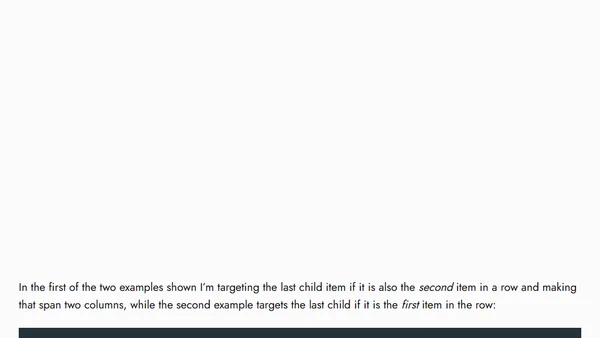
Controlling Leftover Grid Items with Pseudo-selectors
A CSS Grid tutorial on using pseudo-selectors to control the layout of leftover items (widows) in a grid, comparing it to flexbox solutions.

A CSS Grid tutorial on using pseudo-selectors to control the layout of leftover items (widows) in a grid, comparing it to flexbox solutions.
A guide to building a polite web crawler that respects robots.txt, manages crawl frequency, and avoids overloading servers, with an example in .NET.
Explores strategies and challenges for orchestrating micro-frontends, comparing client-side, server-side, and edge-side approaches.
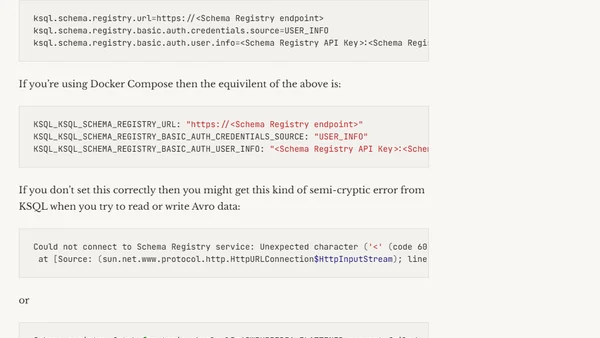
Guide on configuring KSQL to connect to a secured Confluent Cloud Schema Registry, including Docker setup and error troubleshooting.
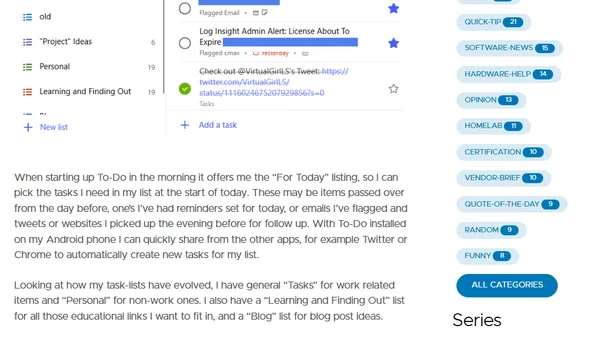
A personal review of Microsoft To-Do, detailing its features like My Day and how it's used to manage both work and personal tasks.

A conference talk exploring .NET memory management concepts, the Garbage Collector, hidden allocations, and profiling techniques.

