The need for slimmer containers
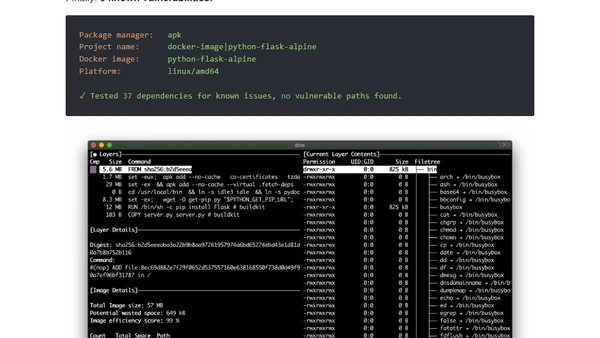
Discusses the importance of using smaller, secure container images, analyzing vulnerability scans and trade-offs between Alpine and Debian-based images.

Discusses the importance of using smaller, secure container images, analyzing vulnerability scans and trade-offs between Alpine and Debian-based images.
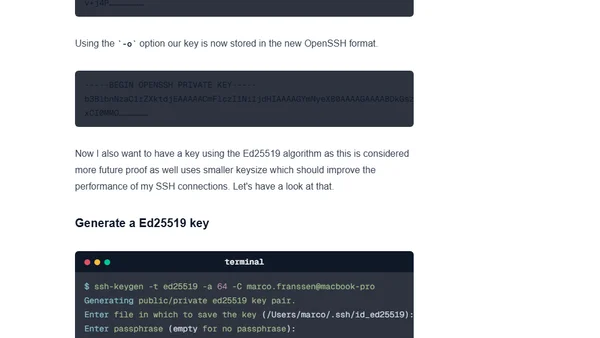
A technical guide comparing SSH key algorithms (RSA, ECDSA, Ed25519) and providing recommendations for generating secure keys in a DevOps context.
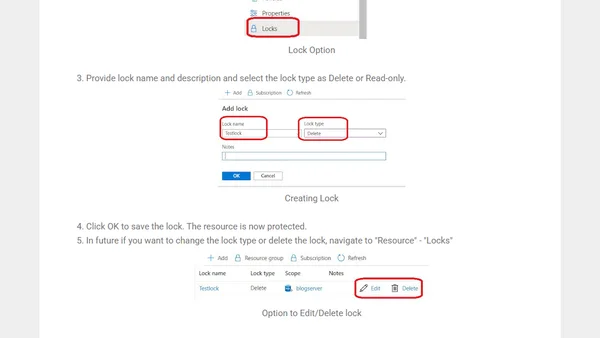
Explains Azure Resource Locks, their types (CanNotDelete/ReadOnly), and how to apply them via the Azure Portal to prevent accidental deletion or modification.
A developer argues that cryptocurrency has caused widespread abuse of free CI services and damaged trust in the software industry.
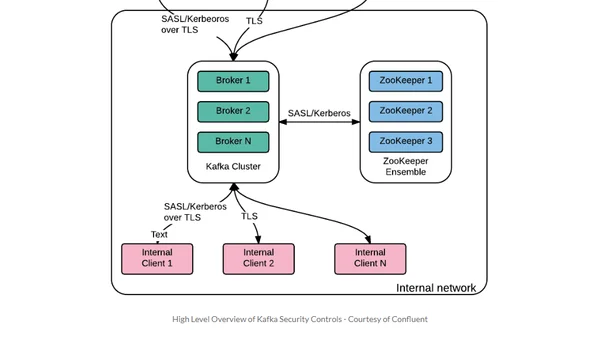
A guide for security professionals to understand Apache Kafka basics and its security features within the Kubernetes ecosystem.
A developer recounts a critical security bug in a custom-built framework, arguing against writing your own framework for client projects.
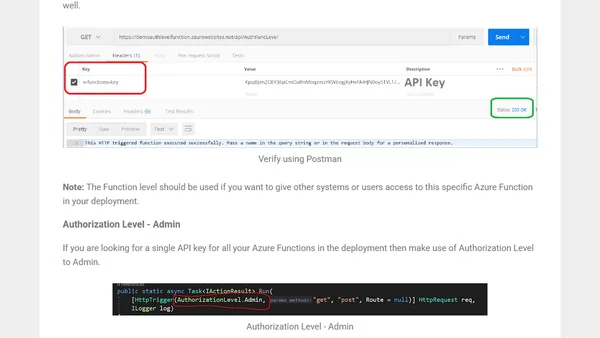
A guide to securing Azure Functions using API keys, covering different authorization levels and practical verification with Postman.
A live coding session on debugging browser tools and XSS mitigation while fixing an issue to render HTML tags as text.
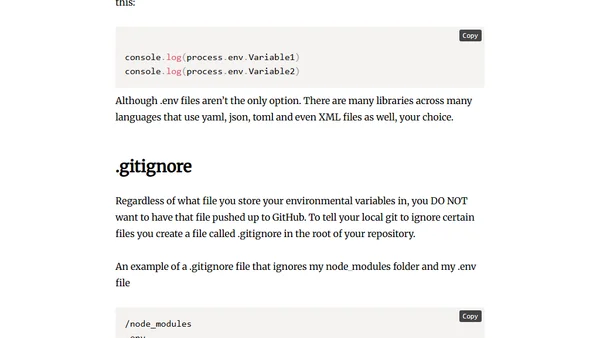
A guide on using environment variables in React to securely manage sensitive data like API keys and database credentials.
