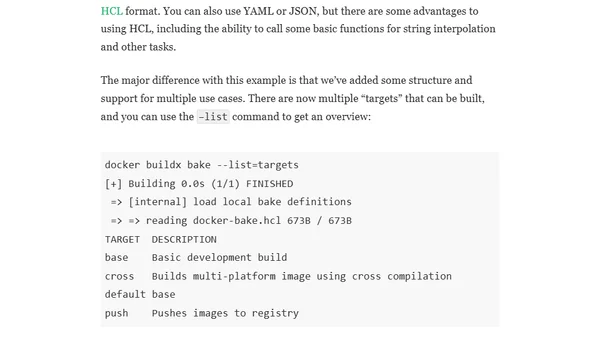
Docker Bake and Chainguard Images
Explains how to use Docker Bake to simplify and automate multi-stage Docker builds, with a focus on integrating Chainguard Images.
Adrian Mouat is a software engineer, consultant, speaker, and author specializing in containers, DevOps, Kubernetes, and software supply chain security. He is the author of Using Docker and creator of the Trow container registry, sharing expertise through talks, writing, and open-source contributions.
14 articles from this blog

Explains how to use Docker Bake to simplify and automate multi-stage Docker builds, with a focus on integrating Chainguard Images.

A guide to building multi-architecture Docker images using Chainguard Images, covering QEMU emulation, cross-compilation, and native runners.
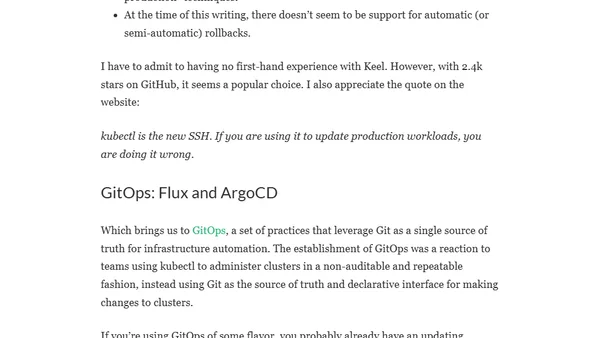
Explores strategies and tools for securely updating container images to maintain system security and stability in modern infrastructure.
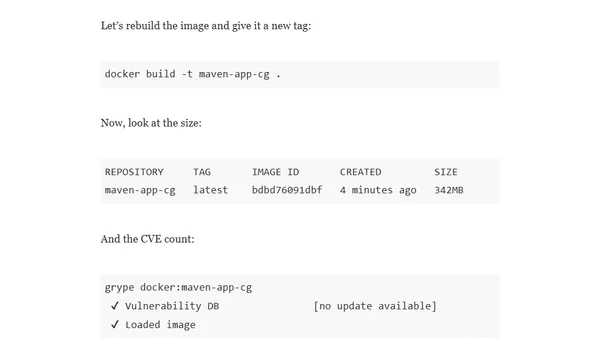
A guide to building smaller, more secure Java container images using Chainguard Images, reducing size and CVEs.
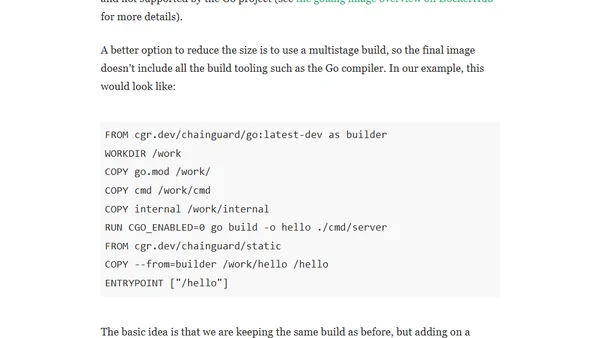
Explains how to create smaller, more secure container images for Go applications using minimal base images like Chainguard Images to reduce size and eliminate CVEs.
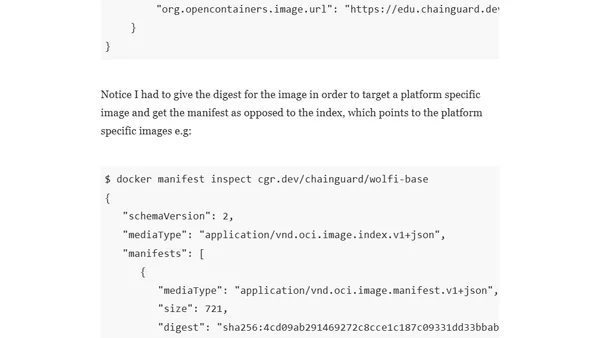
Explains the difference between annotations and labels in container images, referencing OCI specs and examples from Bitnami and Chainguard.
A guide to building secure container images, covering image signing, reducing scanner noise, and using SBOMs for vulnerability management.

