Achtung! Decentralize, decentralize, decentralize!
Argues for decentralized, open-source social platforms as the solution to privacy exploitation by centralized tech giants like Facebook and Google.

Argues for decentralized, open-source social platforms as the solution to privacy exploitation by centralized tech giants like Facebook and Google.
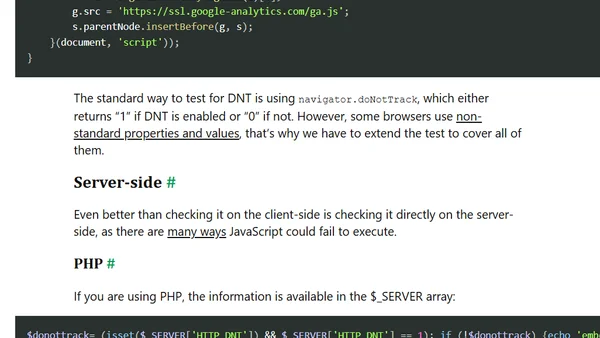
A technical guide on implementing Do Not Track (DNT) support for websites, covering both client-side and server-side checks.
A review of Kevin Mitnick's book 'The Art of Invisibility', which explores digital privacy threats and practical protection strategies for everyone.

Argues against abandoning Firefox over recent controversies, comparing privacy implications of switching to Chrome/Chromium or using forks.
A critique of Mozilla's recent decisions to include ads and sponsored content in Firefox, arguing it violates user trust and the browser's core purpose.

Introducing Black Out, a macOS app for easily redacting sensitive information and removing metadata from images before sharing online.
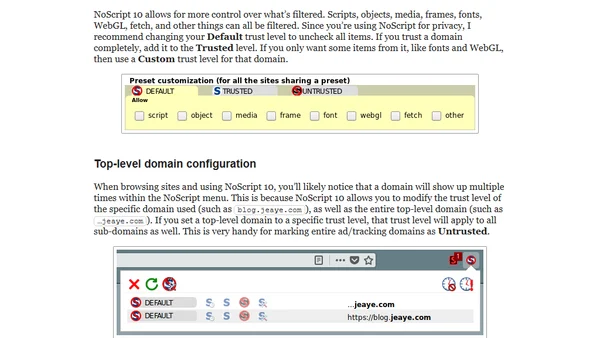
A guide to using NoScript 10.x in Firefox, covering its new UI, trust levels, and configuration for privacy and security.
The article critiques the use of SSNs as both a secret and a universal ID, arguing it's a core problem behind data breaches like Equifax.
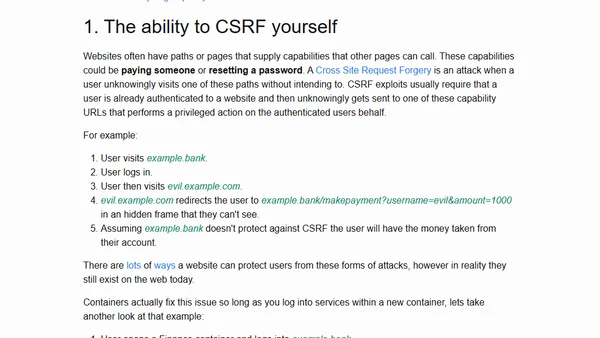
Mozilla introduces website assignment for Firefox Containers, allowing users to automatically open specific sites in isolated containers for enhanced privacy.
A developer details their journey to replace Google services with self-hosted alternatives for email, YouTube, and music, focusing on privacy and customization.
A guide to enhancing network security and privacy on macOS, covering ISP choice, browser extensions, and search engine alternatives.
A personal reflection on the trade-offs between convenience and privacy in an era of AI, IoT, and pervasive data collection.
Discusses the inevitability of website breaches, lists major hacks, and explains how to assess your risk and prepare for security incidents.
A software engineer's critique of Windows 10, focusing on bloatware, privacy concerns, and the inferiority of its command-line tools compared to Linux.
A guide to using the Tor network for enhanced online privacy, covering applications beyond web browsing and practical setup tips.
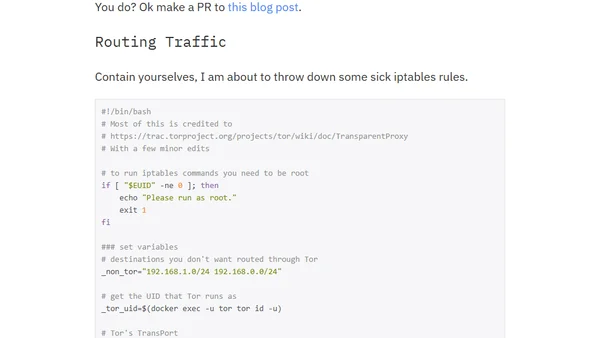
A technical guide explaining how to route all host traffic through a Tor Docker container using iptables rules.
Analyzes the TV show Continuum to discuss real-world surveillance, IoT security risks, and the erosion of privacy in a connected world.
Former Mozilla CEO discusses the 'network problem' of user data, privacy, and economic value, proposing solutions post-resignation.
Analysis of the Lavabit case, focusing on government overreach and Fourth Amendment violations in demanding encryption keys.
A 2013 Facebook bug leaked 6 million users' contact info, revealing the platform collects data from friends' contacts without user consent.