IdentityServer and Signing Key Rotation
Explains the process and importance of rotating signing keys in IdentityServer for security, detailing the use of AddSigningCredential and AddValidationKey.

Explains the process and importance of rotating signing keys in IdentityServer for security, detailing the use of AddSigningCredential and AddValidationKey.
Explains security risks and best practices for managing user permissions in Django's admin interface to prevent data leaks.
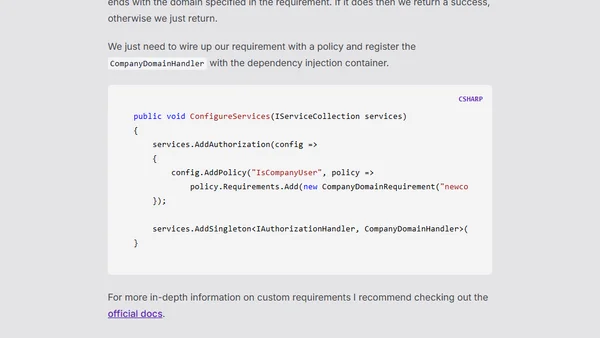
A guide to implementing policy-based authorization in Blazor applications, covering setup, advantages over role-based auth, and custom requirements.
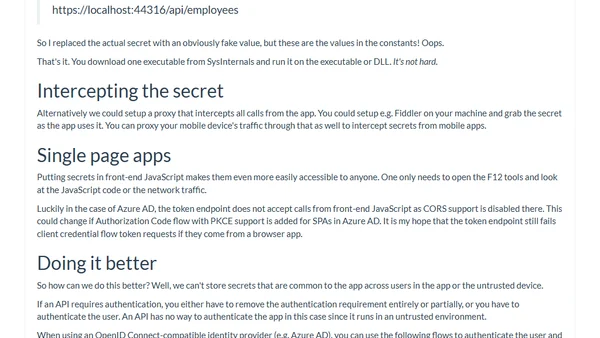
Explains why embedding secrets like API keys in native apps is a critical security flaw, with a practical demonstration.
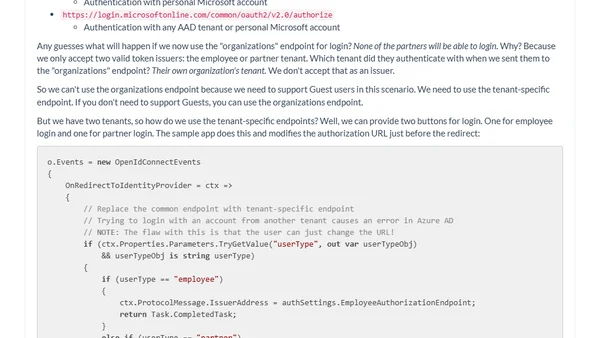
Explains best practices for building secure multi-tenant Azure AD applications that restrict login to a specific set of known tenants.
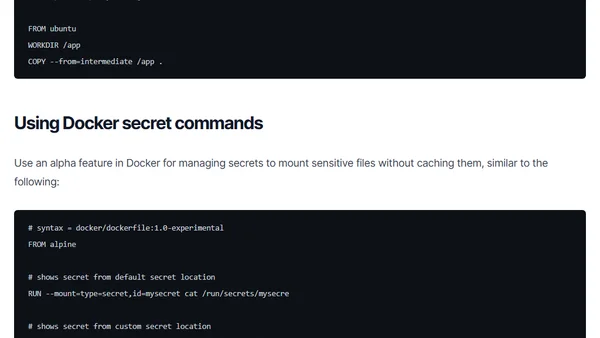
Learn how to prevent secrets like SSH keys and API tokens from being leaked into your final Docker images using multi-stage builds and secrets management.
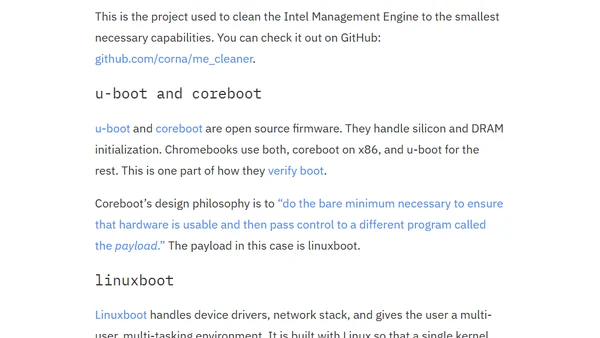
Explains the security risks of proprietary firmware in deep system privilege levels (Rings -2 & -3) and advocates for open source alternatives.
A delegate's analysis of Rubrik's Cloud Field Day 5 presentation, focusing on their Polaris platform and its potential beyond ransomware detection.

