Outsource Your O11y: How To Be A Champion (part 1/3)
A guide on championing third-party observability services to security teams, featuring expert advice in a three-part series.

A guide on championing third-party observability services to security teams, featuring expert advice in a three-part series.
Analyzes security risks in npm package installation, highlighting the dangers of arbitrary code execution and advocating for cautious dependency management.
Highlights from the Node.js Security WG's January 2019 meeting, covering bounty programs and vulnerability database improvements.
A guide for ASP.NET MVC Core developers on identifying and adding CSRF protection to an inherited codebase lacking security measures.
Analyzes the security concerns and evolving best practices for the OAuth2 implicit flow, especially for browser-based applications.
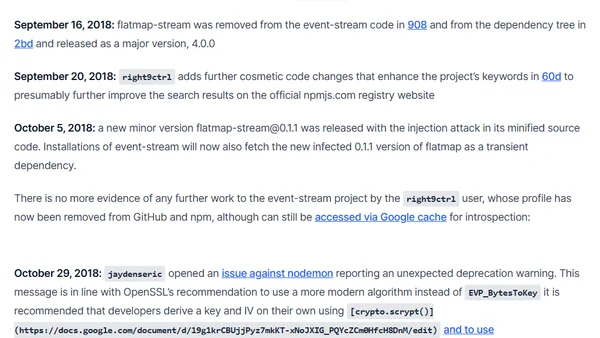
A detailed analysis of the malicious event-stream npm package backdoor, its timeline, and the social engineering attack that led to its inclusion.
Explains the purpose of React's $$typeof property, a security feature using Symbols to prevent XSS attacks in React elements.
A guide on securely storing sensitive configuration data in .NET Core applications, covering sources like User Secrets and Environment Variables.
Explains npm's evolving naming rules to combat typosquatting attacks, detailing case sensitivity and character restrictions for package names.
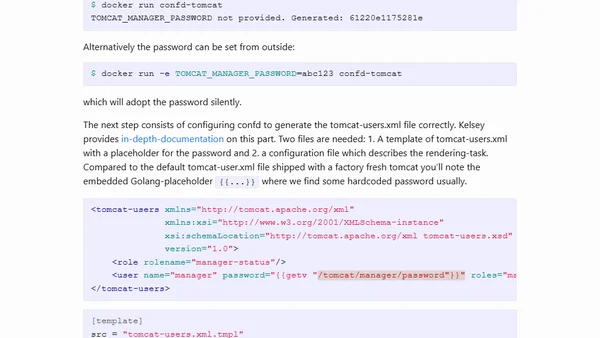
A guide on using confd to dynamically generate Tomcat configuration files and eliminate hardcoded passwords in Docker containers.
A critical analysis of Signal's security model, focusing on its reliance on Google Play Services and resistance to F-Droid distribution.
Explains Bitcoin's security as a spectrum, not binary, using analogies and discussing confirmations, threat models, and double-spend protection.
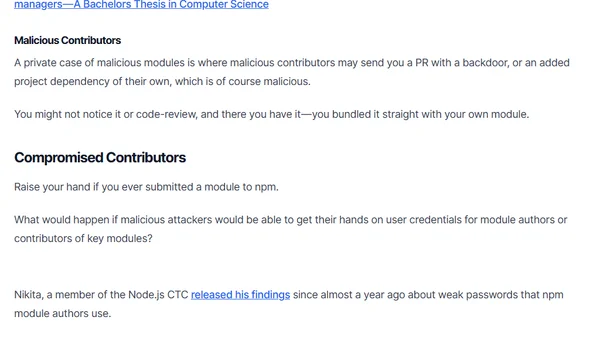
Explains security risks in the npm ecosystem, including malicious modules, typosquatting, and compromised contributors, with mitigation advice.
Explains a key security change in ASP.NET Core 2.1 where authorization filters are combined, altering authentication and role-checking behavior.
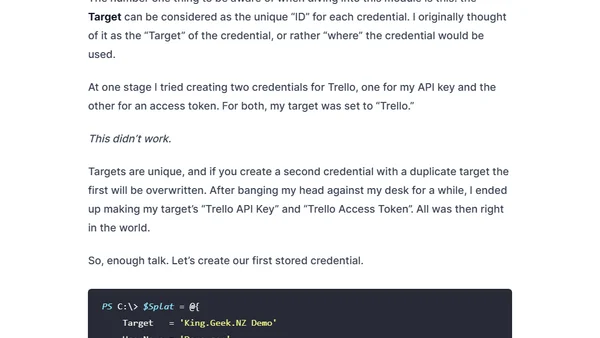
A guide to securely storing and accessing script credentials using the Windows Credential Manager and a PowerShell module.
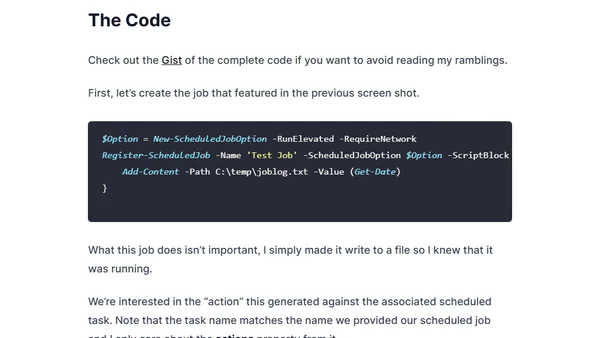
Explains how to specify the full path to PowerShell.exe in Windows Scheduled Jobs for improved security, preventing path interception attacks.
A compilation of technical talks on open source firmware, container security, Intel SGX, and cloud-native infrastructure from 2017-2019.
An introduction to the Node.js Security Working Group, its role in securing Node.js core and modules, and how to get involved.
Explains how flawed Regular Expressions can cause ReDoS attacks, crippling Node.js services with catastrophic backtracking and high CPU usage.
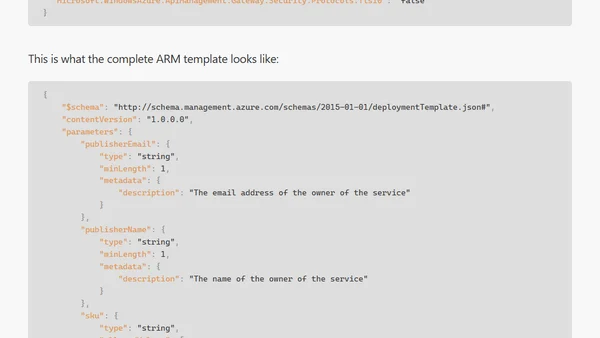
Guide to disabling outdated TLS protocols and ciphers in Azure API Management using ARM templates for improved security.