Safeguarding target=_blank links
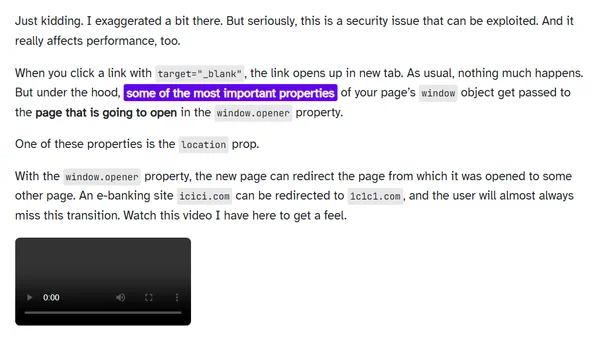
Explains the security and performance risks of using target=_blank links without rel="noopener" and provides the simple fix.

Explains the security and performance risks of using target=_blank links without rel="noopener" and provides the simple fix.
A detailed analysis of a blackmail email scam demanding a $2000 Bitcoin payment to prevent the release of compromising material.
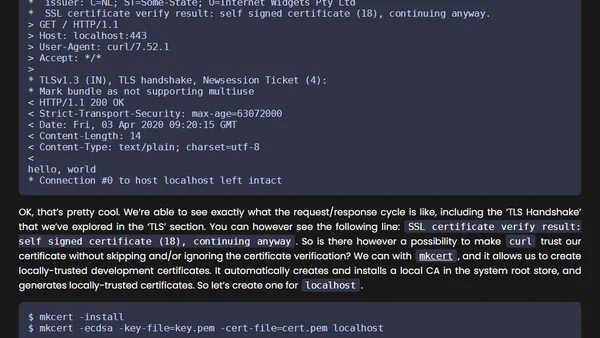
A guide to implementing security best practices for Go HTTP webservers, covering timeouts, TLS, and other hardening measures.
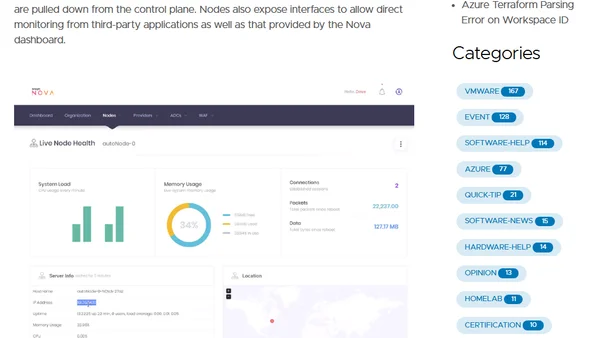
A review of Snapt's Nova platform for multi-cloud load balancing, web acceleration, and security, presented at a virtual IT event.
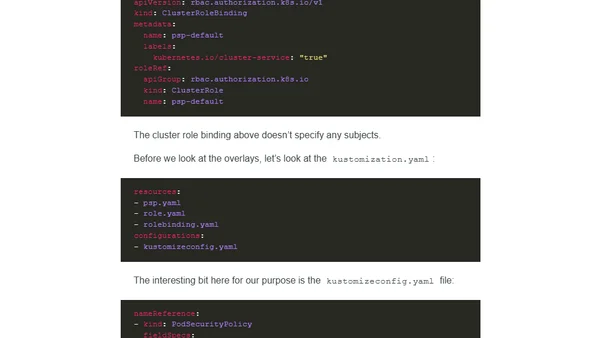
A technical guide explaining Kubernetes Pod Security Policies (PSP), their enforcement, and management using tools like kustomize.
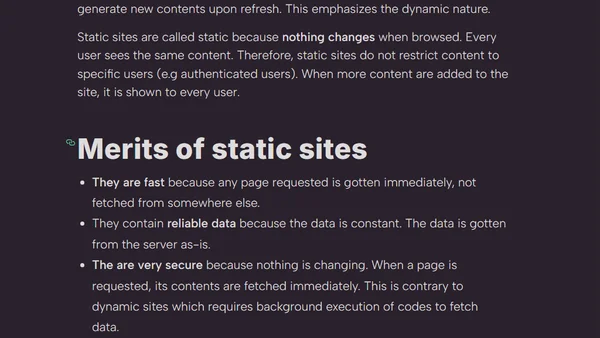
Explains static site generators (SSGs), their benefits for speed and security, and contrasts them with dynamic websites.
