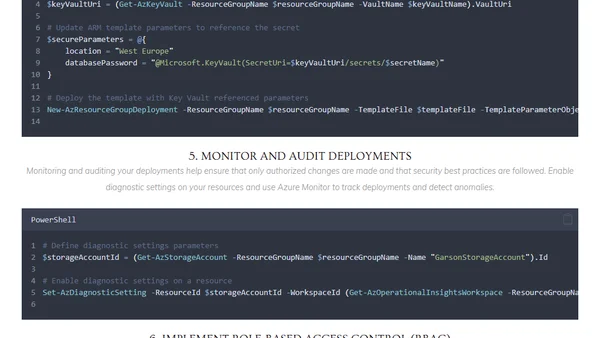
Best Practices for Secure IaC Deployment with Azure ARM templates
Explores best practices for securing Azure ARM templates and using PowerShell to automate secure Infrastructure as Code deployments.

Explores best practices for securing Azure ARM templates and using PowerShell to automate secure Infrastructure as Code deployments.
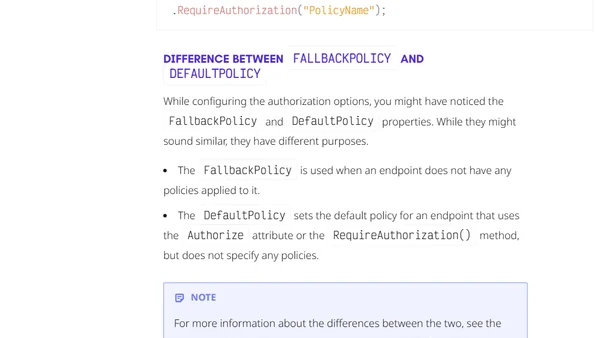
A developer shares lessons learned and pitfalls to avoid when implementing policy-based authorization in .NET applications.
Discussion on alternative app stores for iOS, their impact on developer workflows, code signing requirements, and preparing for new OS versions.
A technical guide on implementing DNSSEC using Azure's private preview feature, detailing the PowerShell command and its significance for security compliance.
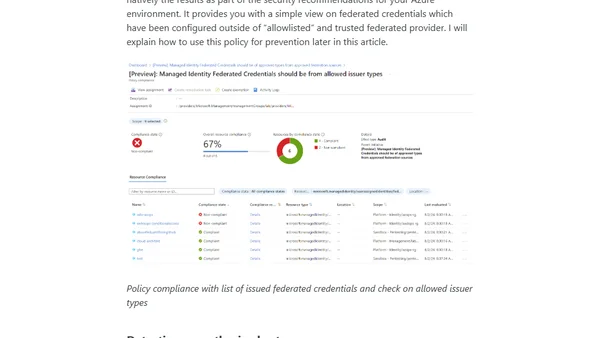
Explains security risks and attack scenarios for Managed Identities using Federated Credentials in Azure, focusing on privilege requirements and abuse prevention.
Analysis of W3C TAG's response to Google delaying third-party cookie removal, discussing privacy, ad tech, and web standards.
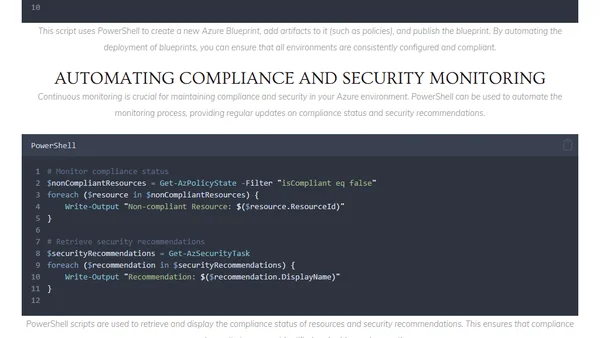
How to use PowerShell to automate compliance and security tasks in Microsoft Azure, including policy management and security monitoring.
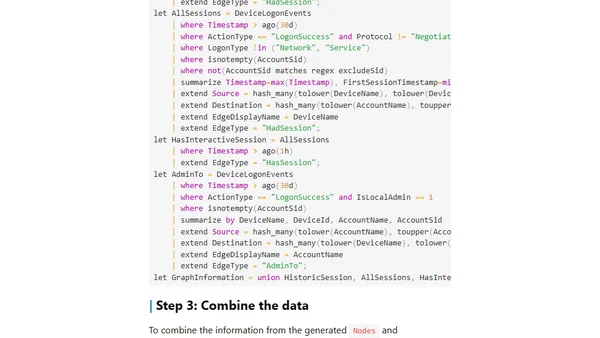
Explains how to use KQL Graph semantics in Microsoft security tools to identify lateral movement paths between users, computers, and groups.
