Installing a Laravel app on Heroku
A step-by-step guide to deploying a Laravel application on Heroku, covering setup, configuration, and deployment.

A step-by-step guide to deploying a Laravel application on Heroku, covering setup, configuration, and deployment.
A developer's post-mortem on an unfinished game, 'Mining Incorporated', created for the Ludum Dare 48-hour game jam.
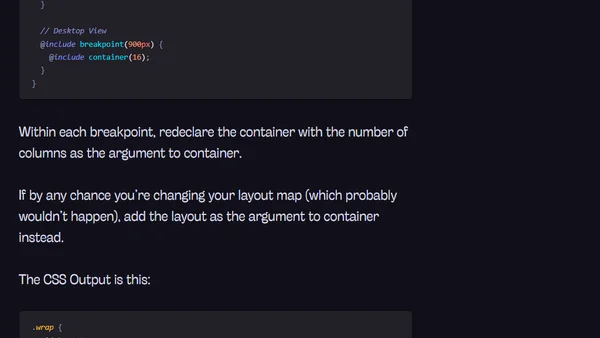
A tutorial on configuring and using static grids with the Susy 2 CSS layout framework, including responsive breakpoints.
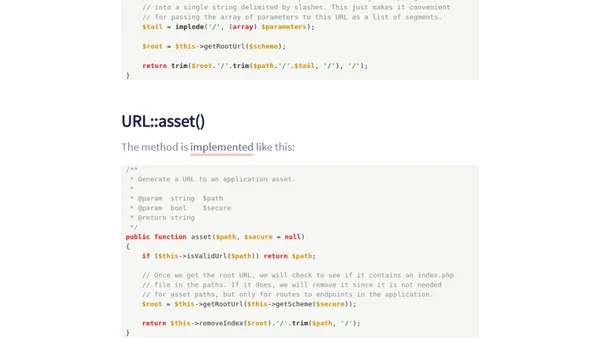
Explains the technical differences between Laravel's URL::to() and URL::asset() methods for generating URLs, including performance and use cases.
A developer's early morning start on Ludum Dare 29, detailing initial coding progress and challenges with a game prototype.
A developer's entry for the Ludum Dare 29 game jam, detailing their tech stack and preparation using C++ and SFML.
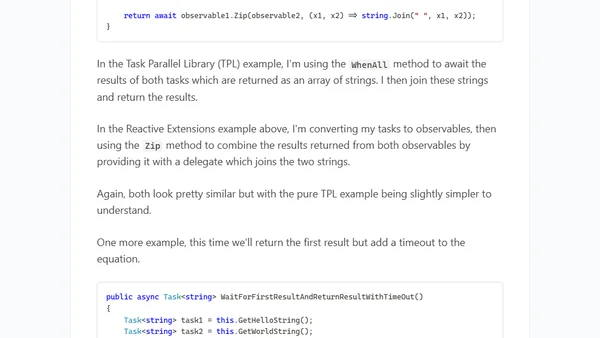
Explains how to convert C# Tasks into Observables using Rx's ToObservable method, with a practical example comparing it to Task Parallel Library.
A developer recounts leading a team at the NASA Space Apps hackathon, focusing on preparation and iterative development to build an asteroid mining game.
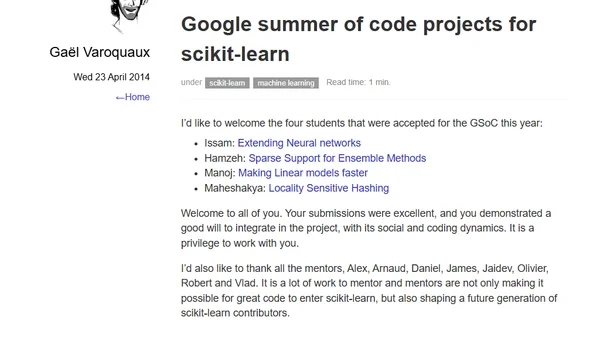
Announcing the four students accepted for Google Summer of Code 2024 to work on scikit-learn projects, including neural networks and performance improvements.
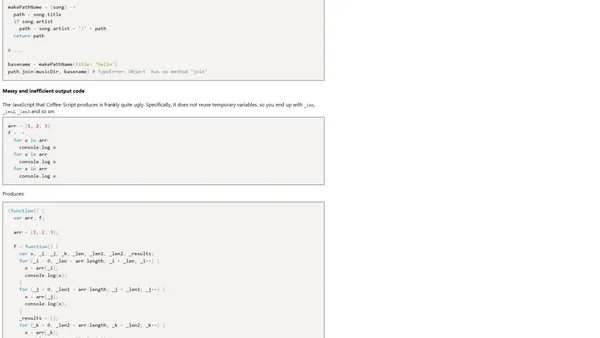
A developer's journey building a custom music player, detailing technical challenges, loudness compensation, and lessons from Amarok 1.4.

