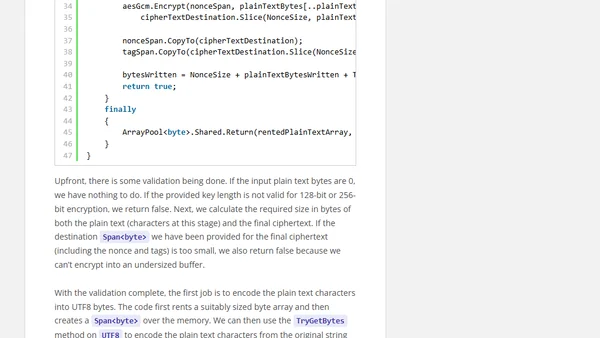
Encrypting Properties with System.Text.Json and a TypeInfoResolver Modifier (Part 2)
A technical guide on implementing AES-GCM encryption for property serialization using System.Text.Json in .NET.

A technical guide on implementing AES-GCM encryption for property serialization using System.Text.Json in .NET.
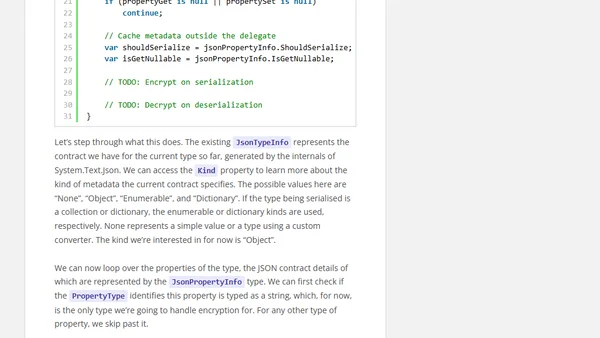
A technical guide on using System.Text.Json and TypeInfoResolver to automatically encrypt/decrypt sensitive properties during JSON serialization.
A daily roundup of links covering .NET, web development, AI, Python, DevOps, and other software engineering topics from January 8, 2026.
A developer's personal review and comparison of Ente, an end-to-end encrypted photo backup service, against alternatives like Amazon Photos and self-hosted options.
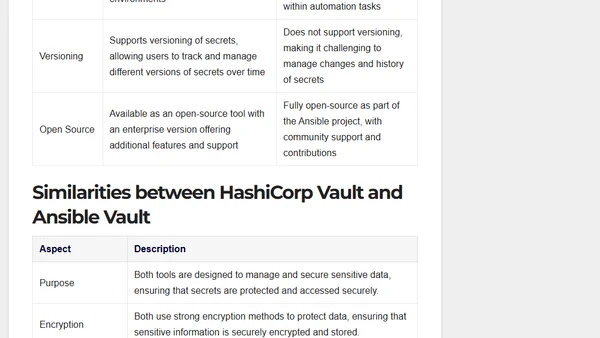
A detailed comparison of HashiCorp Vault and Ansible Vault for secrets management, covering features, use cases, and security.
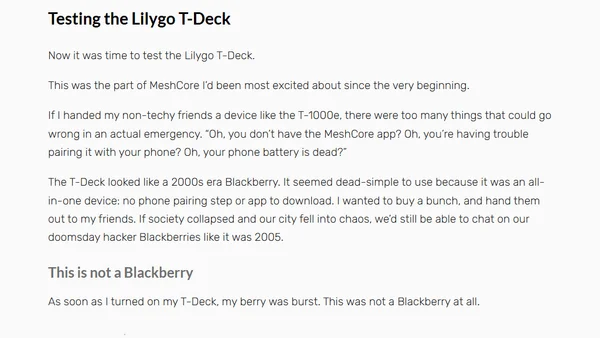
A personal review of MeshCore, an encrypted, off-grid mesh messaging system using LoRa radios for communication during emergencies.