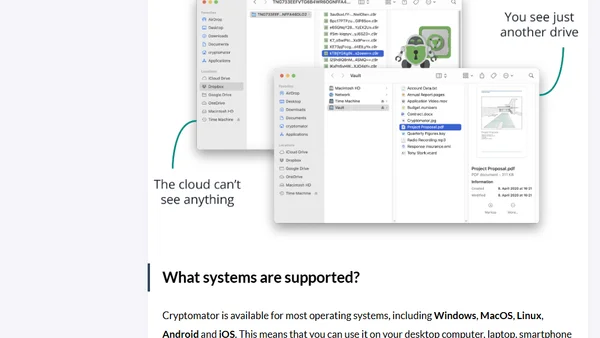
Explains how Cryptomator, a free open-source tool, provides end-to-end encryption for files stored in cloud services like Google Drive or Dropbox.
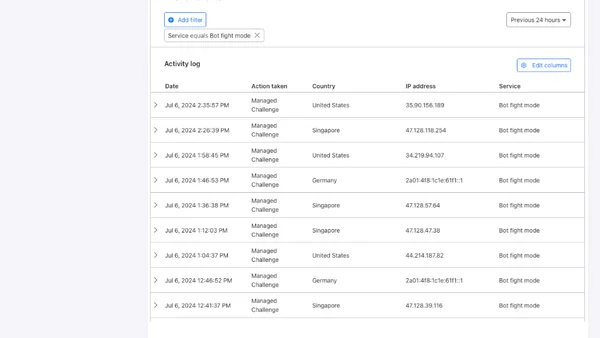
Cloudflare now offers a simple setting to block AI bots from scraping your website, available even on free plans.
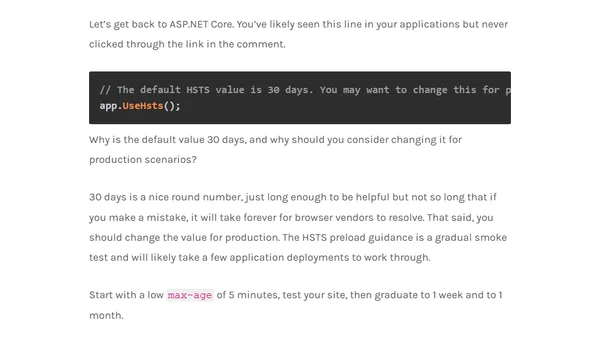
Explains HSTS (HTTP Strict Transport Security), its role in ASP.NET Core apps for enforcing HTTPS, and configuration considerations.
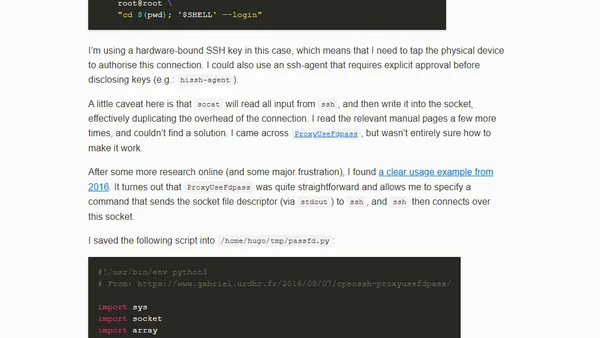
Explores using a local SSH server as a secure alternative to sudo for privilege management, avoiding setuid binaries.
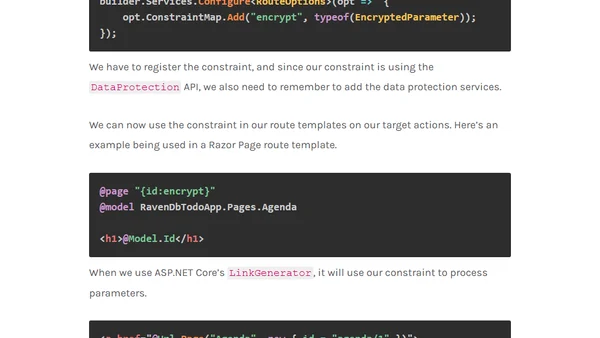
A guide to encrypting and decrypting sensitive identifiers in ASP.NET Core route parameters for improved security and data privacy.
