DUM-E and U
Explores building real-world robotic arms like Tony Stark's DUM-E using ROS and machine learning for automated tasks.
Jessie Frazelle is a technologist and author specializing in hardware, software, and data center technologies. She writes about chip design, mechanical CAD, energy systems, 3D printing, and security in computing.
67 articles from this blog

Explores building real-world robotic arms like Tony Stark's DUM-E using ROS and machine learning for automated tasks.
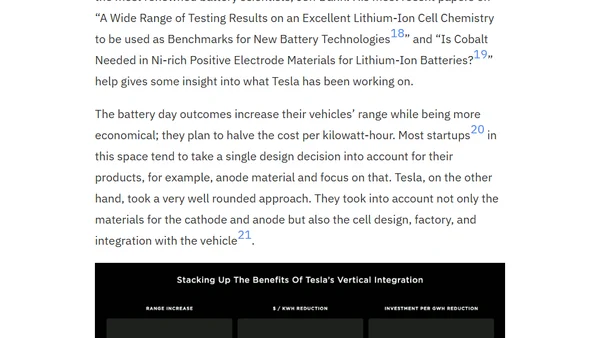
An analysis of Tesla's Battery Day event, explaining the fundamental chemistry and physics of how batteries work.
A technical deep dive into automating internal infrastructure and data workflows using Rust, cron jobs, and a central database.
A technical comparison of FDM and SLA 3D printing processes, including the author's personal experience and research into additive manufacturing.
A developer discusses the importance of computer specs, criticizing cheap Windows machines with low RAM and advocating for better hardware.
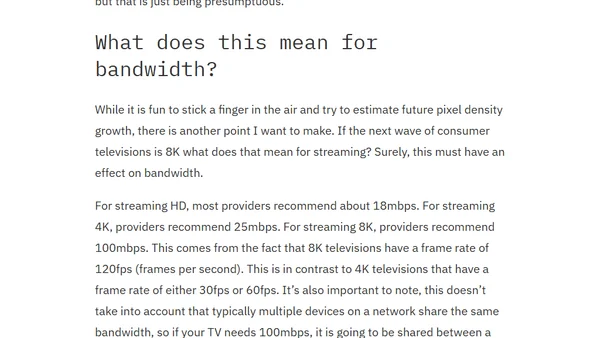
Explores the evolution of TV resolution from SD to 8K and questions the availability of high-bandwidth internet needed for such advanced content.
A programmer explores the philosophy and practical benefits of automation, sharing personal examples and discussing tools like Apple Shortcuts and IFTTT.
A historical journey through data storage mediums, from punch cards to modern DRAM, explaining how a single byte is represented.

Explains the environmental impact of data centers, comparing carbon neutral, net zero, and carbon negative goals of major tech companies.

A developer details setting up a high-performance office network using UniFi equipment, including switches, APs, and an isolated Wi-Fi 6 network.
Announcing the founding of Oxide Computer Company, aiming to bring hyperscale-like infrastructure to on-premises data centers.
A developer's experience at the Open Source Firmware Conference hackathon, detailing the process of flashing OpenBMC onto a Supermicro server board.
Explores transactional memory concepts like Intel's TSX, comparing deadlocks vs. livelocks, and discusses security implications like Spectre/Meltdown.
A guide explaining Kubernetes' challenges for business leaders, focusing on stateful data risks and security pitfalls.
A programmer's enthusiastic foreword for a book on using BPF and XDP for advanced Linux observability, tracing, and networking.
Explains the security risks of proprietary firmware in deep system privilege levels (Rings -2 & -3) and advocates for open source alternatives.
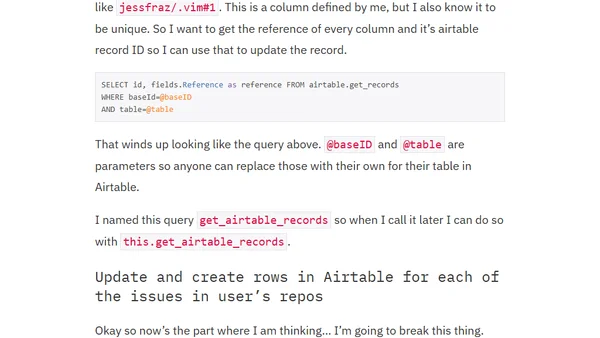
A developer explores Transposit, a platform providing a SQL interface to interact with multiple APIs, and attempts to rebuild a complex GitHub bot using it.
A developer's critical questions for evaluating cloud providers, focusing on problem-solving, security implementation, and customer-driven development.
Applying software CI principles to leadership, proposing a 'Leadership CI' framework of reflective questions for better decision-making.
A developer explores investigative journalism, drawing parallels between source control diffs and uncovering truth in legal documents and online comments.