Using a Custom Key for Encrypted Cast Model Attributes in Laravel
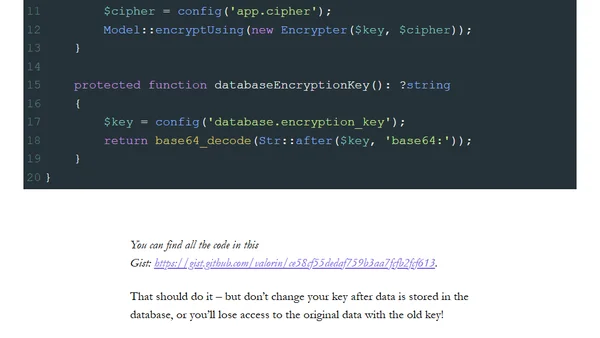
A Laravel security tip explaining how to use a custom encryption key for encrypted model attributes instead of the default app key.

A Laravel security tip explaining how to use a custom encryption key for encrypted model attributes instead of the default app key.
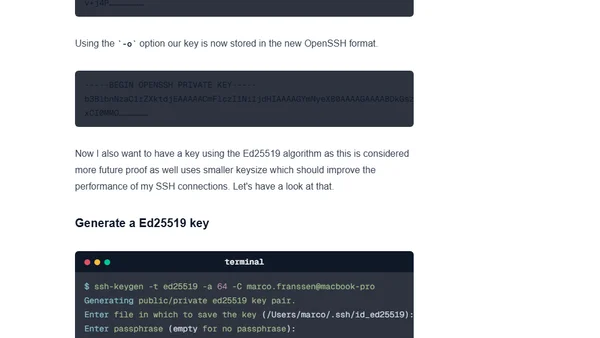
A technical guide comparing SSH key algorithms (RSA, ECDSA, Ed25519) and providing recommendations for generating secure keys in a DevOps context.
A software expert's open letter opposing the EARN IT Act, arguing it threatens essential end-to-end encryption and digital freedoms.
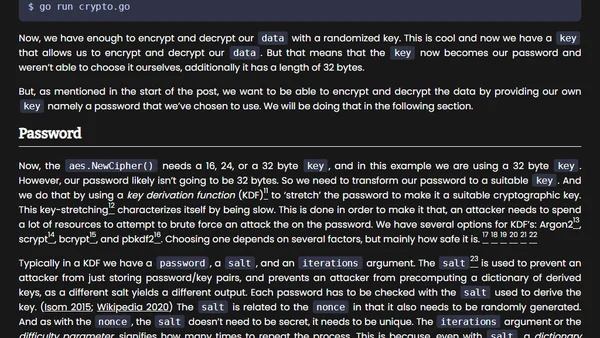
A tutorial on implementing password-based encryption in Go, covering key derivation and AES-GCM for secure data handling.
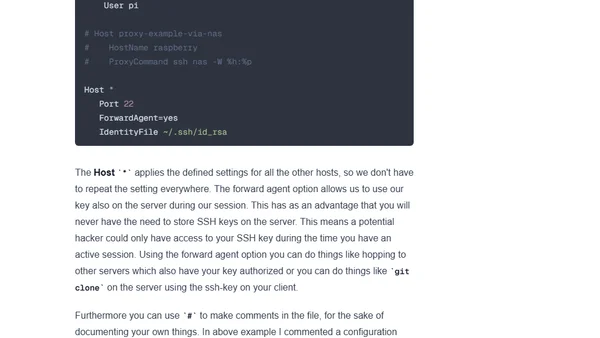
A guide to using SSH efficiently from the terminal, covering key generation, SSH agent setup, and best practices for secure remote access.
Summary of key new features in SQL Server 2019 Standard Edition, including Transparent Data Encryption (TDE) and performance enhancements.
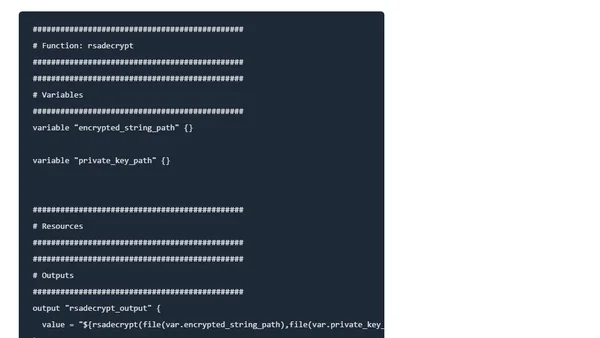
Explains the Terraform rsadecrypt() function for decrypting base64-encoded strings with an RSA key, including a practical example.
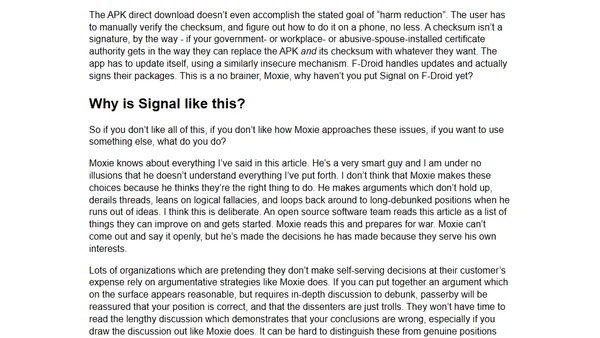
A critical analysis of Signal's security model, focusing on its reliance on Google Play Services and resistance to F-Droid distribution.
