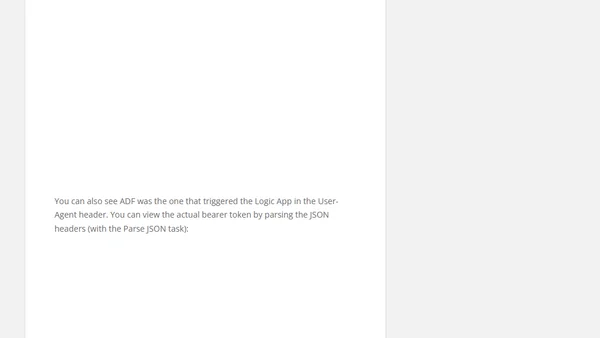
Secure Logic Apps with OAuth Authorization
A guide to securing Azure Logic Apps HTTP triggers by replacing SAS tokens with OAuth authorization policies and Azure AD authentication.

A guide to securing Azure Logic Apps HTTP triggers by replacing SAS tokens with OAuth authorization policies and Azure AD authentication.

A critique of JavaScript's dependency management after a major supply-chain attack, arguing for systemic change but predicting stagnation.
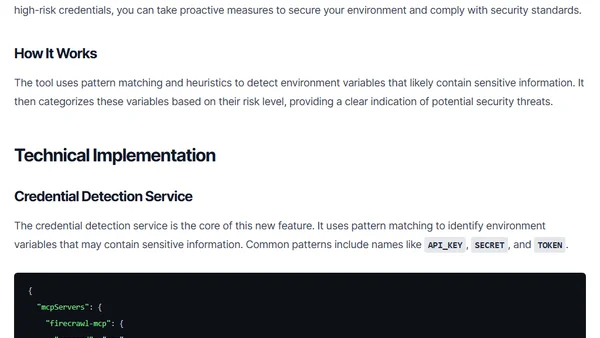
The ls-mcp tool update adds a security feature to detect and assess the risk of credentials stored in environment variables within MCP server configurations.
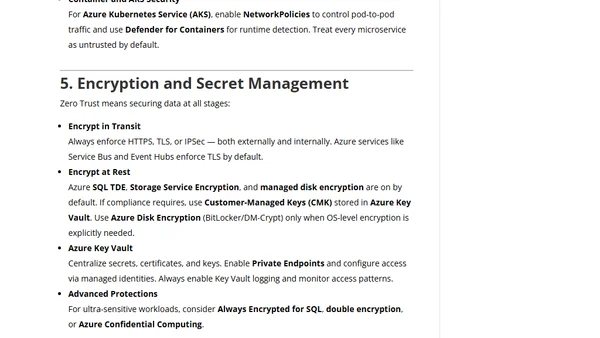
A guide to implementing Zero Trust security principles within Microsoft Azure, covering identity management, network segmentation, and continuous monitoring.
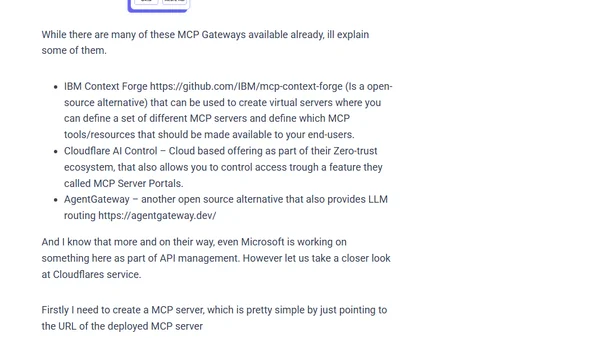
Explains the security risks of community-developed MCP servers and how to centrally manage and secure them using an MCP Gateway.
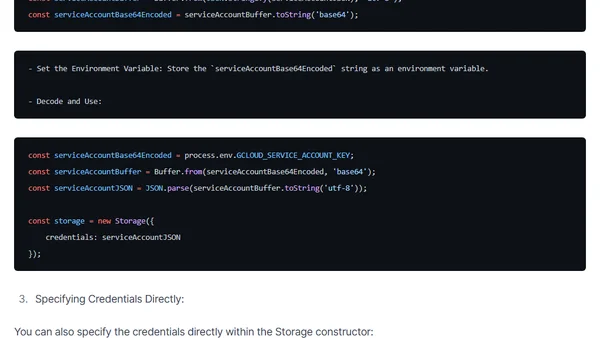
A guide to securely loading and managing Google Cloud Storage service account credentials in Node.js applications, covering JSON files, environment variables, and direct specification.
