The worst truism in information security
Challenges the common security truism that defenders must be perfect, arguing for a more realistic, economics-based approach to defense.

Challenges the common security truism that defenders must be perfect, arguing for a more realistic, economics-based approach to defense.
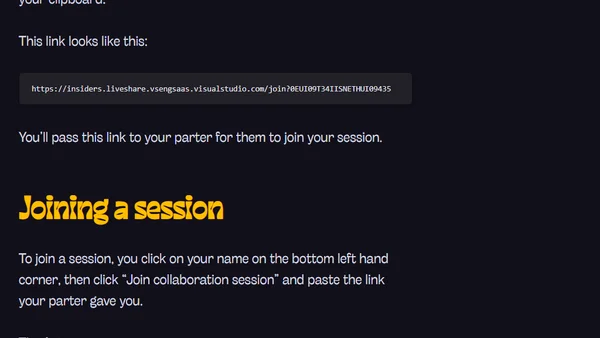
A tutorial on setting up and using Visual Studio Live Share for real-time collaborative coding sessions in VS Code.
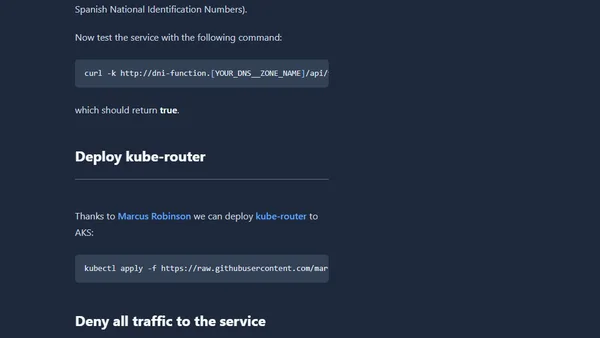
A guide to implementing and testing Kubernetes Network Policies on Azure Kubernetes Service (AKS) using the kube-router CNI plugin.
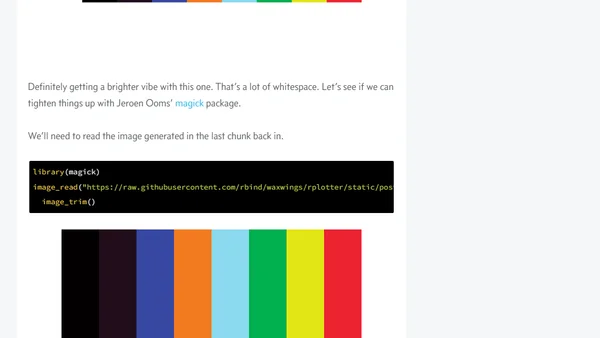
A technical tutorial on generating color palettes in R using various packages, inspired by movie posters and applied to Archer TV show artwork.
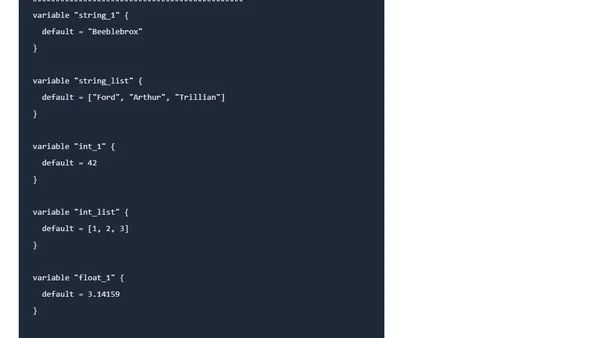
A technical guide explaining the formatlist() interpolation function in Terraform, including its syntax, usage examples, and practical applications.