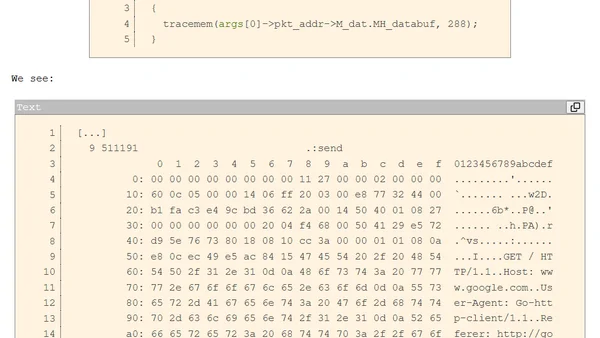
A technical guide on using DTrace to inspect encrypted and compressed network traffic in Go programs for debugging purposes.
Part 3 of a series on SQL Server security, covering auditing, encryption, and secure development practices for DBAs.
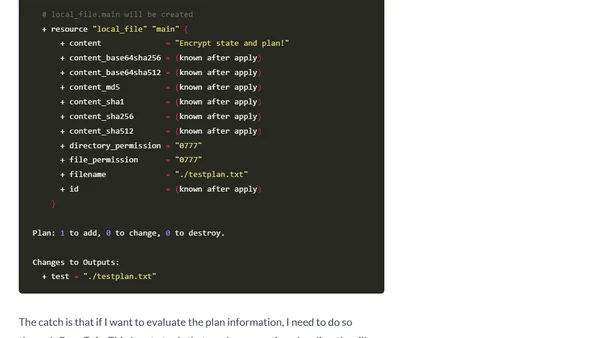
A guide to encrypting state data and plan files using the new encryption feature in OpenTofu 1.7, covering its purpose and implementation.
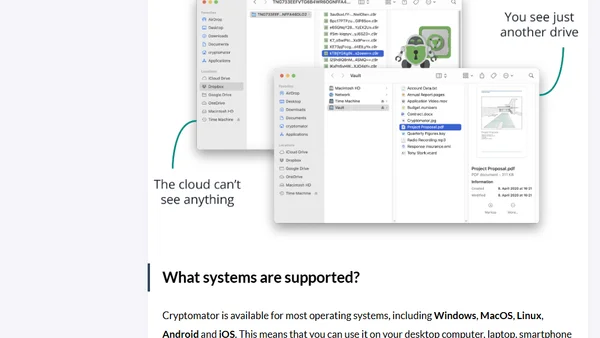
Explains how Cryptomator, a free open-source tool, provides end-to-end encryption for files stored in cloud services like Google Drive or Dropbox.
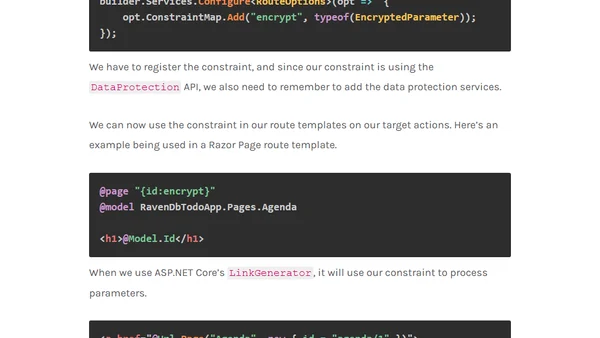
A guide to encrypting and decrypting sensitive identifiers in ASP.NET Core route parameters for improved security and data privacy.
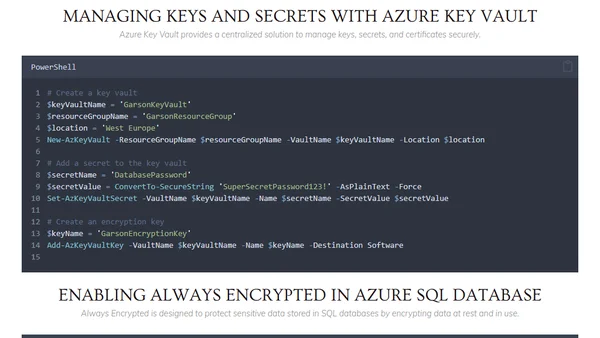
A guide to implementing encryption and data protection in Azure using PowerShell, covering Key Vault, TDE, Storage Encryption, and more.
An article explaining homomorphic encryption, a method for performing computations on encrypted data without decryption, with a practical example in R.
An overview of popular file encryption algorithms like AES, MD5, SHA-1, and SHA-2, explaining their uses and how to choose the right one for data security.
