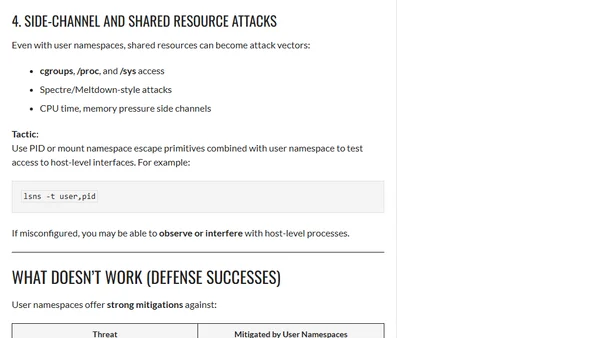
User Namespaces in Kubernetes: Perspectives on Isolation and Escape
Analyzes Kubernetes User Namespaces from an offensive security perspective, covering isolation benefits, potential misconfigurations, and escape vectors.

Analyzes Kubernetes User Namespaces from an offensive security perspective, covering isolation benefits, potential misconfigurations, and escape vectors.
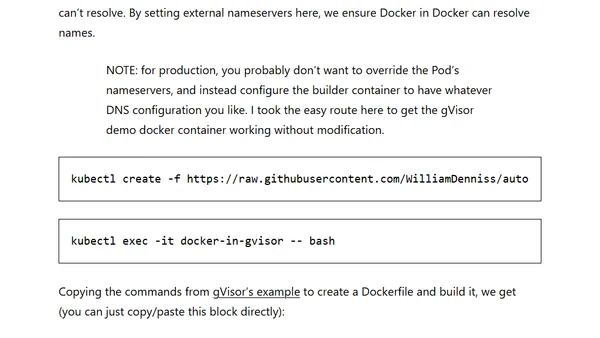
A guide to running Docker-in-Docker workloads securely on GKE Autopilot using the gVisor sandbox, including cluster configuration steps.
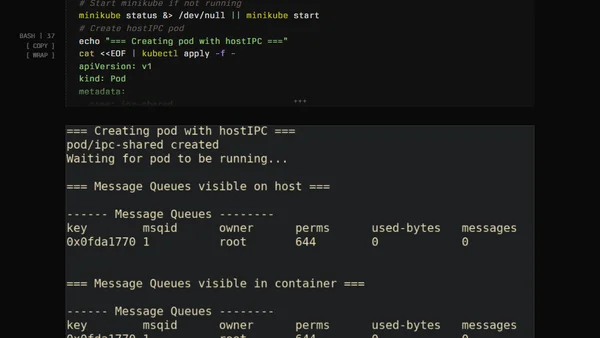
Explains the nuanced differences between privileged pods and host namespace sharing in Kubernetes, clarifying common misconceptions.
Explores strategies and tools for securely updating container images to maintain system security and stability in modern infrastructure.
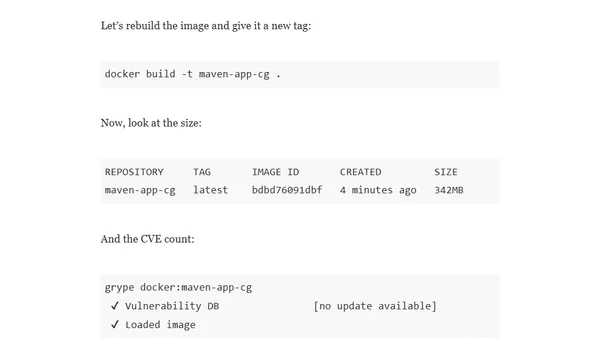
A guide to building smaller, more secure Java container images using Chainguard Images, reducing size and CVEs.
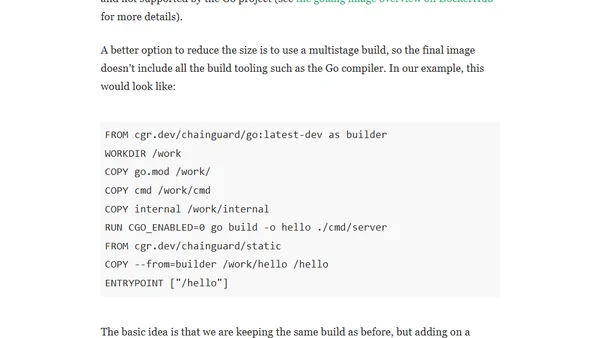
Explains how to create smaller, more secure container images for Go applications using minimal base images like Chainguard Images to reduce size and eliminate CVEs.