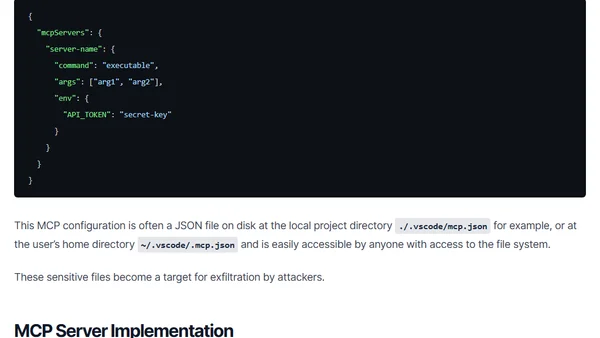
A proposed security evaluation framework for Model Context Protocol (MCP) servers, focusing on configuration and implementation risks for developers.
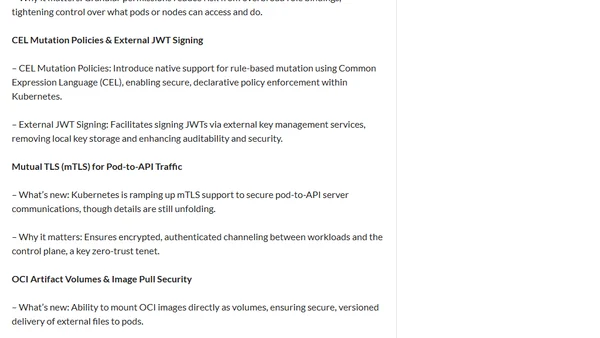
Kubernetes 1.34 focuses on security enhancements, including short-lived registry tokens, scoped anonymous API access, and improved mTLS for pods.
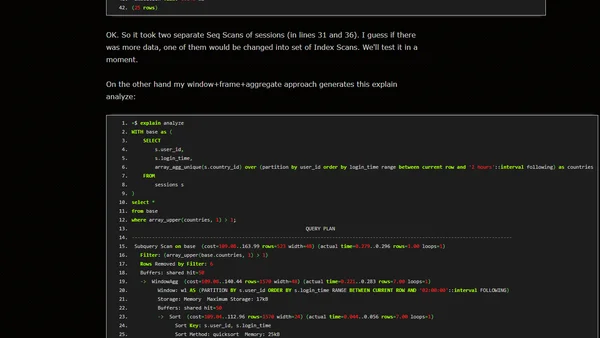
A technical analysis of a SQL interview question about detecting suspicious account logins from multiple countries within a short timeframe.
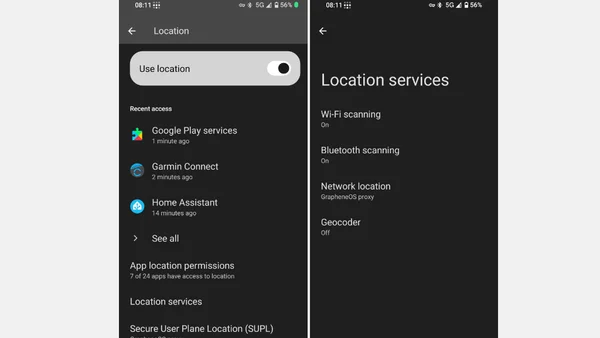
Advocates for GrapheneOS as a privacy-focused, de-Googled Android alternative, detailing its installation and app compatibility.
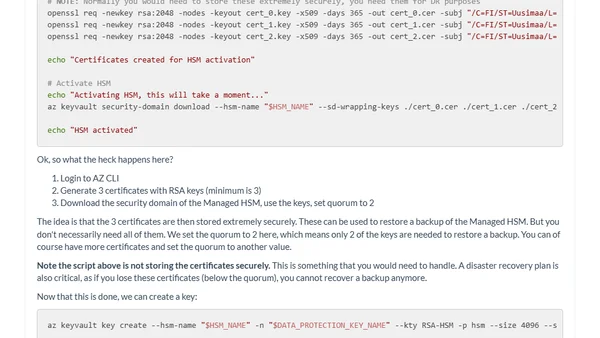
Explains Azure Key Vault Managed HSM, its purpose for regulatory compliance and hardware-level security, and provides a technical setup guide.
