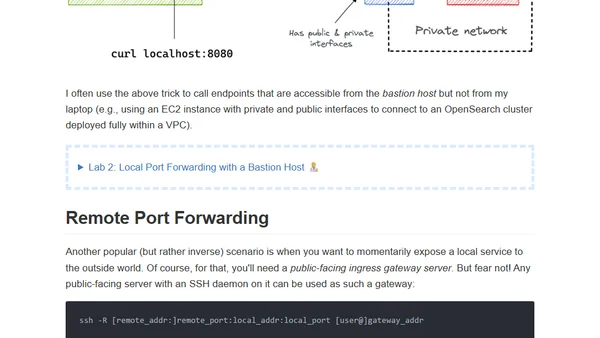
A Visual Guide to SSH Tunnels (with labs)
A visual guide and hands-on labs explaining SSH tunnels, focusing on local and remote port forwarding for developers.

A visual guide and hands-on labs explaining SSH tunnels, focusing on local and remote port forwarding for developers.
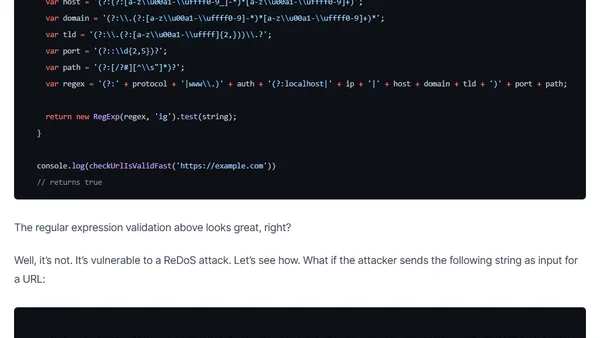
Explains why using RegEx for URL validation in JavaScript can introduce security vulnerabilities like ReDoS attacks, and recommends safer alternatives.
An overview of core cryptography concepts and their implementation in Python, based on a presentation by Andrew Sillers.
VMware vSphere 6.5 and 6.7 reach end of general support, urging users to upgrade for security and updates.
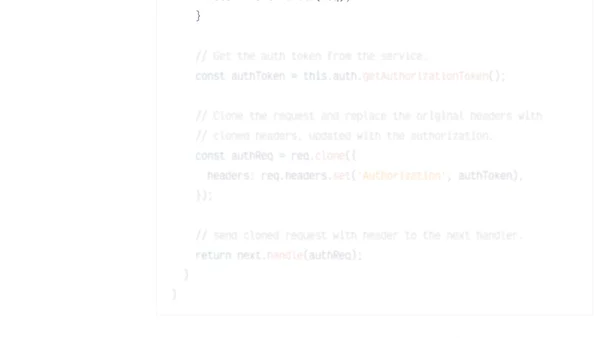
Discusses security risks in Angular HTTP interceptors, especially when exposing authentication tokens, and provides examples from common implementations.
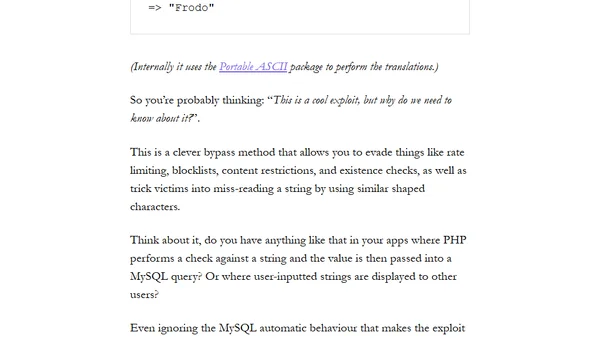
Explains how Unicode transliteration can bypass security measures like rate limiting in Laravel apps and how to fix it.
Announcing django-denied, a Django package that enforces authorization by denying all views by default for enhanced security.
A Laravel security tip on using Git's selective staging (git add -p) to review code before committing, preventing secrets or debug code from being pushed.
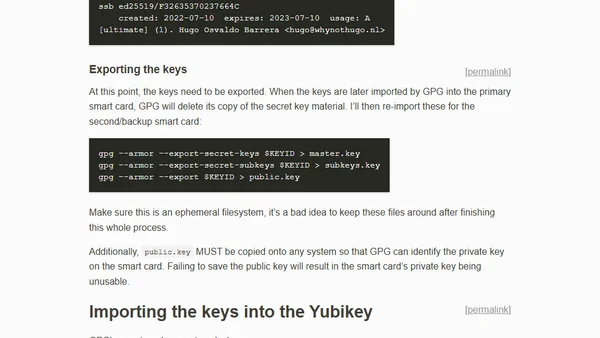
A technical guide on setting up and using a Yubikey hardware token for GPG encryption and signing, covering key generation and smart card configuration.
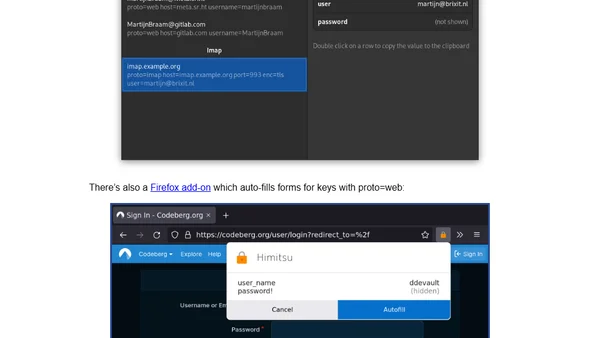
Introducing Himitsu, a new Unix key/value store and protocol for managing secrets like passwords and SSH keys, with a focus on extensibility and user consent.
