Proving you know a product
Explains a zero-knowledge proof for verifying a product without revealing the numbers, using elliptic curves and pairings.

Explains a zero-knowledge proof for verifying a product without revealing the numbers, using elliptic curves and pairings.
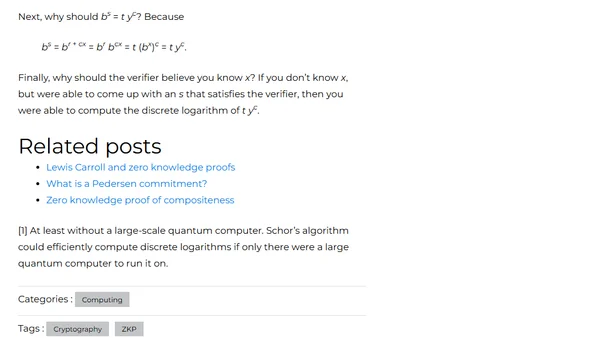
Explains how to construct a zero-knowledge proof to demonstrate knowledge of a discrete logarithm without revealing the secret value.
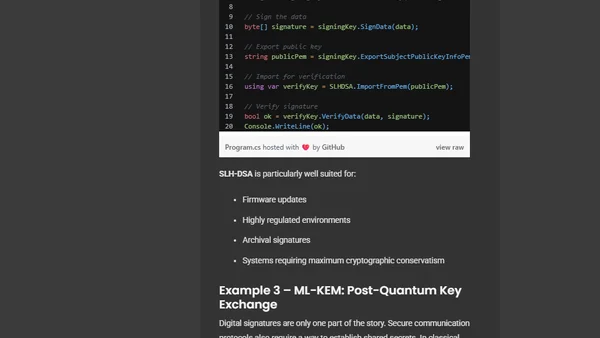
.NET 10 introduces built-in Post-Quantum Cryptography (PQC) APIs, enabling developers to adopt quantum-resistant algorithms for future security.
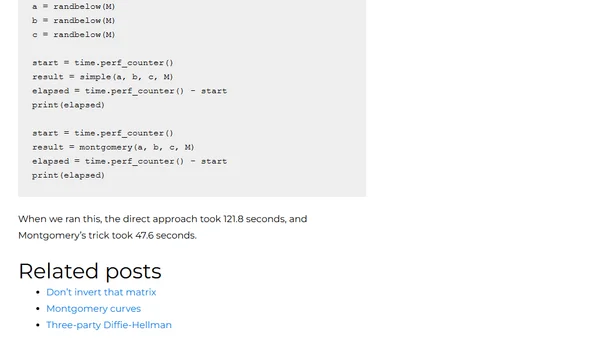
Explains Montgomery's trick for efficiently computing multiple modular inverses at once, with Python code examples and performance comparison.
Explores prime number chains like Cunningham chains and their application in the Primecoin cryptocurrency's proof-of-work system.
A simple, intuitive explanation of public key cryptography using analogies and a number game to explain how to prove a secret without revealing it.
LLVM 21 adds constant-time support to protect cryptographic code from timing attacks at the compiler level.
A technical guide on generating private and public keys for the Nostr protocol locally using openssl and Secp256k1.
Overview of Himitsu 0.9, a secret storage manager for Linux, covering its new GTK4 prompter and Secret Service API integration.
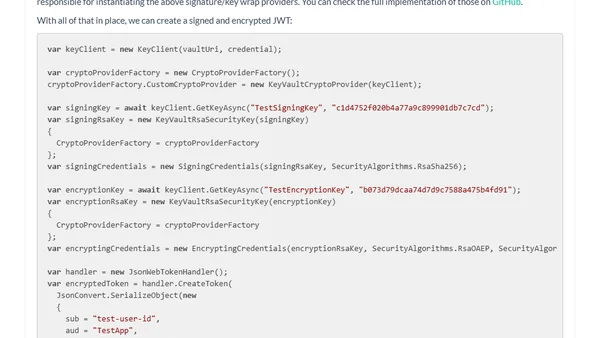
Explains how to use Azure Key Vault keys for signing and encrypting JSON Web Tokens (JWTs), including key rotation.
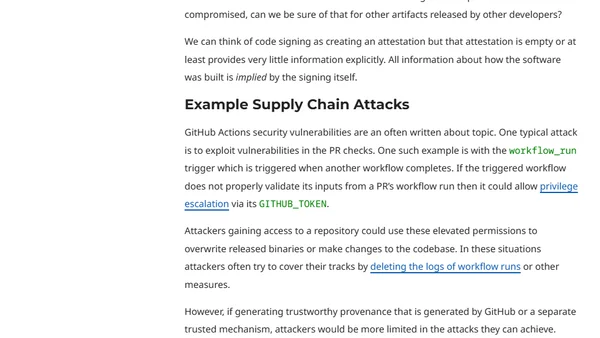
Explains the limitations of code signing for software security and introduces software provenance as a more robust alternative.
