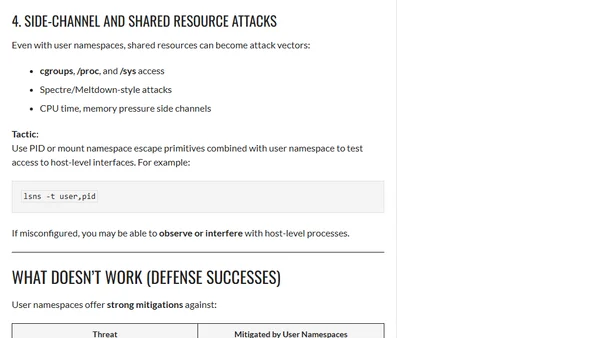
User Namespaces in Kubernetes: Perspectives on Isolation and Escape
Analyzes Kubernetes User Namespaces from an offensive security perspective, covering isolation benefits, potential misconfigurations, and escape vectors.

Analyzes Kubernetes User Namespaces from an offensive security perspective, covering isolation benefits, potential misconfigurations, and escape vectors.
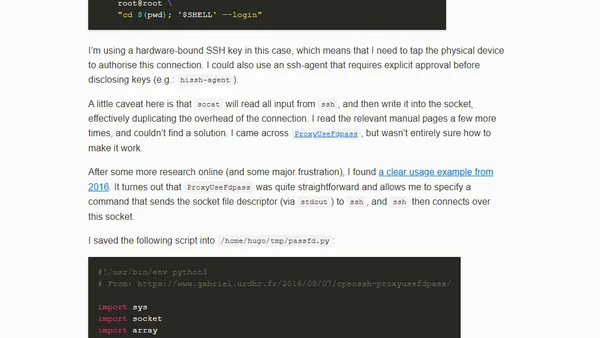
Explores using a local SSH server as a secure alternative to sudo for privilege management, avoiding setuid binaries.
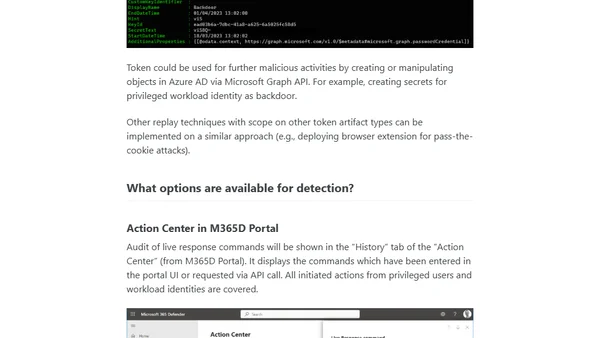
Analyzes the abuse of Microsoft 365 Defender's Live Response feature for privilege escalation on Tier0 assets and discusses detection methods.
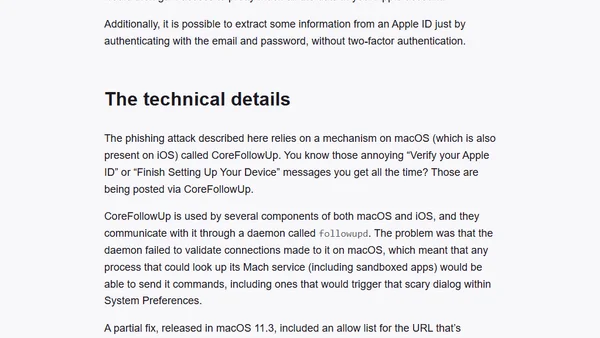
A macOS bug allowed malicious apps to spoof Apple ID verification alerts within System Preferences, enabling sophisticated phishing attacks.
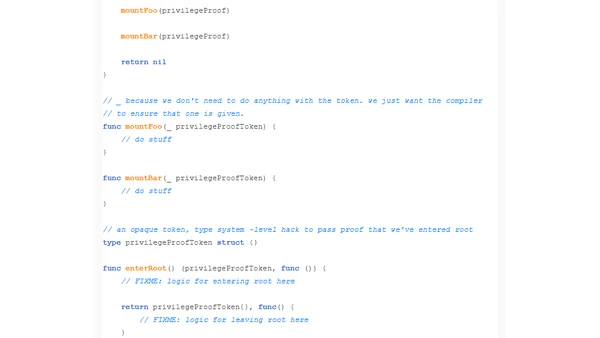
A programming pattern using opaque tokens and the type system to ensure functions requiring root privileges are only called from within a root context.

Explores the feasibility of CPU backdoors, how they could be implemented, and the security risks they pose.