Analyzes different methods for calling assertions in PHPUnit, comparing their popularity and performance.
Guide to enabling TLS 1.2 support in legacy .NET applications without recompilation, using configuration file updates.
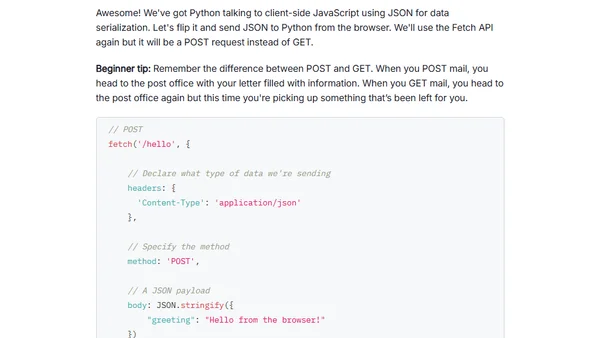
Explains how to pass data between JavaScript and Python using JSON serialization and AJAX requests with the Fetch API and Flask.
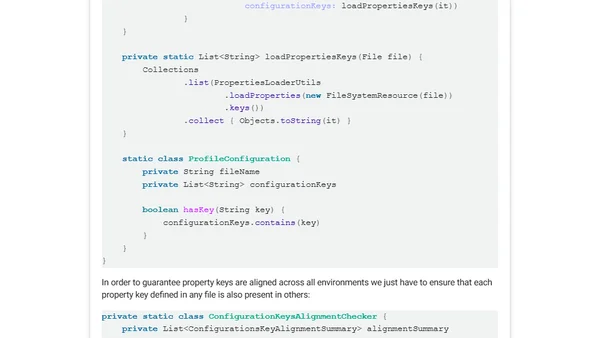
A developer explains the risks of using default property values in Spring configuration and advocates for dedicated environment profiles to prevent misconfigurations.
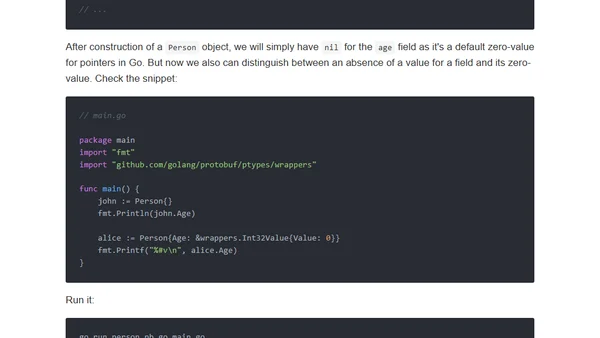
Explains how to implement truly optional scalar fields in Protocol Buffers 3 using wrapper types, with practical Go examples.
A personal review and analysis of the 'Revolution OS' film, exploring the history and impact of the GNU project and the Free & Open Source Software movement.
A student shares a portfolio of their university art projects, including generative code art, a metadata website, and social commentary pieces.
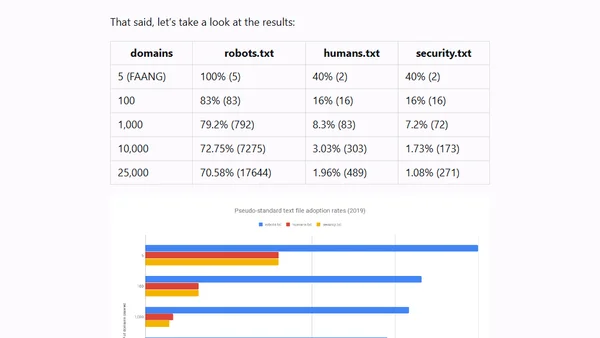
Analysis of adoption rates for robots.txt, humans.txt, and security.txt files across the top 25,000 websites, including methodology and results.
Blog author offers free 45-minute one-on-one R training sessions to 10 people, focusing on data analysis, visualization, and package development.
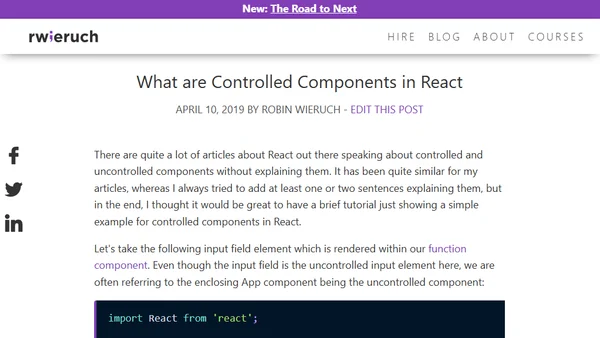
A tutorial explaining the difference between controlled and uncontrolled components in React with practical code examples.
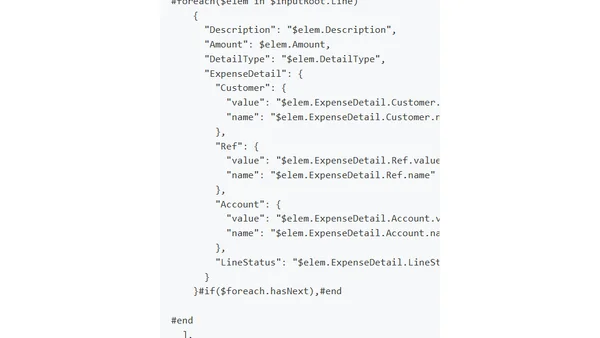
A comprehensive guide to understanding the components and request lifecycle of AWS API Gateway for building serverless applications.
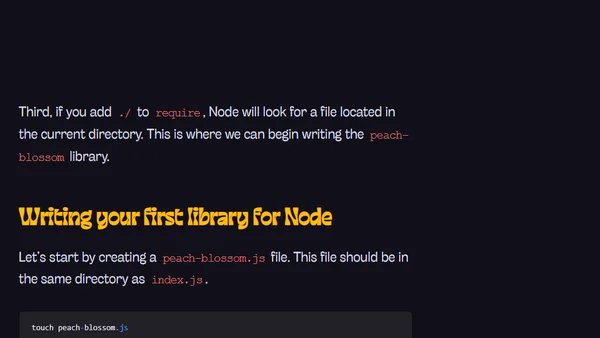
A guide to writing and publishing JavaScript packages that work in both browser and Node.js environments, covering module patterns and setup.
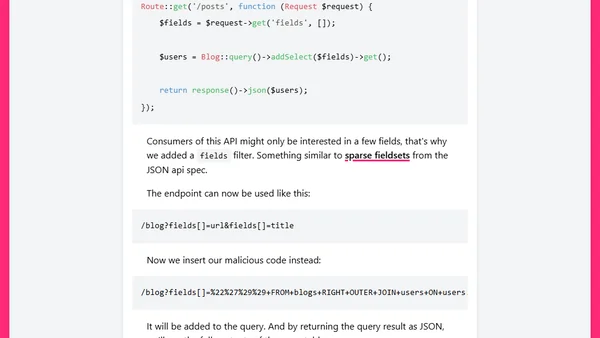
Explains SQL injection risks in Laravel's query builder, focusing on unsafe functions like addSelect and JSON shorthand, with a fixed vulnerability example.
Analyzes technical and market challenges hindering widespread adoption of security keys, focusing on iOS limitations and API fragmentation.