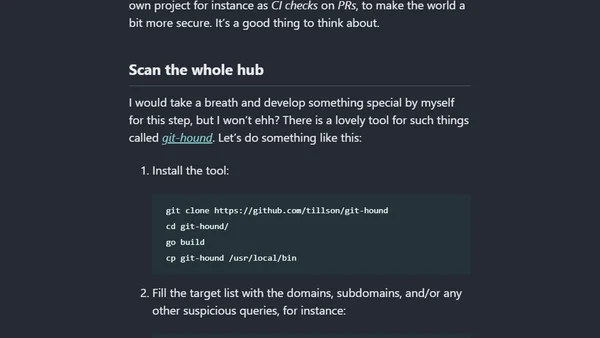
A technical guide on using tools like gitleaks, earlybird, and git-hound to find security leaks and exposed secrets in code repositories.
OpenIddict 3.0, a .NET OpenID Connect server and validation library, is now generally available with a rewritten, event-oriented architecture.
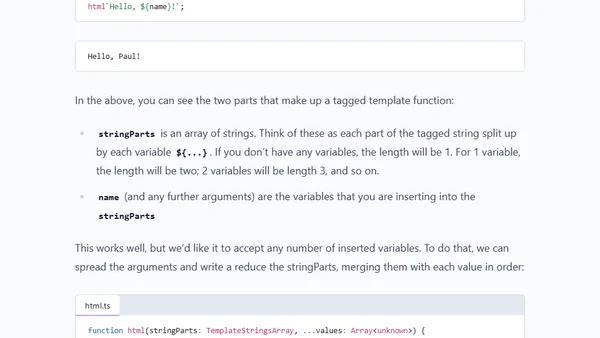
Explains how to safely generate HTML responses in Express.js without a templating engine, focusing on preventing XSS attacks.
Let's Encrypt's root certificate change may cause website trust issues for older Android devices, affecting millions of users globally.
A guide to implementing secret scanning with GitLeaks in Azure DevOps pipelines to prevent accidental exposure of API keys and passwords in code repositories.
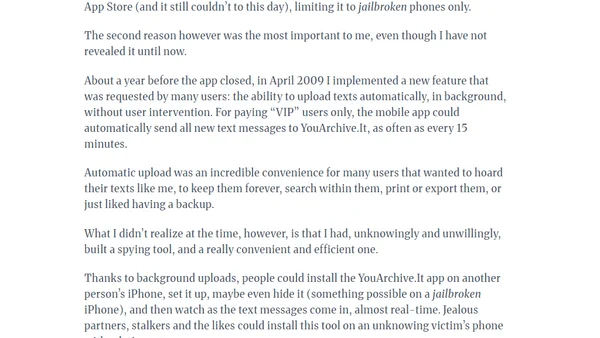
A developer recounts accidentally creating a spying app as a teenager while trying to solve the iPhone's 1000-SMS limit, exploring early mobile hacking.
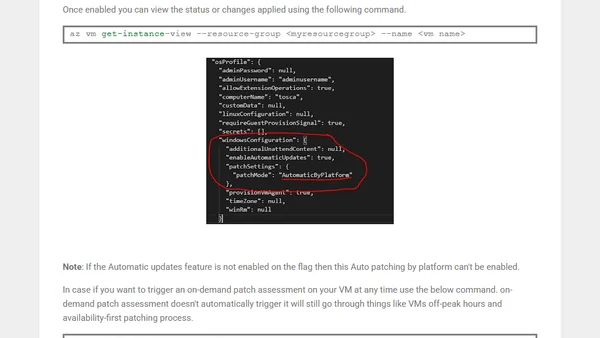
Guide to enabling Automatic Guest OS Patching for Windows Azure VMs, a public preview feature for automated security updates.

A threat modeling case study using bicycle theft to illustrate security principles applicable to IT systems.
A guide on using the Terminal command `spctl` to verify if a macOS application has been notarized by Apple.
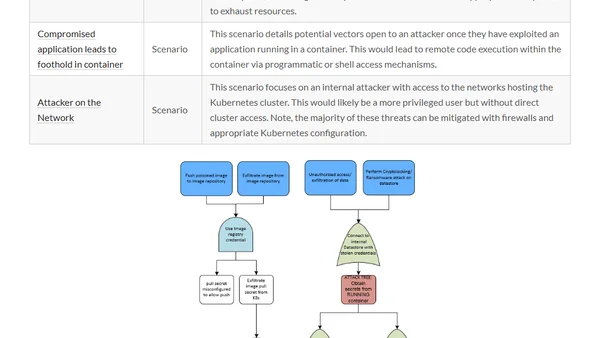
A summary of three major Kubernetes threat modeling initiatives to help security professionals secure their production clusters.
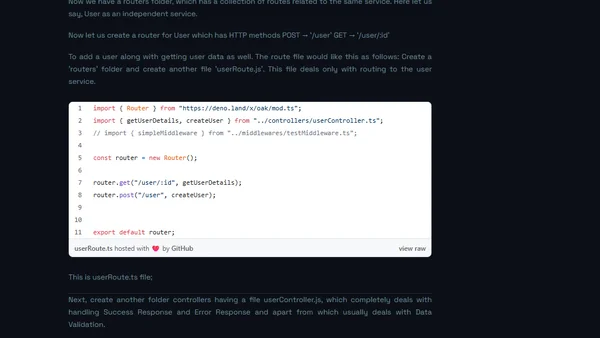
A technical analysis comparing Deno and Node.js, focusing on Deno's design improvements like security, URL imports, and eliminating node_modules.