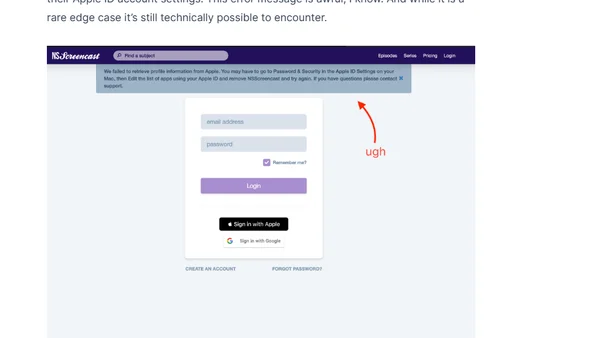
A developer's guide to implementing Sign-in with Apple, focusing on challenges with one-time profile data and security considerations.
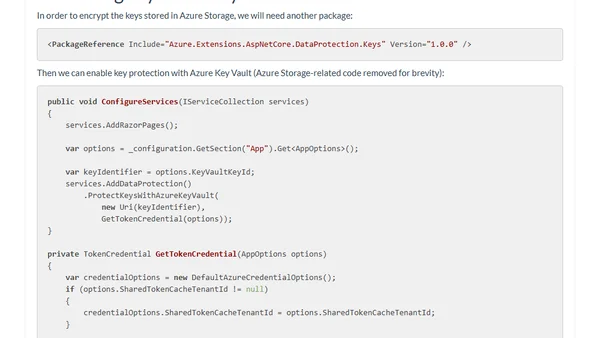
Guide to securely storing ASP.NET Core Data Protection keys using Azure Key Vault for encryption and Azure Blob Storage for persistence.
A software expert's open letter opposing the EARN IT Act, arguing it threatens essential end-to-end encryption and digital freedoms.
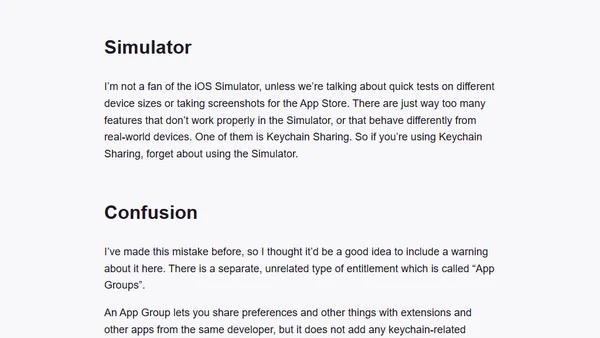
Explores common issues and solutions when implementing Keychain Sharing for iOS app extensions, covering group names, simulator limitations, and entitlements.
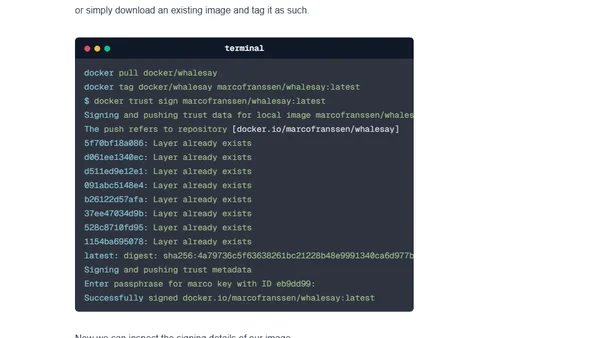
A guide to using Docker Content Trust (DCT) to digitally sign Docker images, ensuring integrity and publisher authenticity.
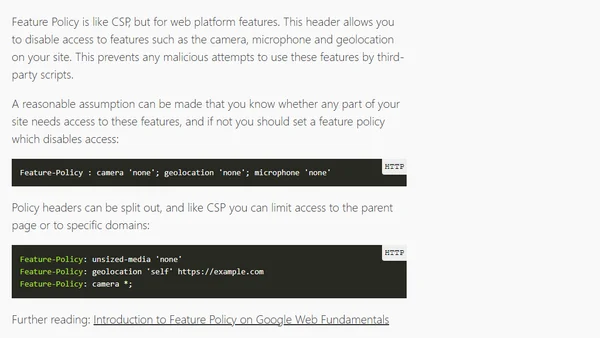
A guide to configuring essential HTTP response headers like Content-Security-Policy and Cache-Control for improved security and performance on static sites hosted on Netlify.