A comprehensive guide to all OAuth 2.0 grant types, explaining their flows and use cases for secure application authorization.
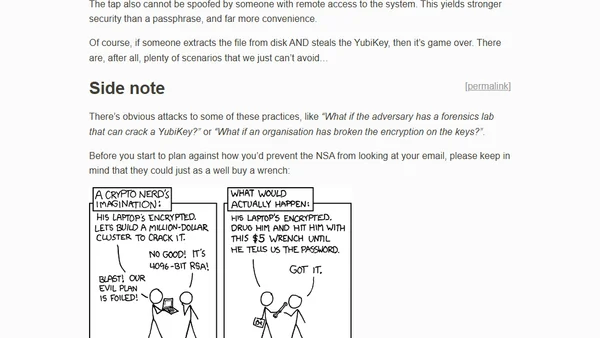
A developer shares practical tips and warnings for using YubiKeys for 2FA, SSH authentication, and sudo prompts to enhance security.
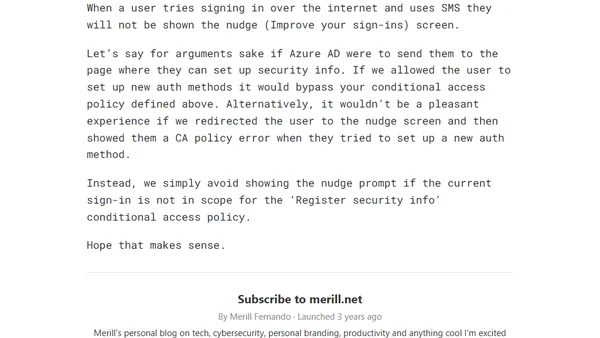
Explains why Azure AD's 'Nudge' campaign fails to prompt users to register the Microsoft Authenticator app, often due to conflicting Conditional Access policies.
A PowerShell guide to increase security by removing unwanted HTTP response headers from an Azure Application Gateway using rewrite rules.
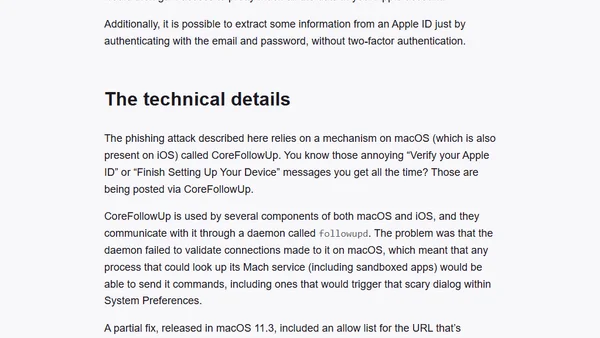
A macOS bug allowed malicious apps to spoof Apple ID verification alerts within System Preferences, enabling sophisticated phishing attacks.
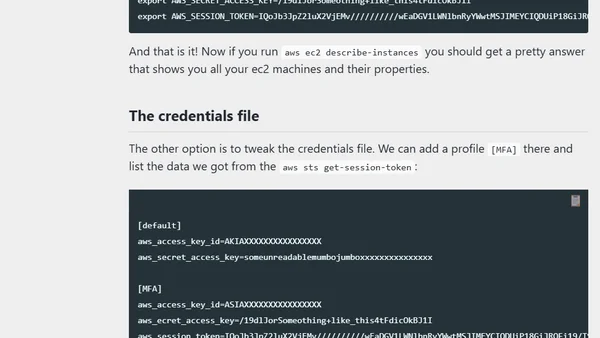
A guide to enforcing AWS IAM 2FA and scripting logins for secure, automated command-line access.
Announcing a new book for JavaScript developers on practical cryptography, covering hashing, encryption, and digital signatures.
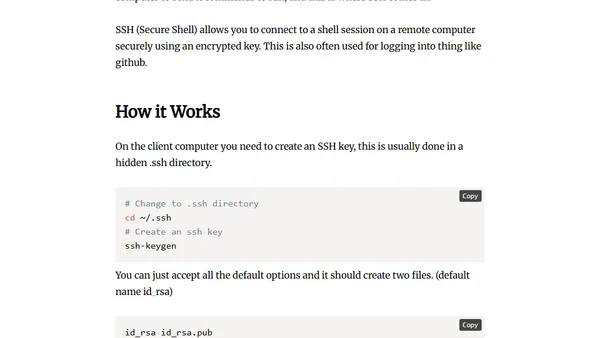
Explains SSH (Secure Shell), its purpose for secure remote computer connections, and how to generate and use SSH keys.
A critical analysis of Plaid's security model, arguing its credential collection widget undermines decades of online banking security best practices.
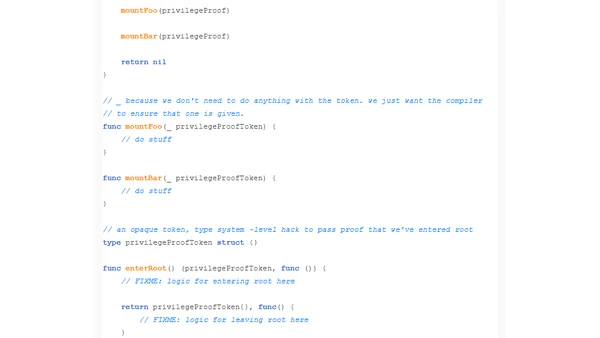
A programming pattern using opaque tokens and the type system to ensure functions requiring root privileges are only called from within a root context.