The author renames the open-source project TYPO3-Analytics to 'Jacobine', explaining the naming process and its personal significance.
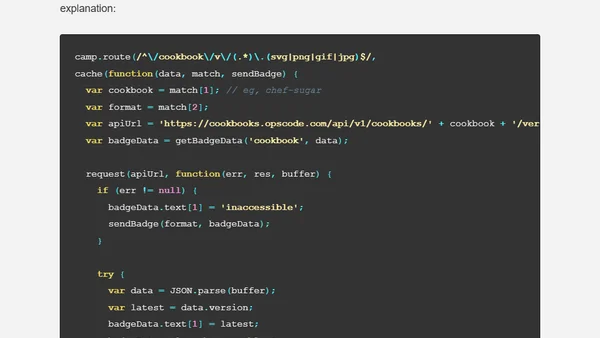
A developer's journey to add Chef cookbook badges to the Shields.io service, addressing inconsistent badge design and lack of cookbook support.
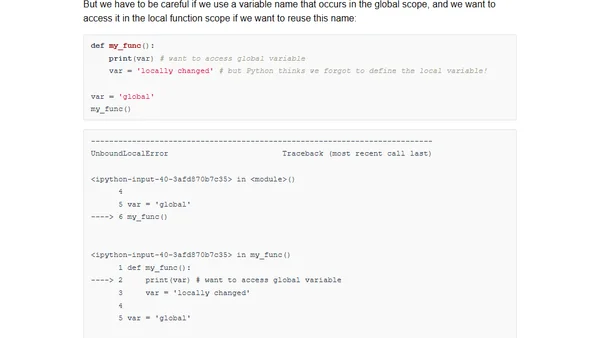
An in-depth exploration of Python's advanced features, quirks, and common pitfalls for experienced developers.
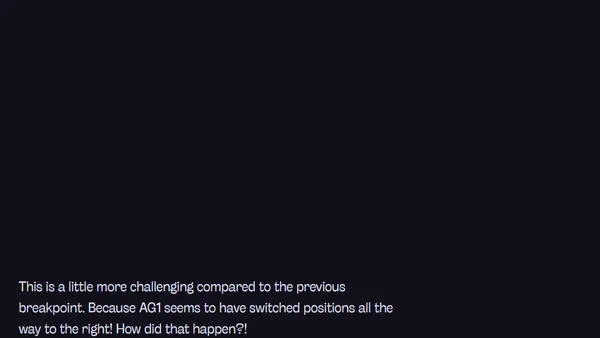
A deep dive tutorial on using Susy 2 and the Breakpoint gem to create responsive website layouts with Sass.
A blogger clarifies that Skype's unencrypted local database is not a security vulnerability, as it's protected by system-level access controls.
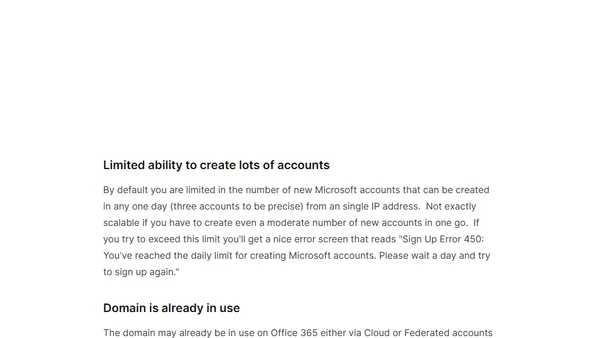
Explains SharePoint Online's Partner Access License (PAL) for inviting external users without an O365 license, covering setup and key recommendations.
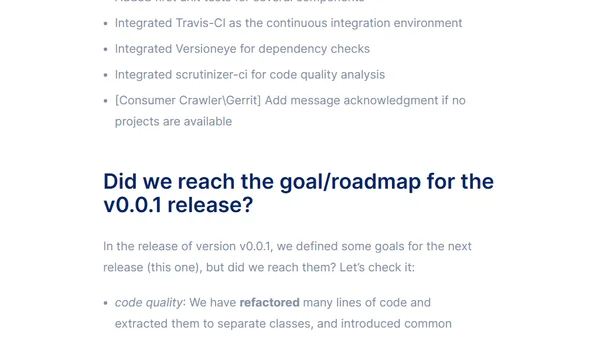
Announcement of TYPO3-Analytics v0.1.0 release, detailing new features, enhancements, and bug fixes for the open-source analytics tool.
A security analysis revealing that Skype stores user data in an unencrypted, password-less local database, making it vulnerable to data extraction.

A PyCon 2014 attendee reflects on the community spirit of swag bag stuffing and the technical depth of an open space session on software composition.
Explains the advantages of vectorization in R for writing faster, simpler, and safer code by examining how R works internally.