A technical overview of Telegram's features, including its open API, encryption, bots, cross-platform sync, and large group capabilities.
A technical critique of Deputy AG Rosenstein's speeches linking encryption to cybersecurity threats, arguing his position misrepresents the role of encryption in major breaches.
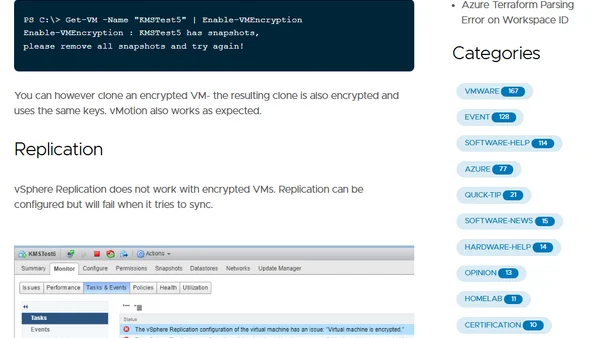
Explores technical limitations of vSphere Encryption, including restrictions on encrypting powered-on VMs, snapshots, and replication.
Explains why forward secrecy is crucial for modern encryption, contrasting GPG's long-term key model with the Signal Protocol's ephemeral keys.
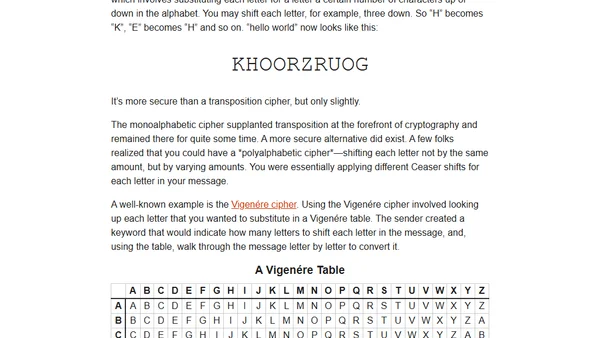
A reflection on teaching basic cryptography to children, highlighting the importance of usable security through historical ciphers like the rail fence and Caesar cipher.
A guide to checking BitLocker encryption status on remote Windows computers using PowerShell and the manage-bde command.
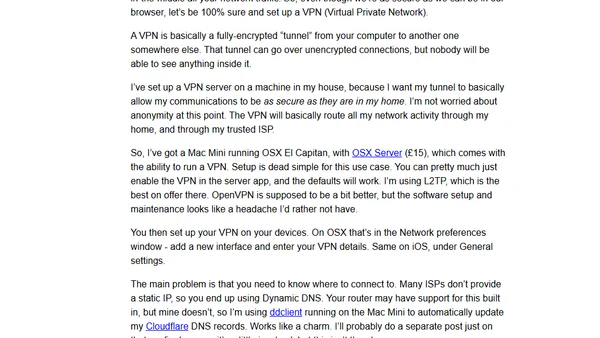
A guide to enhancing network security and privacy on macOS, covering ISP choice, browser extensions, and search engine alternatives.
Explores the new Protect/Unprotect-CmsMessage cmdlets in PowerShell V5 for DSC credential encryption, detailing upgrade challenges.
Analysis of the Apple vs FBI encryption case, arguing that longer passcodes can maintain iPhone security even if Apple loses.
A detailed guide to the author's personal security setup on OSX, focusing on password management with KeePass and related tools.
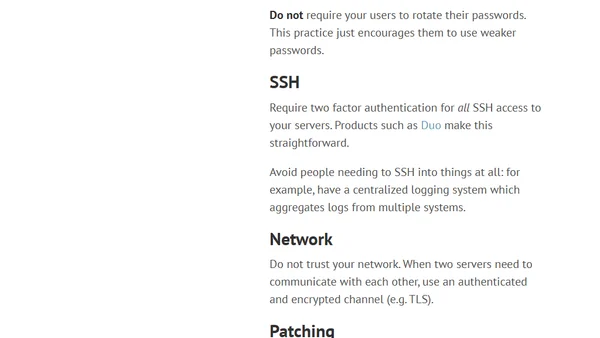
Practical advice for enhancing company security, covering password storage, SSH access, network encryption, patching, and developer education.
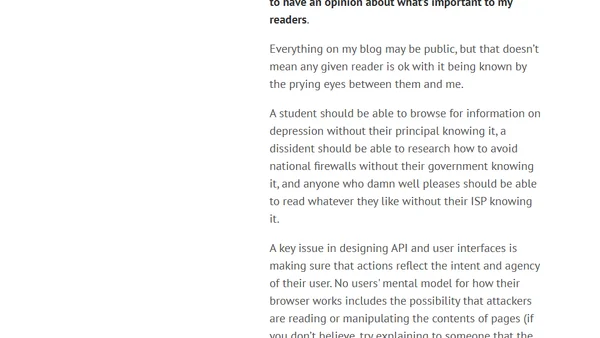
The author argues that all websites should use HTTPS by default to protect user privacy and security, making HTTP unethical.