Claude Cowork Exfiltrates Files
Security researchers found a vulnerability in Claude Cowork allowing data exfiltration via the Anthropic API, bypassing default HTTP restrictions.

Security researchers found a vulnerability in Claude Cowork allowing data exfiltration via the Anthropic API, bypassing default HTTP restrictions.
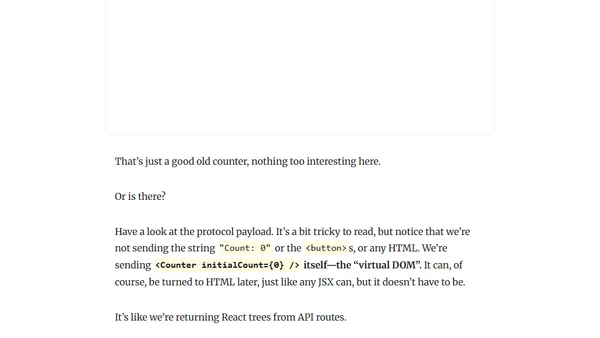
Introduces RSC Explorer, an open-source tool for visualizing and understanding the React Server Components protocol and its streaming behavior.
Security advisory for Datasette open redirect vulnerability fixed in versions 0.65.2 and 1.0a21, including additional features.
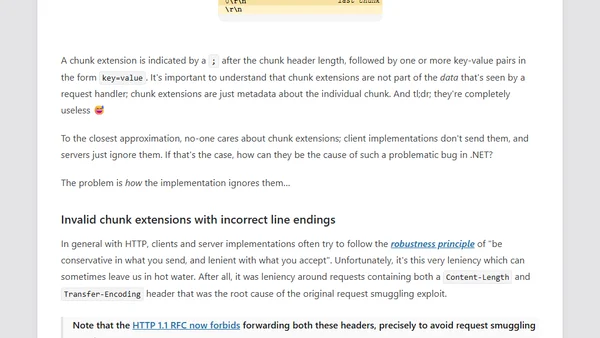
Analysis of CVE-2025-55315, a critical HTTP request smuggling vulnerability in ASP.NET Core with a CVSS 9.9 score, its impact, and mitigation.

A security researcher details a SQL Server auditing bug that allows low-privilege users to exfiltrate sensitive data without detection.
A security researcher details a privacy flaw allowing retrieval of private Facebook friends via Instagram's signup process, and the responsible disclosure timeline.
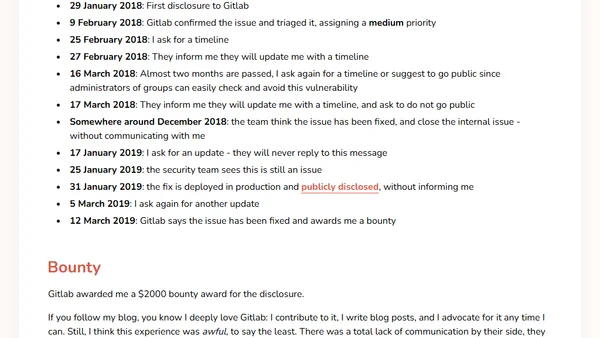
A security researcher details a GitLab access control vulnerability, its disclosure timeline, and the communication issues with GitLab's security team.
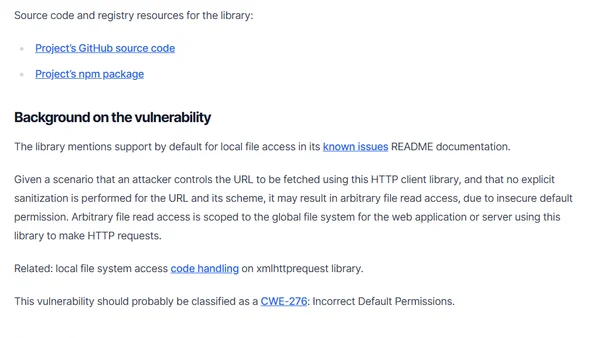
Discloses a Local File Inclusion vulnerability in the xmlhttprequest npm package, allowing arbitrary file reads due to insecure default permissions.
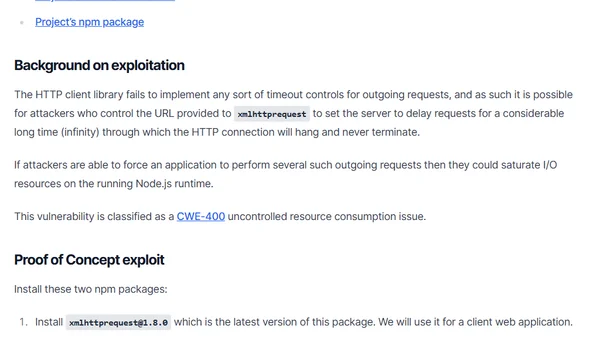
Discloses a CWE-400 uncontrolled resource consumption vulnerability in the xmlhttprequest npm package due to missing timeout controls.
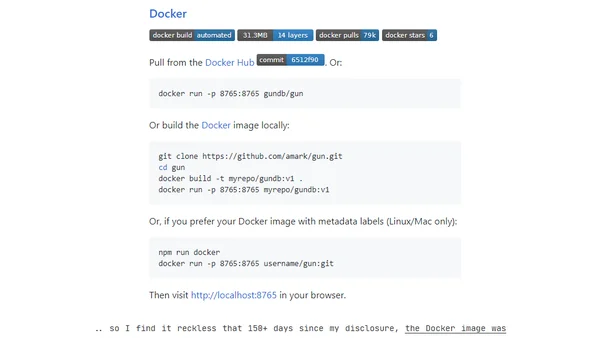
A security researcher details a critical path traversal vulnerability in GunDB that allowed reading server files and stealing AWS credentials.
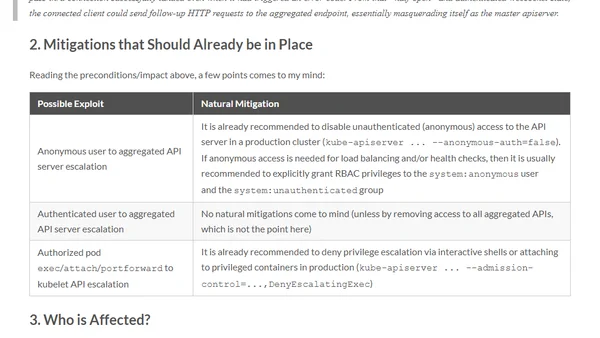
Analysis of CVE-2018-1002105, a critical Kubernetes API server vulnerability allowing privilege escalation and arbitrary backend requests.
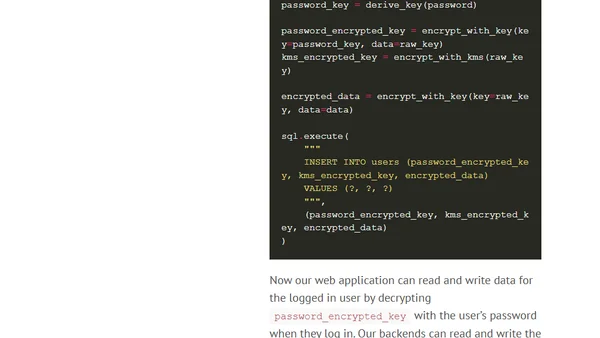
Analyzes the Apache Struts CVE-2017-5638 vulnerability, using the Equifax breach as a case study to explore architectural resilience against RCE attacks.

Explores a disclosure vulnerability in SQL Server's Row- and Cell-Level Security when implemented with views, demonstrating how protected data can be exposed.