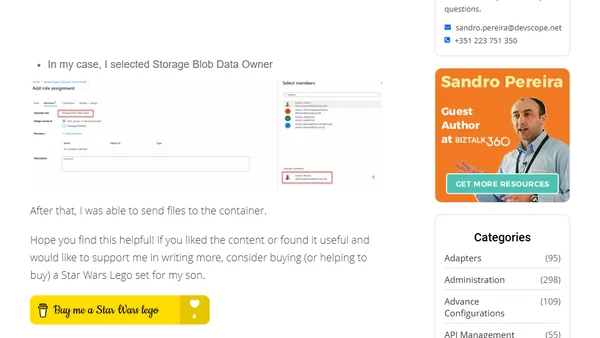
Storage Account: You do not have permissions to list the data using your user account with Entra ID
Explains why being an Azure Storage Account Owner doesn't grant data access and how to assign the correct Storage Data roles.

Explains why being an Azure Storage Account Owner doesn't grant data access and how to assign the correct Storage Data roles.
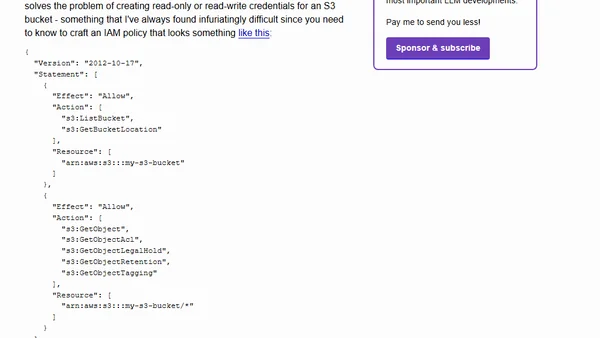
Discusses the future of small open source libraries in the age of LLMs, questioning their relevance when AI can generate specific code.
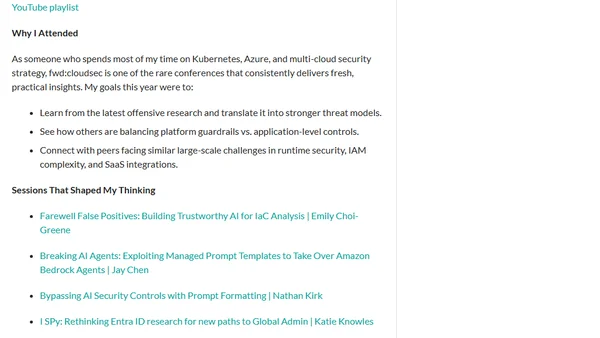
A practitioner's key takeaways from the fwd:cloudsec 2025 conference, focusing on cloud security research, offensive techniques, and defensive strategies.
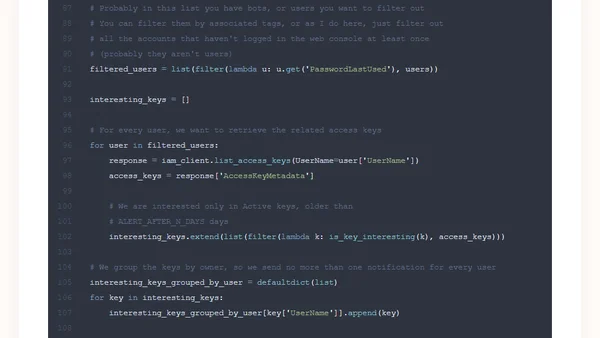
A tutorial on automating AWS IAM access key age notifications using AWS Lambda and SES, with code examples and security best practices.

An analysis of AWS EKS Pod Identity, comparing it to IRSA, explaining its benefits, and discussing why the author's company hasn't adopted it yet.
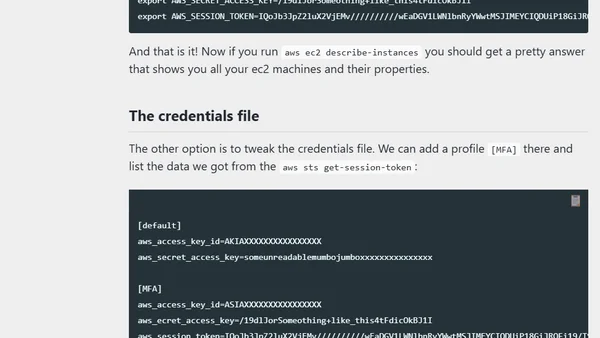
A guide to enforcing AWS IAM 2FA and scripting logins for secure, automated command-line access.