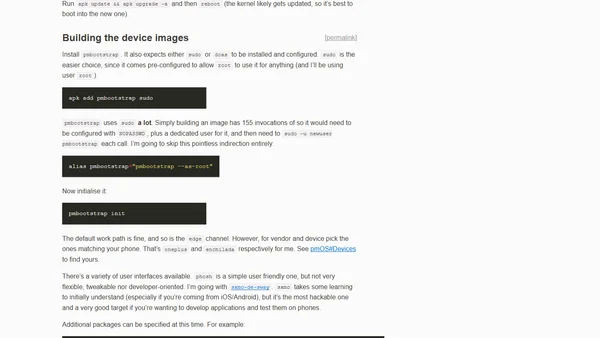
A technical guide detailing the process of installing postmarketOS with full-disk encryption on a OnePlus 6 smartphone.
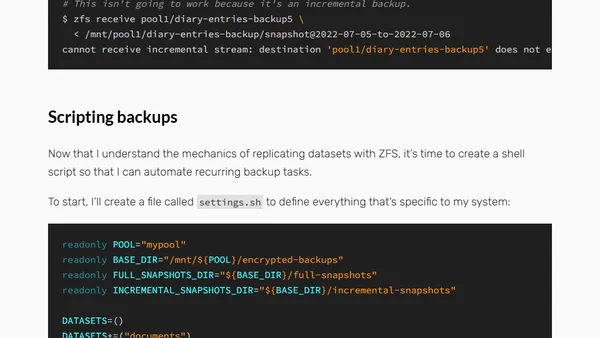
Guide to backing up encrypted ZFS datasets to cloud storage without unlocking them, using TrueNAS and custom scripts.
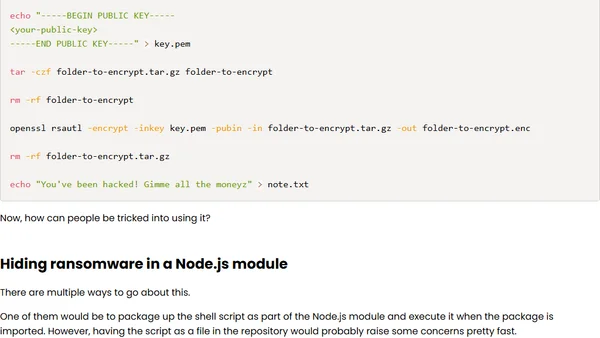
A technical analysis of how ransomware can be executed via a malicious Node.js module, written for educational awareness.
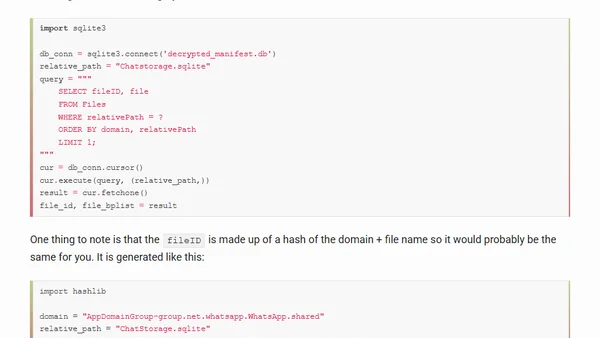
A technical guide on extracting and decrypting WhatsApp messages from a local iOS backup for data preservation.
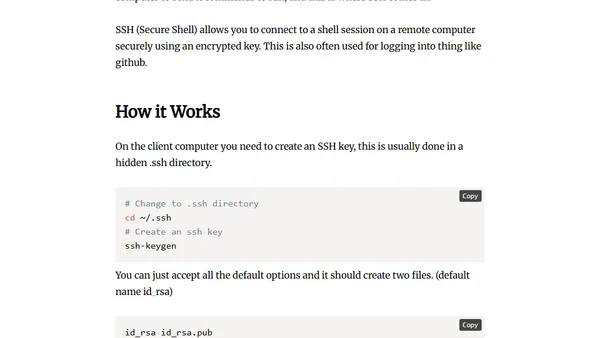
Explains SSH (Secure Shell), its purpose for secure remote computer connections, and how to generate and use SSH keys.
A critical analysis of the 4privacy Kickstarter project, examining its privacy promises, technology, and potential economic and trust challenges.