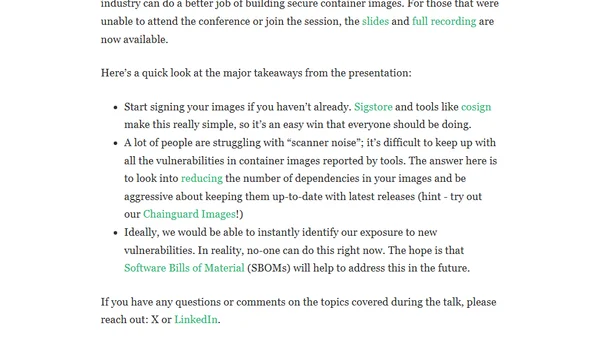
A guide to building secure container images, covering image signing, reducing scanner noise, and using SBOMs for vulnerability management.
Analysis of the Dirty Pipe Linux kernel vulnerability (CVE-2022-0847), its impact on cloud environments, and defensive advice.
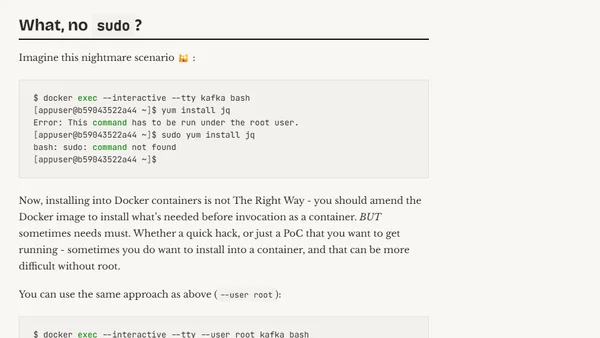
How to run commands as root in Docker containers that default to non-root users, using the --user flag.
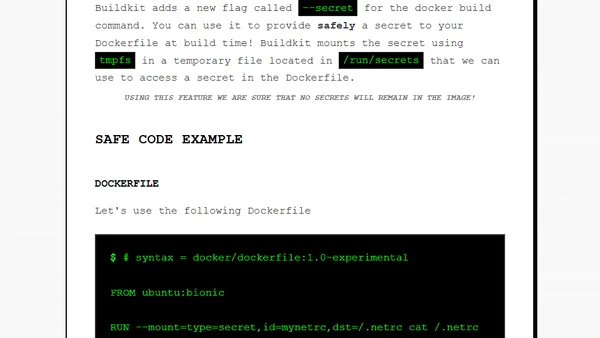
A tutorial on securely managing secrets during Docker builds using Buildkit, avoiding common vulnerabilities.
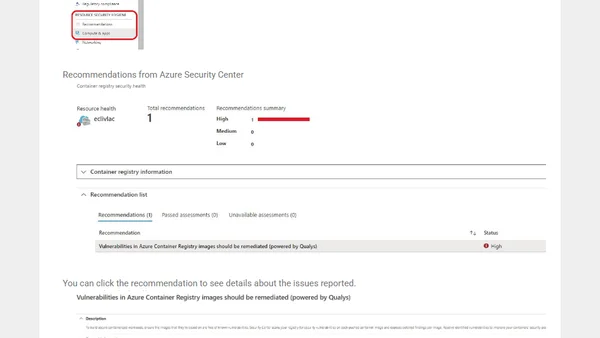
Explains how to use Azure Security Center to scan container images in Azure Container Registry for vulnerabilities, powered by Qualys.
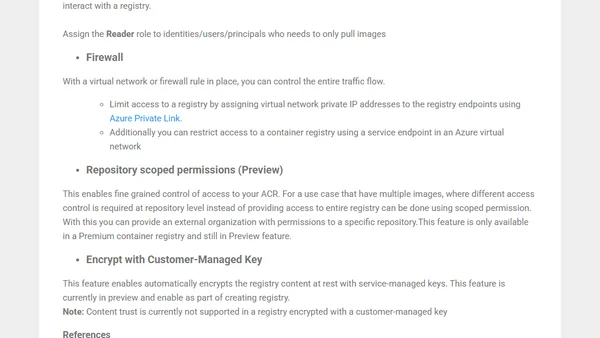
Best practices for securing Azure Container Registry, including image scanning, content trust, managed identities, and network controls.
