Vulnerabilities That Will Define 2026
Analysis of emerging cybersecurity threats for 2026, focusing on AI-powered attacks, software supply chain flaws, and critical vulnerabilities in widely-used software.

Analysis of emerging cybersecurity threats for 2026, focusing on AI-powered attacks, software supply chain flaws, and critical vulnerabilities in widely-used software.
Introduces the Geomys Standard of Care, a professional framework for secure and reliable open-source software maintenance.
Analysis of 2024/2025 open source supply chain compromises, categorizing root causes like control handoff, phishing, and CI/CD vulnerabilities.
A developer shares their experience and security improvements gained from participating in the GitHub Secure Open Source Fund for their .NET projects.
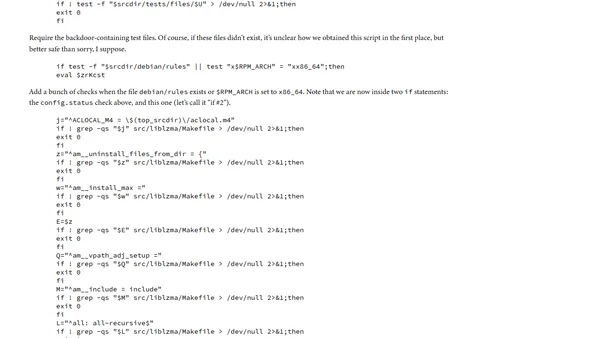
Analysis of the malicious shell script component in the xz backdoor attack, detailing its injection and execution mechanisms.
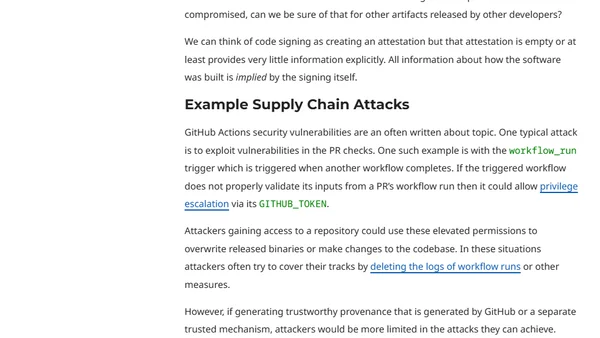
Explains the limitations of code signing for software security and introduces software provenance as a more robust alternative.
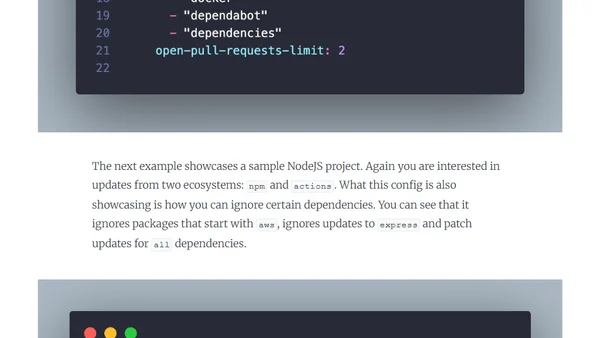
A guide on implementing Dependabot for automated dependency updates and vulnerability management to improve software supply chain security.
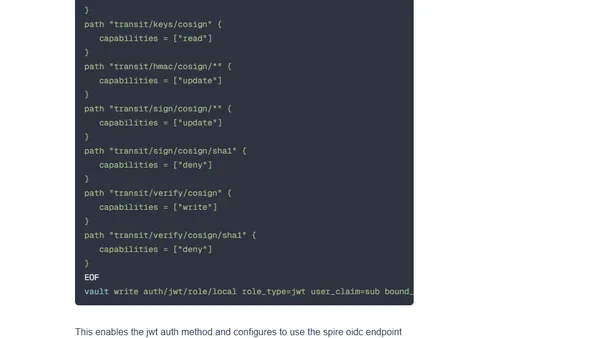
Introducing spiffe-vault, a CLI tool for secretless and keyless software supply chain security using SPIFFE and HashiCorp Vault.
Critique of proxy.golang.org's permanent caching, which hides broken dependencies and creates hidden risks in the Go ecosystem.
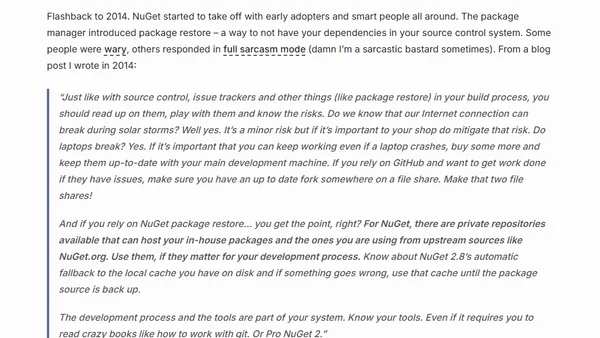
A developer discusses the risks of external dependencies after the 'left-pad' NPM incident and argues for mirroring critical packages.