Code Signing is not Enough
Explains the limitations of code signing for software security and introduces software provenance as a more robust alternative.

Explains the limitations of code signing for software security and introduces software provenance as a more robust alternative.
A developer's prank NPM package called 'everything' that depends on all public packages causes dependency chaos and highlights registry policy flaws.
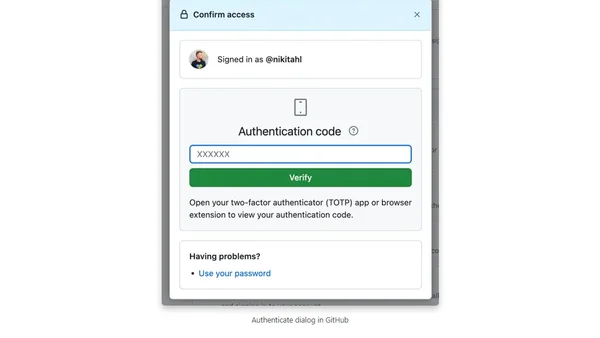
A step-by-step guide on how to change the TOTP-based two-factor authentication app linked to your GitHub account.
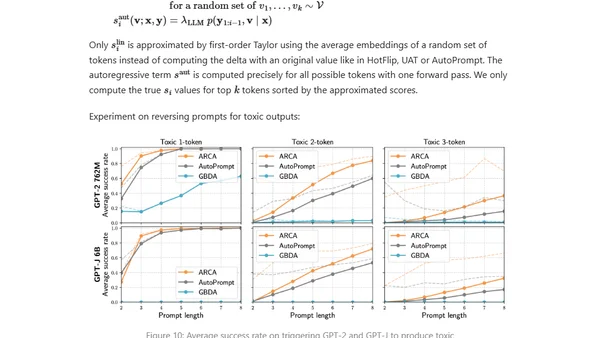
Explores adversarial attacks and jailbreak prompts that can make large language models produce unsafe or undesired outputs, bypassing safety measures.
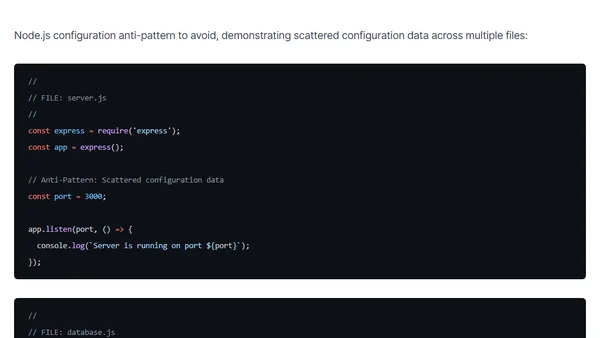
Explores configuration management patterns and anti-patterns for Node.js applications, focusing on security, portability, and maintainability.
Explains why using the Device Filter is more secure than Device Platform for Conditional Access policies targeting managed devices.
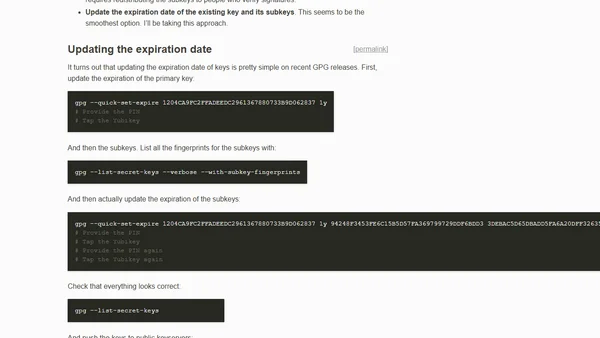
A technical guide on how to extend the expiration date of an existing GPG key and its subkeys, including commands and best practices.
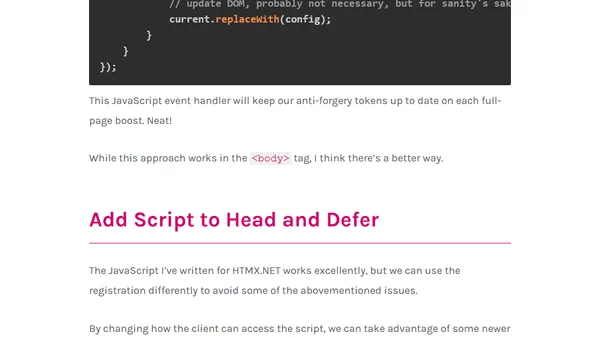
Explains how to handle ASP.NET Core anti-forgery tokens when using HTMX boosts, including solutions for script re-registration.
A developer shares a cautionary tale about identity theft on freelancer platforms, based on a Darknet Diaries podcast episode.
Explains why eBPF observability tools, designed for low overhead, are not suitable for security monitoring due to evasion risks.
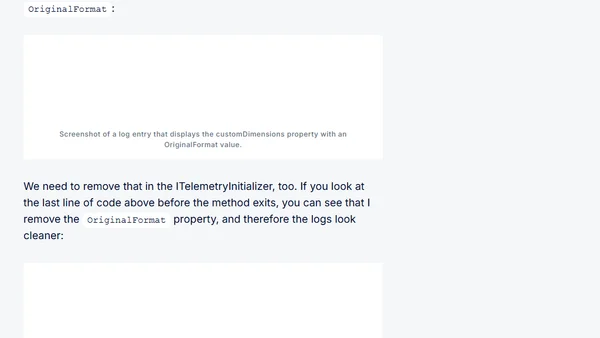
A guide to redacting sensitive PII data like email addresses from logs before they are sent to Azure Application Insights using C# and ITelemetryInitializer.