Explains the OAuth Resource Owner Password Credentials (ROPC) grant flow in Azure AD, detailing its purpose and why it should be avoided in modern applications.
Explains security risks of wildcard reply URLs in MSAL.js and demonstrates a safer alternative using session storage for post-login redirects.
An analysis of Sysdig's cloud-native monitoring solution, which uses eBPF for container security and performance insights.
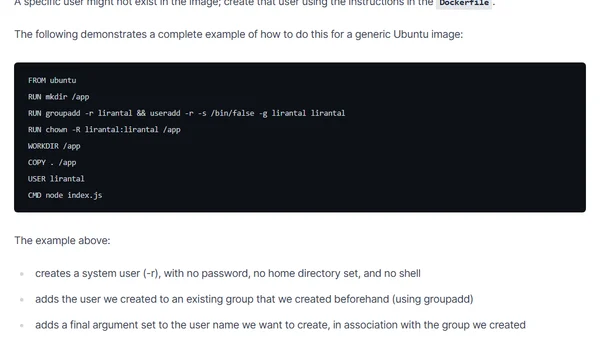
A guide on implementing Docker security best practices for Node.js, focusing on using non-root users to minimize attack surfaces.
A critical analysis of VPN services, highlighting privacy risks and the importance of researching providers before use.
Guide to enabling TLS 1.2 support in legacy .NET applications without recompilation, using configuration file updates.
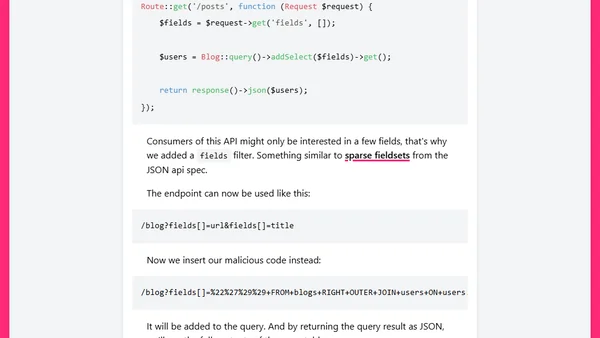
Explains SQL injection risks in Laravel's query builder, focusing on unsafe functions like addSelect and JSON shorthand, with a fixed vulnerability example.
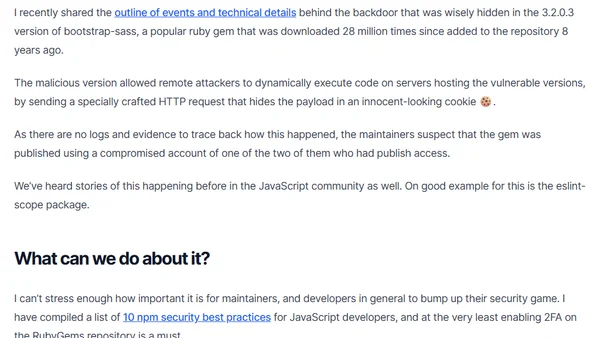
Analysis of a malicious backdoor discovered in the popular bootstrap-sass Ruby gem, its impact, and essential security best practices for developers.
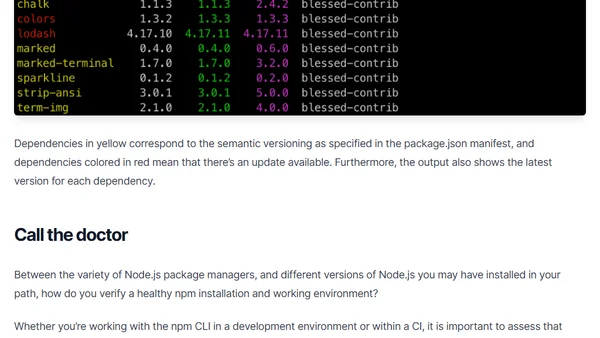
Learn how to use npm outdated and npm doctor commands to assess your project's dependency health and environment setup.
A developer's updated reflections on Intel SGX technology, considering its original DRM purpose and new use cases for secure cloud execution.
Part 6 of a series on AWS serverless mistakes, focusing on security best practices like IAM roles, secret management, and OWASP risks.

Part 2 of a series on championing third-party observability tools to your security team, focusing on building empathy and alignment.