Analyzes common security flaws in Express.js authentication, focusing on hardcoded secrets and poor cookie configuration, with solutions.
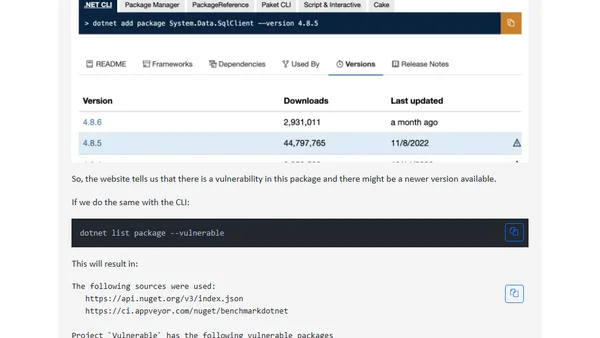
Learn how to use the dotnet CLI to check your .NET solution for NuGet packages with known vulnerabilities or that are deprecated.
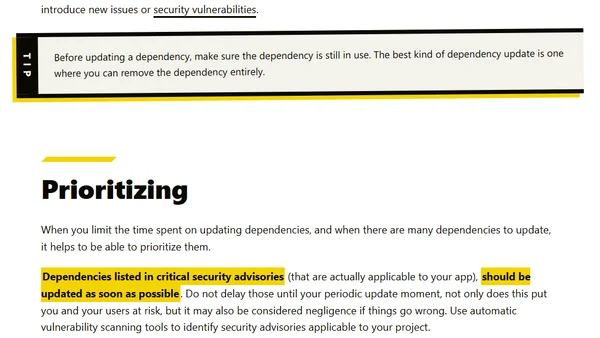
Discusses the challenges of keeping software dependencies updated and compares manual vs. automated strategies for managing updates effectively.
Discusses the retirement of Azure's default outbound access for VMs in 2025, explaining the security reasons and urging preparation.
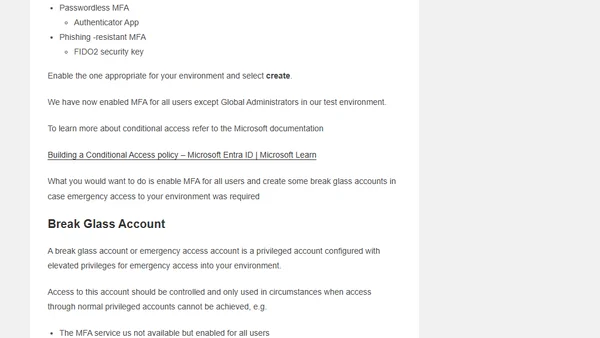
A technical guide on securing user identity in Azure Entra ID, covering MFA, Conditional Access, break glass accounts, and other security configurations.
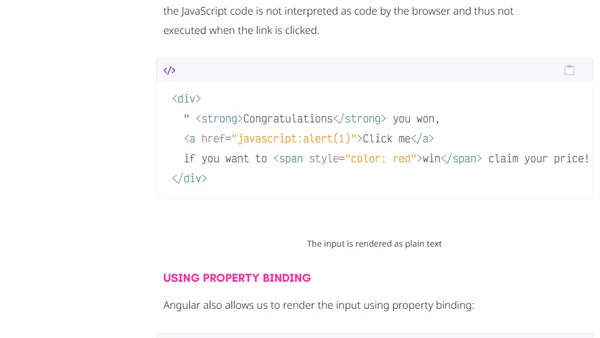
Explains how Angular's built-in security features automatically protect web applications from Cross-Site Scripting (XSS) attacks by sanitizing untrusted values.
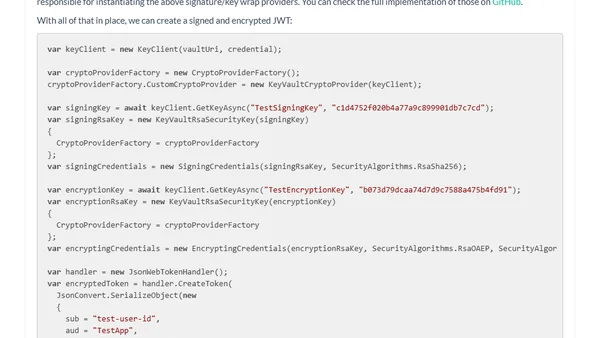
Explains how to use Azure Key Vault keys for signing and encrypting JSON Web Tokens (JWTs), including key rotation.