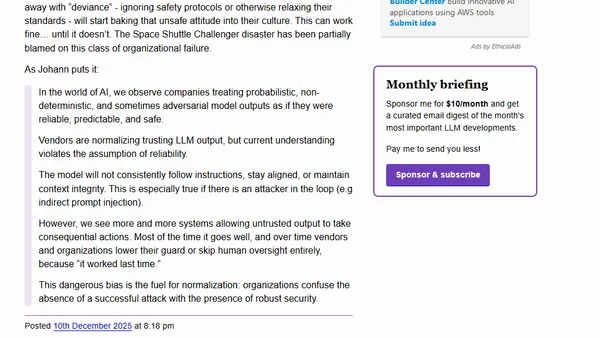
Explores the 'Normalization of Deviance' concept in AI safety, warning against complacency with LLM vulnerabilities like prompt injection.
Analysis of Microsoft's Secure Future Initiative report, emphasizing trust as a core architectural dimension and the risks of timing debt in hybrid infrastructure.
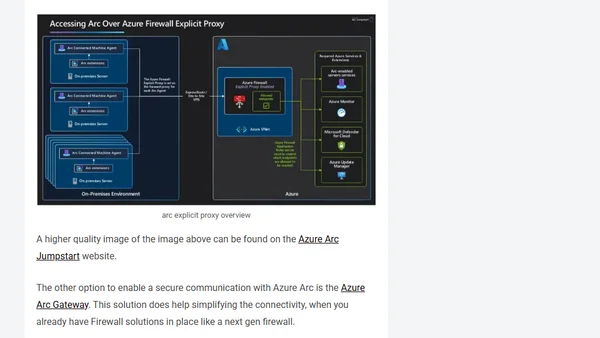
Explains why traditional ESAE security for Tier 0 assets is outdated and details a modern approach using Azure Arc with dedicated subscriptions and tightened controls.
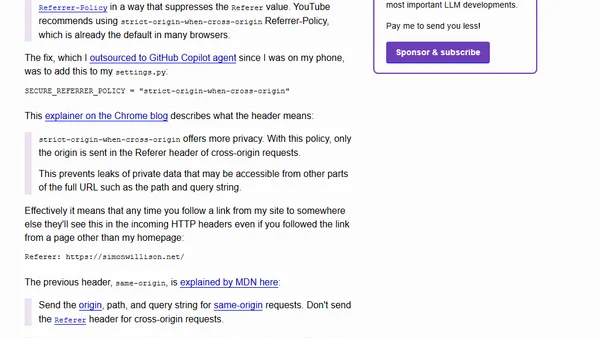
Fixing YouTube embed error 153 by adjusting Django's Referrer-Policy header from same-origin to strict-origin-when-cross-origin.
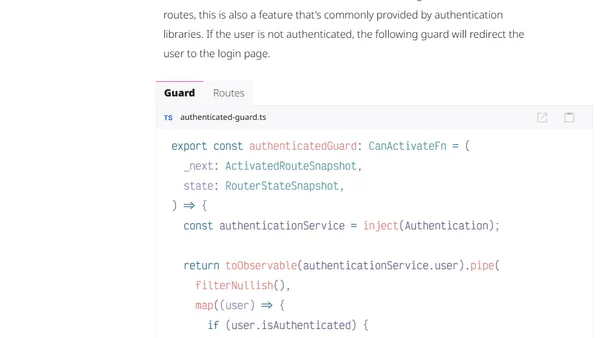
Explains how to implement secure cookie-based authentication in an Angular frontend, comparing it to the Authorization Code flow with PKCE.
Explains Docker Hub's new immutable tags feature, covering their benefits for reproducibility and how to configure them per repository.
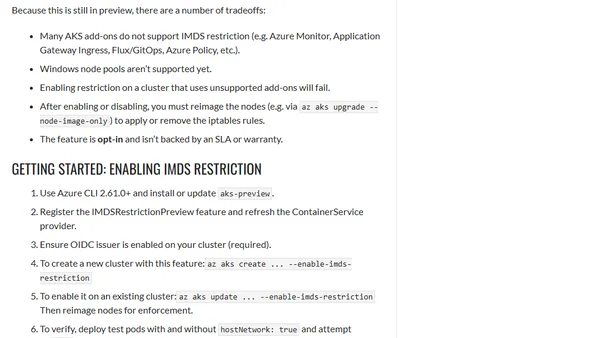
Microsoft introduces a preview feature for AKS to block pod access to the Azure Instance Metadata Service (IMDS), enhancing cluster security.

Analysis of a security attack exploiting toxic flows in the Model Context Protocol (MCP) to target Cursor IDE users via Jira tickets.
Introduces agent-rules, an open-source CLI tool that standardizes security and coding rules across AI coding assistants like GitHub Copilot and Cursor.