A developer shares a list of their recent tech conference talks on topics like Kubernetes security, WebAssembly, and Docker.
A developer explains how they replaced Disqus with Webmention, a W3C standard, to add ad-free, privacy-focused comments to their static Hugo blog.
A developer's predictions for the future of computing, covering WASM, Rust, Kubernetes rivals, serverless, AI, and programming language trends.
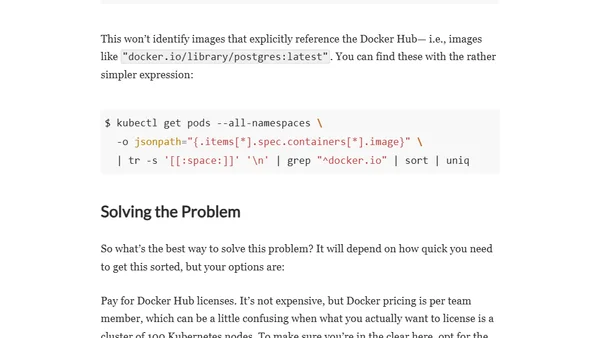
A guide to understanding and mitigating Docker Hub's rate limits on image pulls, especially in Kubernetes and CI/CD environments.
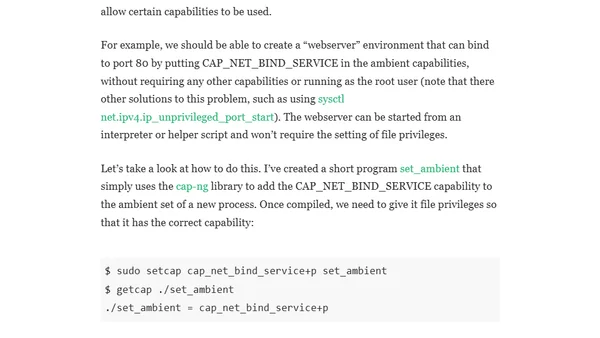
A practical guide to understanding and using Linux capabilities, with examples and tooling for managing privileges in containers.

Explains the history and mechanics of Linux capabilities, a security model for granular process privileges, and their interaction with containers.
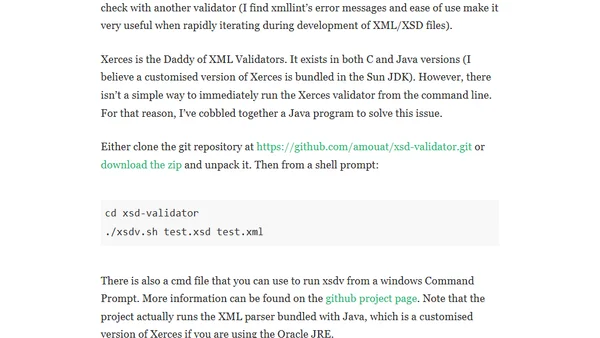
A guide to validating XML files against XML Schemas using online tools, command-line utilities like xmllint, and the Xerces parser.