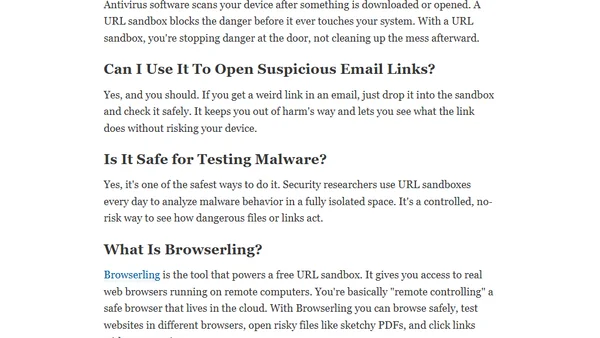
Learn how to use a free URL sandbox to safely open suspicious links and test websites in isolated, remote browsers without risking your device.
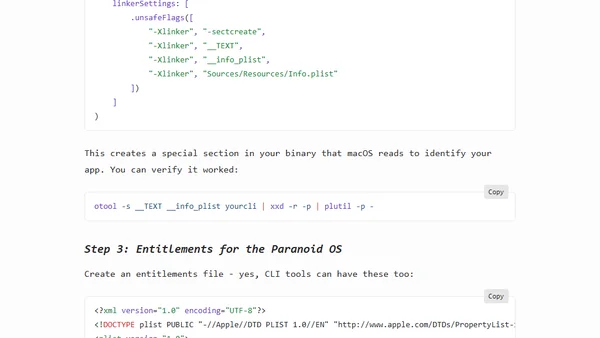
Explains how to embed Info.plist, sign with entitlements, and use undocumented APIs to make AppleScript work in macOS CLI tools without permission dialogs.
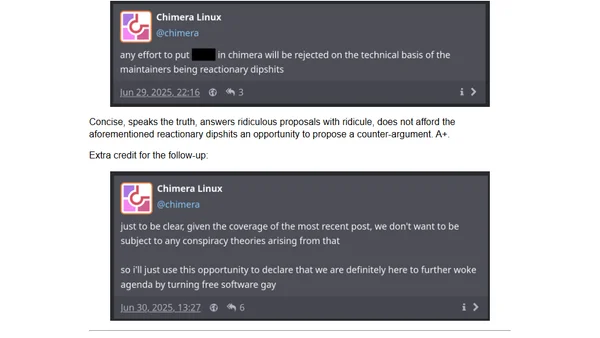
A guide for FOSS community leaders on handling reactionary agitators, contrasting ineffective and effective response strategies.

AI agents' autonomous and probabilistic nature forces stricter security and authorization models, breaking traditional microservice assumptions.
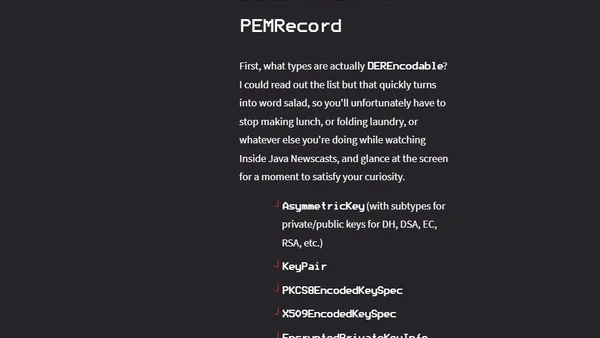
Java 25 introduces a new preview API for easily encoding and decoding cryptographic objects in the PEM text format, addressing a key developer pain point.
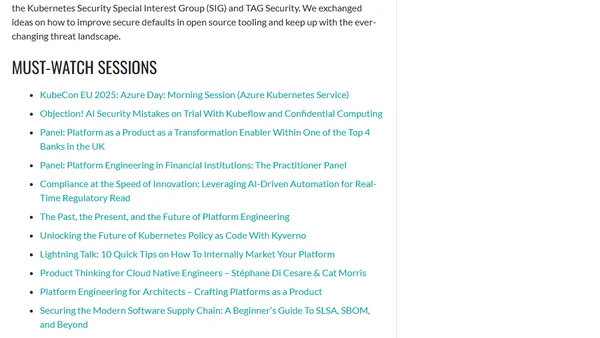
A developer shares their journey to speaking at KubeCon EU 2025, presenting on shifting security down into the platform, and key takeaways from the event.
An engineer critiques the poor security practices in many software companies, highlighting willful neglect and developer resistance to basic safeguards.

A recap of KubeCon NA 2024 highlighting key trends in cloud-native tech: WebAssembly (WASM), Platform Engineering, and Security.
A speaker shares their experience presenting on Kubernetes security at the KubeHuddle Toronto 2024 community conference.