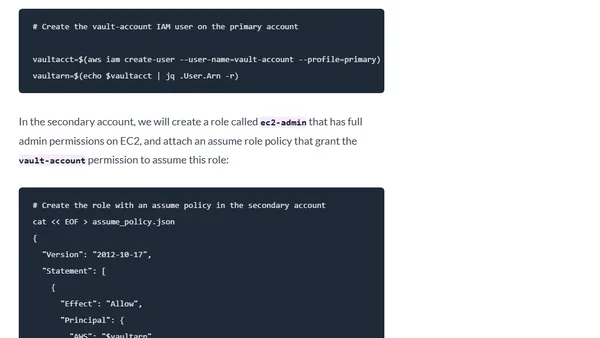
A guide to configuring HashiCorp Vault's AWS secrets engine to dynamically generate credentials across multiple AWS accounts using the assume_role feature.
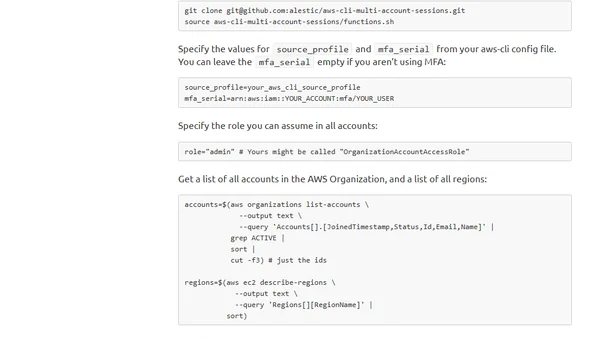
A guide to automating the creation of AWS IAM Access Analyzers across all regions in all accounts of an AWS Organization using the AWS CLI.
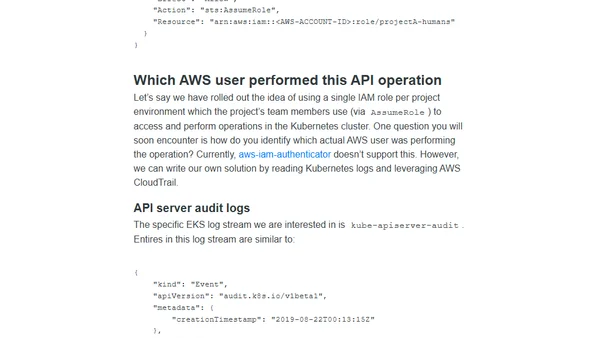
A guide to managing user authentication and authorization for AWS EKS clusters using IAM roles and the aws-auth ConfigMap.
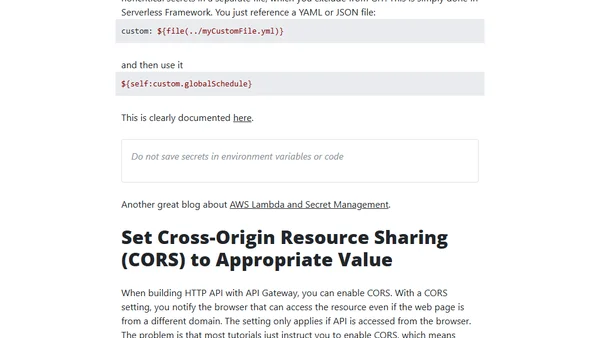
Part 6 of a series on AWS serverless mistakes, focusing on security best practices like IAM roles, secret management, and OWASP risks.
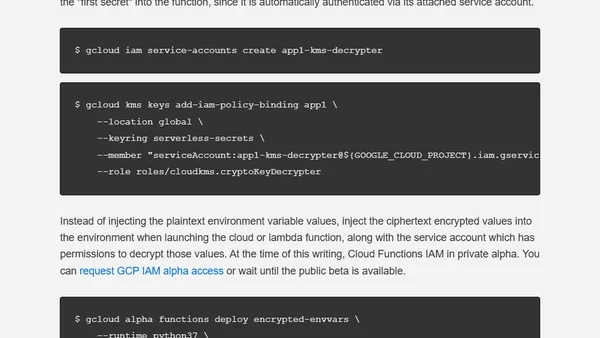
Explores methods for managing secrets and credentials in serverless applications, comparing IAM, environment variables, and other approaches.
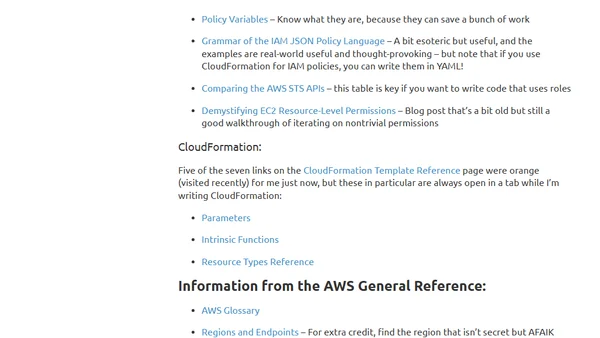
A sysadmin's guide to navigating and mastering AWS documentation, including meta-docs, key services, and frequently updated pages.
Explains how to use AWS cross-account IAM roles and the AssumeRole API (Use-STSRole) in Windows PowerShell for multi-account strategies.
Explains AWS authentication options like root accounts and IAM users, focusing on security best practices and access control.