Introduces cdk-nag, an open-source tool for automated security and compliance checks in AWS CDK infrastructure-as-code projects.
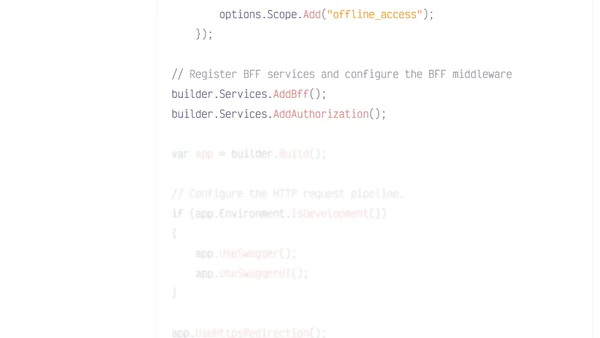
A guide to implementing a Backend for Frontend (BFF) architecture with .NET, Duende, and Auth0 to enhance SPA security by moving token handling server-side.
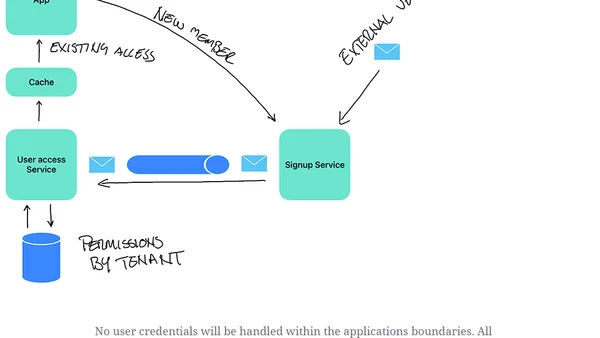
Explores a multi-tenancy security design pattern: external authentication with local authorization, using IDP tokens and SAGA for signup.
An overview of Django's built-in session management system, explaining its security features and how to configure them for robust user data protection.
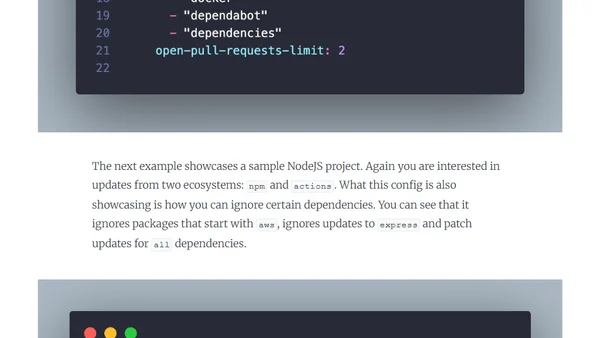
A guide on implementing Dependabot for automated dependency updates and vulnerability management to improve software supply chain security.
A developer shares their journey creating an open source activism program to teach collaboration and inclusivity in software development.

A guide to exporting Azure AD Conditional Access policies using PowerShell, focusing on retrieving readable object names instead of just IDs.
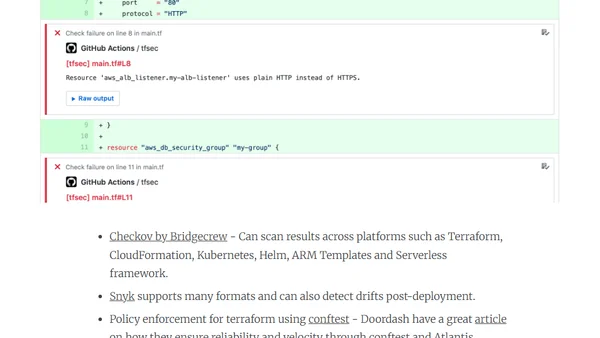
Explains the 'shift left' approach to integrating security early in the DevOps software development lifecycle for better outcomes.
A talk on implementing flexible, permission-based authorization in ASP.NET Core to overcome limitations of traditional role/claim-based systems.