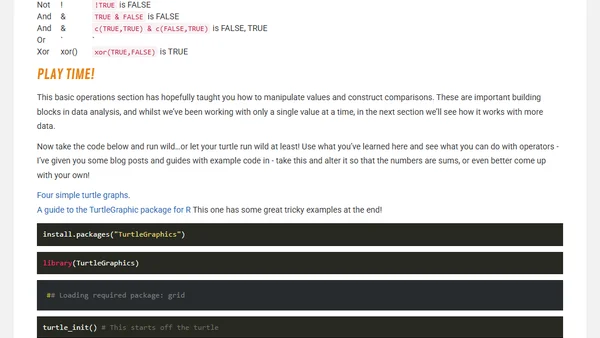
A tutorial on R programming basics, covering mathematical, comparison, and logical operators for data manipulation.
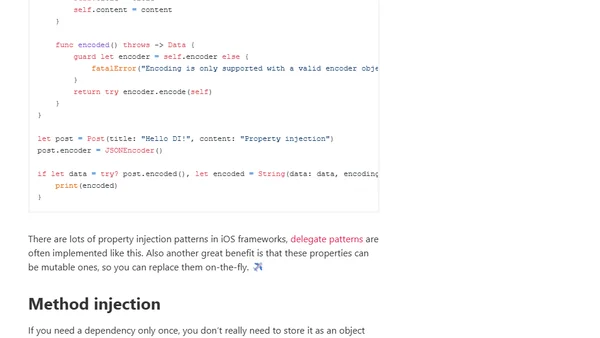
A tutorial explaining the Dependency Injection design pattern in Swift, covering its basics, variations, and implementation for writing loosely coupled code.
Explains security risks in the npm ecosystem, including malicious modules, typosquatting, and compromised contributors, with mitigation advice.
Explains the flexible but complex input handling system in the wlroots library for Wayland compositors and input abstraction.
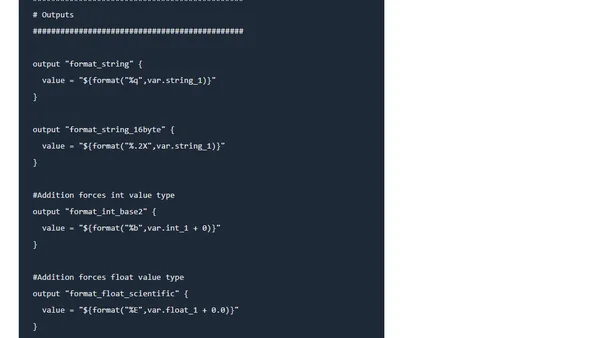
Explains the Terraform format() function, its syntax, and provides examples for formatting strings, integers, and floats.
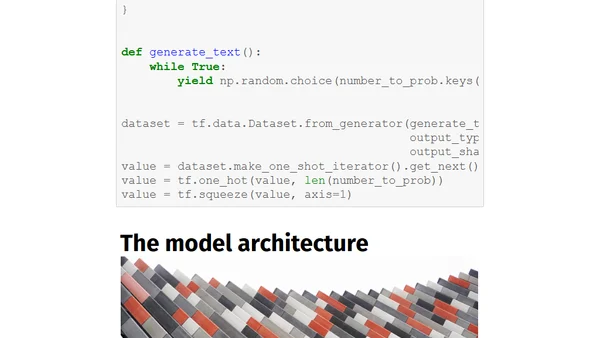
Explains the Gumbel-Softmax trick, a method for training neural networks that need to sample from discrete distributions, enabling gradient flow.
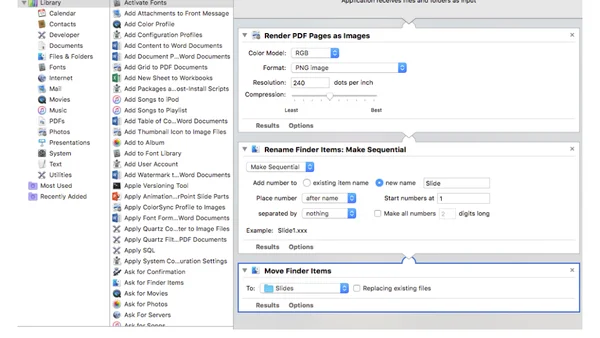
A guide to using Mac's Automator tool to batch convert PDF slides into images for video editing, saving significant time.