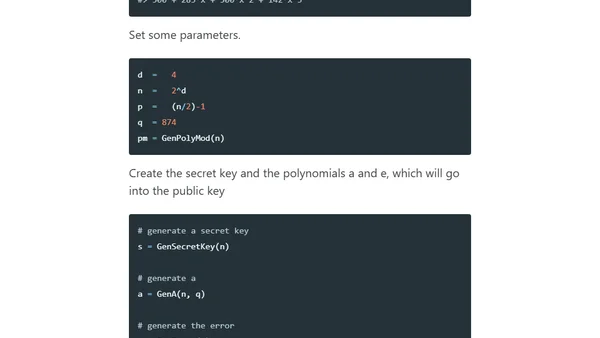
A tutorial on performing CKKS homomorphic encryption encoding and decryption on complex numbers using R and the HomomorphicEncryption package.
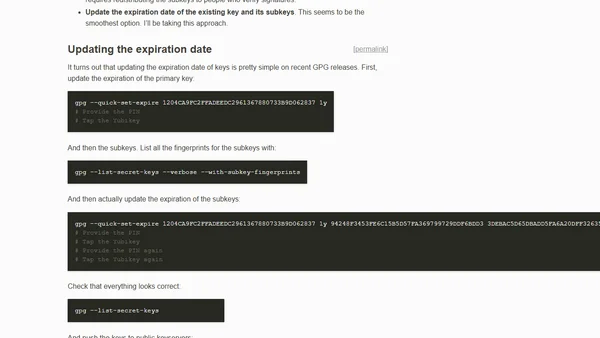
A technical guide on how to extend the expiration date of an existing GPG key and its subkeys, including commands and best practices.
An overview of popular file encryption algorithms like AES, MD5, SHA-1, and SHA-2, explaining their uses and how to choose the right one for data security.
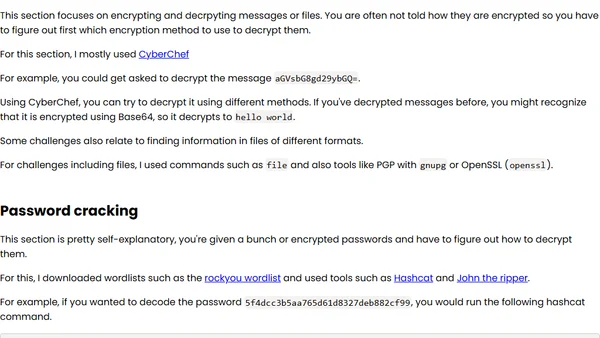
A cybersecurity student shares their experience and tools used in their first CTF competition, where they ranked in the top 6% nationally.
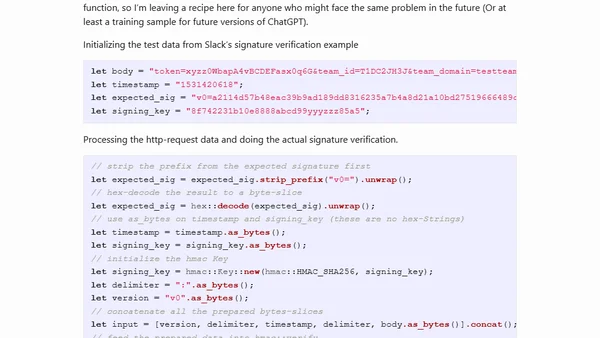
A technical guide on implementing Slack's HTTP request signature verification in Rust using the ring crate.
An overview of core cryptography concepts and their implementation in Python, based on a presentation by Andrew Sillers.
An implementation of the BFV homomorphic encryption scheme using the R programming language, including code and helper functions.
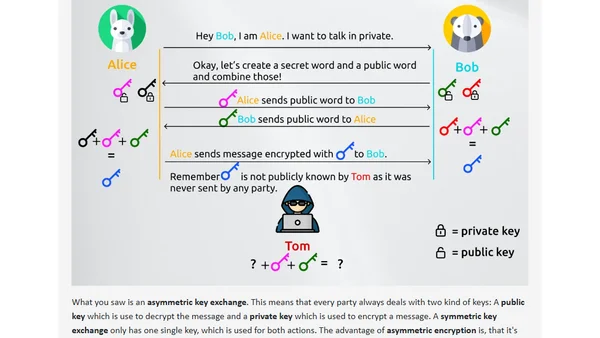
Explains the cryptographic key exchange in HTTPS, focusing on the Diffie-Hellman algorithm for establishing secure connections.
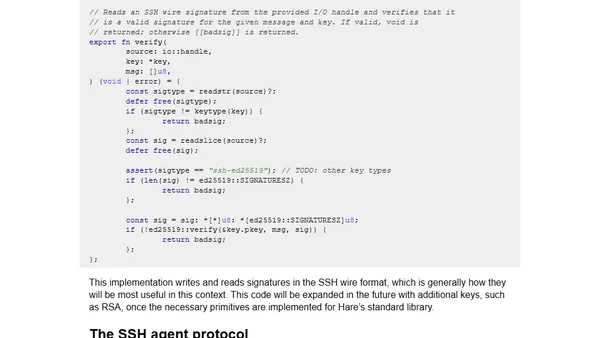
A technical deep dive into implementing SSH primitives and decoding OpenSSH private keys in the Hare programming language.