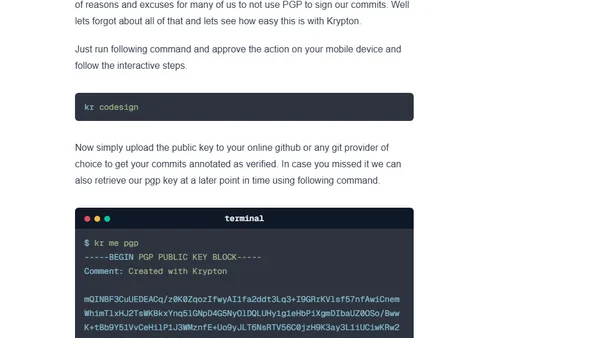
A tutorial on setting up two-factor authentication for SSH and PGP keys using the Krypton tool, storing keys on a mobile device.
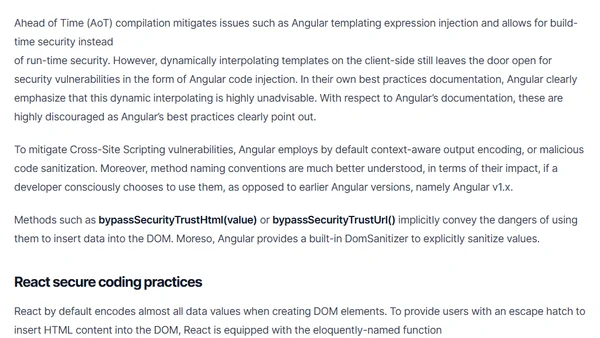
A technical comparison of built-in security features and secure coding practices in React and Angular frameworks.
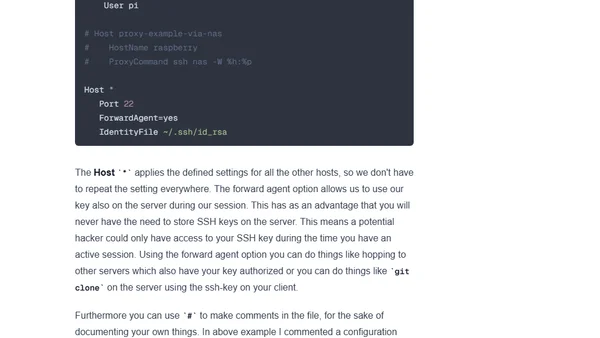
A guide to using SSH efficiently from the terminal, covering key generation, SSH agent setup, and best practices for secure remote access.
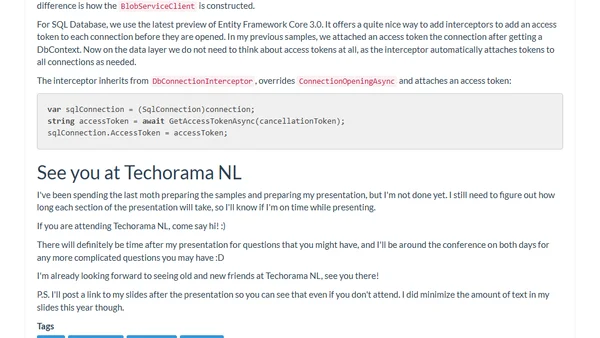
A speaker discusses using Azure Managed Identities to securely access services without managing keys, including a demo app for file sharing.
Azure AD now blocks cross-tenant token attacks by preventing apps from getting tokens for tenants where they have no service principal.

Explains the history and mechanics of Linux capabilities, a security model for granular process privileges, and their interaction with containers.
Essential npm security best practices to protect against malicious packages, including ignoring run-scripts and vetting third-party modules.

Explores SQL Server 2019's new 'Feature Restrictions' security feature, designed to help prevent SQL injection attacks.