A developer's guide to automating image optimization, including compression, file naming, and directory structure for a static blog.
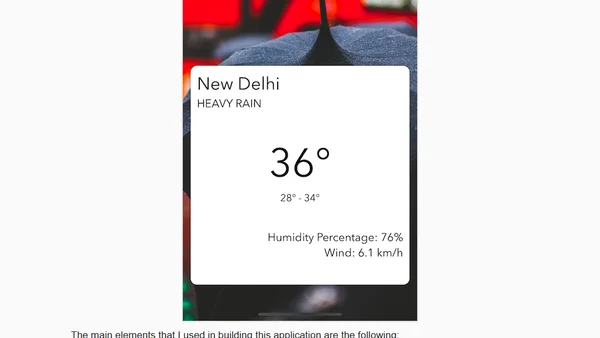
A developer shares their Week 2 progress learning React Native, covering project setup, ESLint configuration, and building a weather app with a third-party API.
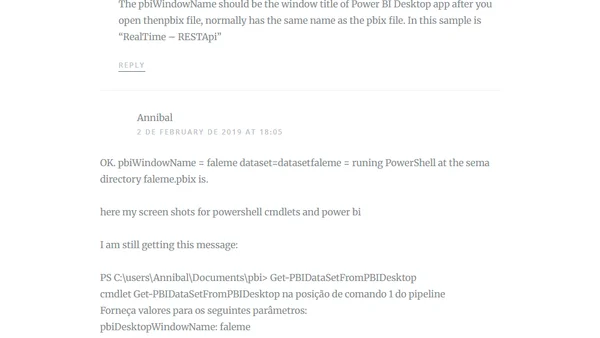
A guide on creating a Power BI Push Dataset using Power BI Desktop and the PowerBIPS.Tools module to simplify API dataset creation.
Troubleshooting guide for resolving email alert failures in vCenter Server Appliance 6.5 due to a sendmail configuration issue.
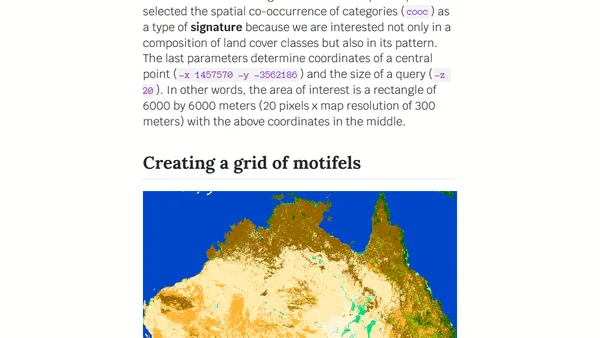
A technical tutorial on using GeoPAT 2 software to find geographically similar landscapes through pattern-based spatial analysis.
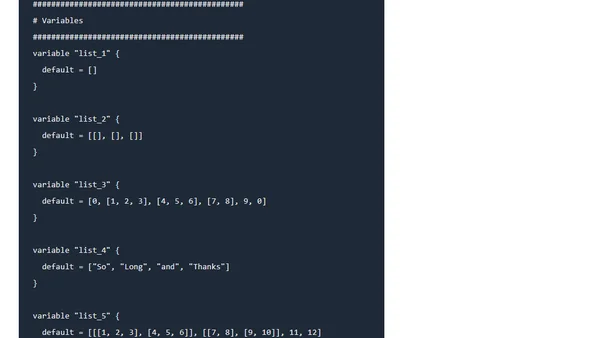
A technical guide explaining the flatten() interpolation function in Terraform, including its syntax, use cases, and examples.

Article argues engineers should focus on understanding user problems, not just building solutions, to create impactful products.
Explains a key security change in ASP.NET Core 2.1 where authorization filters are combined, altering authentication and role-checking behavior.