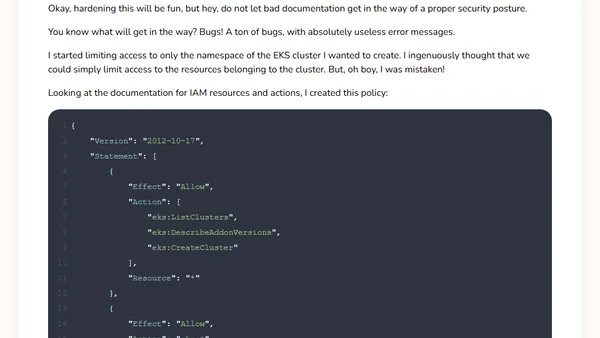
The inconsistencies of AWS EKS IAM permissions
Explores challenges and inconsistencies when configuring IAM permissions for AWS EKS clusters following the principle of least privilege.

Explores challenges and inconsistencies when configuring IAM permissions for AWS EKS clusters following the principle of least privilege.

A guide to using the open-source security tool Falco for dynamic security monitoring and threat detection in AWS EKS Kubernetes clusters.

An analysis of AWS EKS Pod Identity, comparing it to IRSA, explaining its benefits, and discussing why the author's company hasn't adopted it yet.

Explains how to use AWS EBS-backed ephemeral volumes in Kubernetes for temporary storage, avoiding node disk pressure and multi-attach errors.
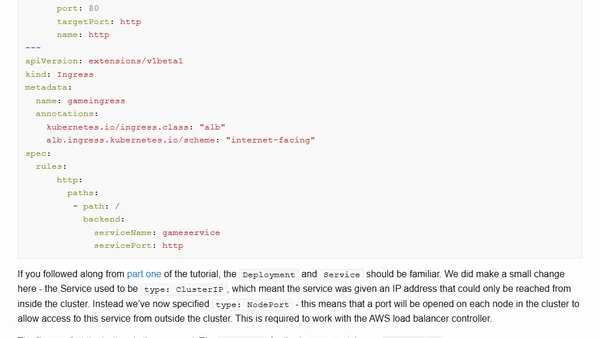
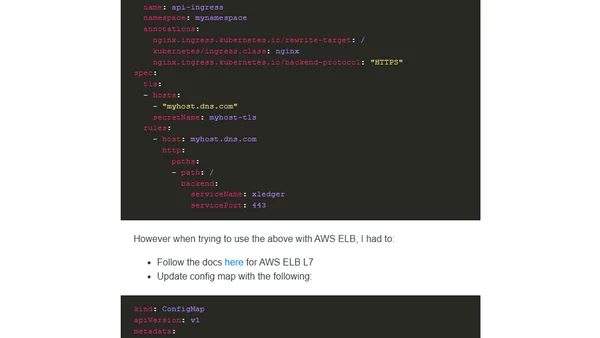
A technical tutorial on exposing Kubernetes services to the internet using AWS EKS, Ingress, and the AWS Load Balancer Controller.
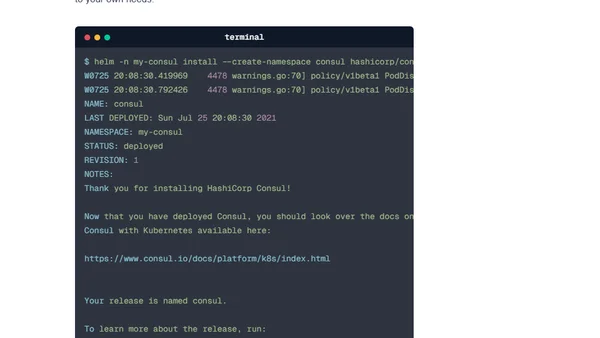
A technical guide on deploying a high-availability HashiCorp Vault cluster on AWS EKS using Helm, Consul, and AWS KMS for auto-unsealing.
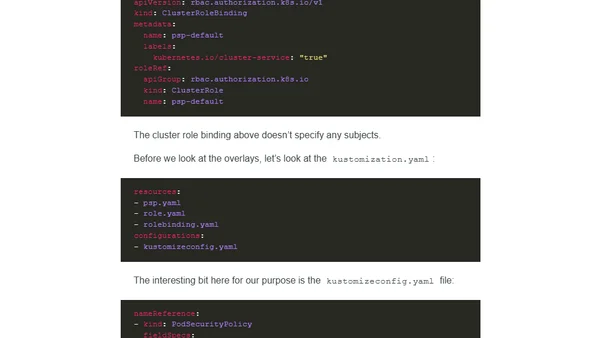
A technical guide explaining Kubernetes Pod Security Policies (PSP), their enforcement, and management using tools like kustomize.
A technical guide on setting up an AWS EKS Kubernetes cluster using Terraform, covering IAM, security groups, and cluster configuration.