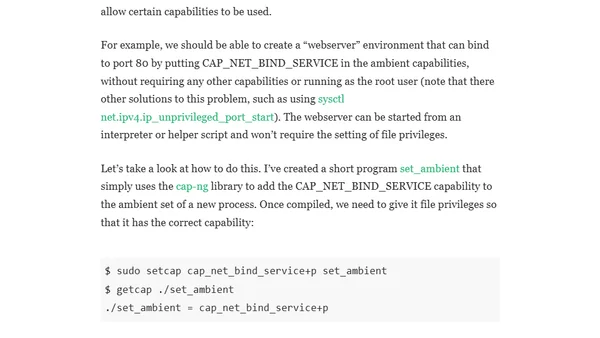
A practical guide to understanding and using Linux capabilities, with examples and tooling for managing privileges in containers.
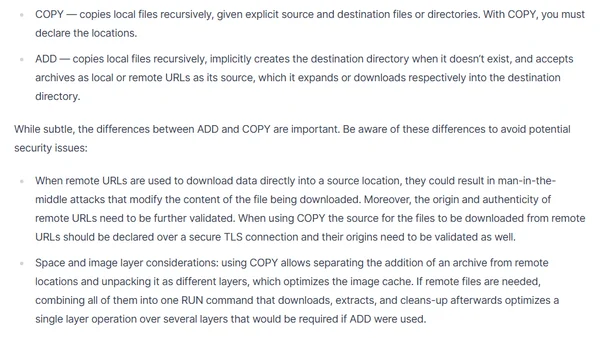
Explains the security and performance differences between Docker's COPY and ADD commands, recommending COPY for safer image builds.
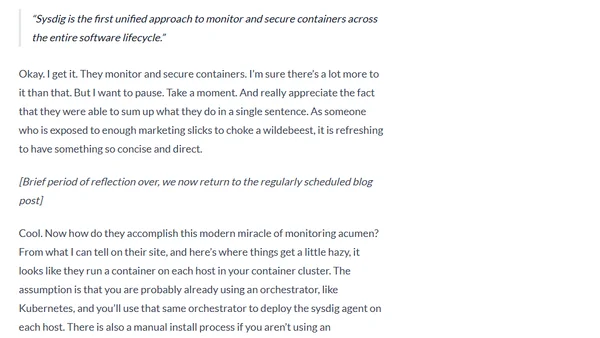
A delegate previews Sysdig's container monitoring and security platform ahead of a Cloud Field Day event, analyzing its integration with cloud and Kubernetes.
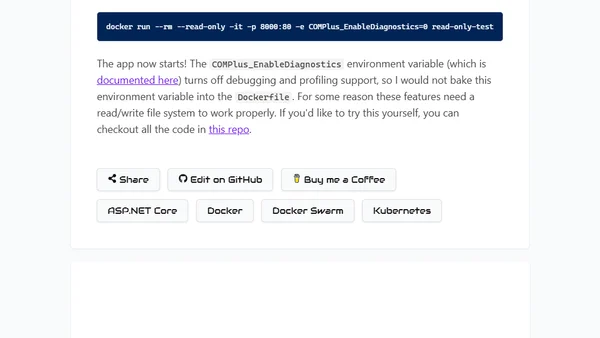
Explains how to run ASP.NET Core applications in Docker containers with a read-only file system for enhanced security, including a workaround for a known issue.
A guide demystifying Kubernetes, focusing on foundational concepts and security for beginners and security professionals.
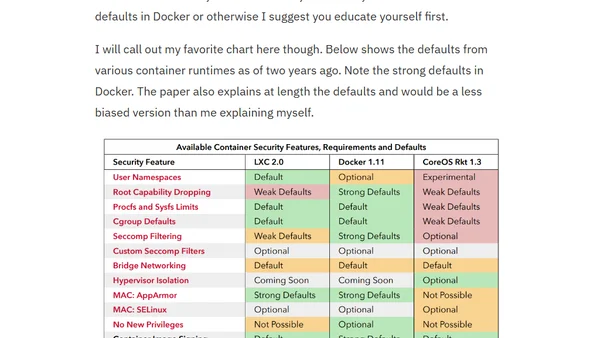
A critique of container security messaging, arguing that existing defaults like Seccomp and AppArmor provide robust, multi-layered sandboxing.
Explores methods for building secure, unprivileged container images within Kubernetes clusters without compromising security.
A guide on implementing read-only file systems in Docker containers for enhanced security, covering CLI and Docker Compose methods.