IntSights Active Directory Integration
How IntSights' Active Directory Integration helps organizations detect and remediate compromised employee credentials from data breaches.

How IntSights' Active Directory Integration helps organizations detect and remediate compromised employee credentials from data breaches.
Explains the subtle but critical security difference between SMS-based Two Factor Authentication (2FA) and insecure SMS-based account recovery.
A detailed analysis of a blackmail email scam demanding a $2000 Bitcoin payment to prevent the release of compromising material.
A 2018 update on Rubrik's expansion from backup appliances to data management (Polaris) and anti-malware (Radar) platforms.
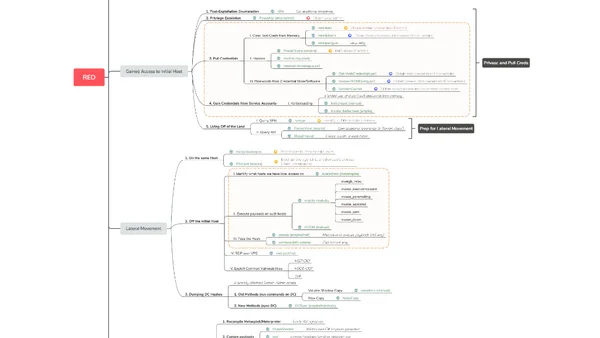
A mind map summarizing the red teaming methodology and techniques from 'The Hacker Playbook 3' for cybersecurity professionals.
A practical guide to finding and exploiting hosts vulnerable to the libSSH authentication bypass (CVE-2018-10933).
Analyzes a famous 2016 phishing attack to argue that modern security hinges on human error, not just technical defenses.
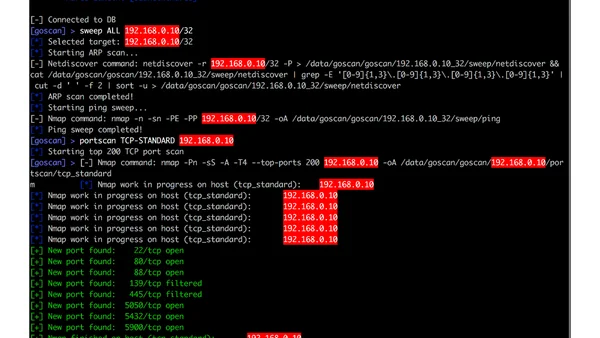
A developer introduces GoScan, a network scanner tool written in Go, and explains how learning Go led to its creation and features like historical port tracking.
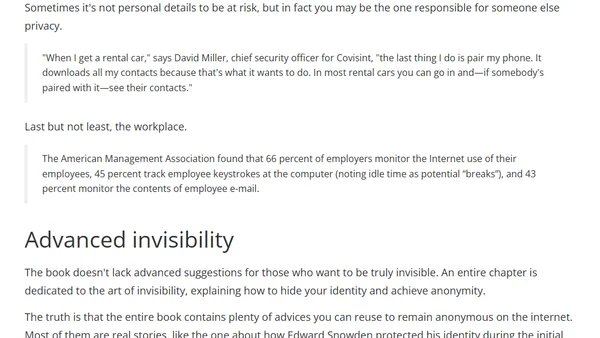
A review of Kevin Mitnick's book 'The Art of Invisibility', which explores digital privacy threats and practical protection strategies for everyone.
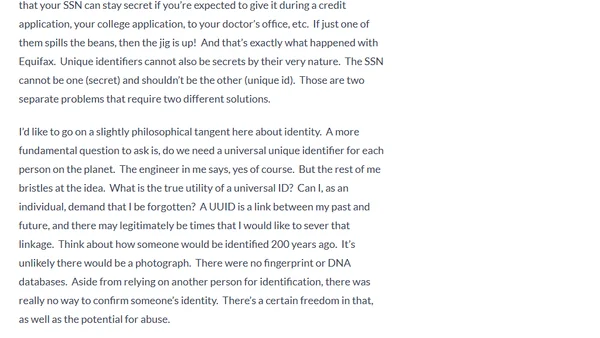
The article critiques the use of SSNs as both a secret and a universal ID, arguing it's a core problem behind data breaches like Equifax.
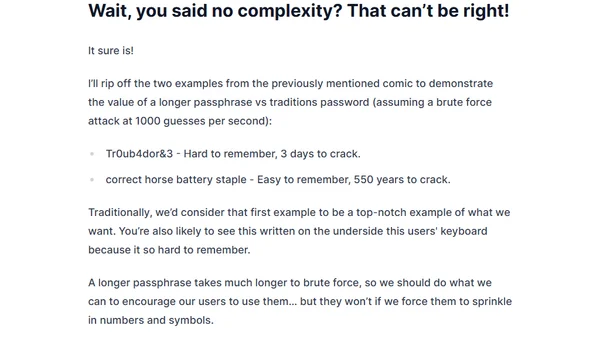
Analysis of new NIST password guidelines advocating for longer passphrases over complex, frequently changed passwords.
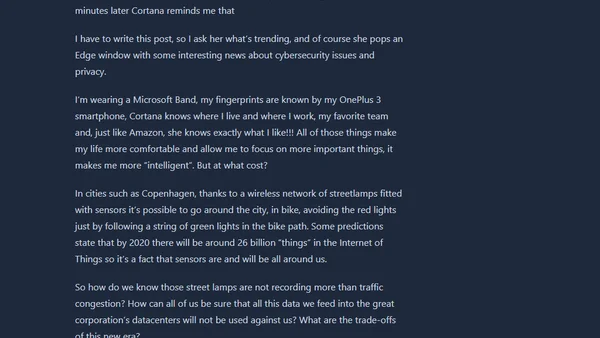
A personal reflection on the trade-offs between convenience and privacy in an era of AI, IoT, and pervasive data collection.
Discusses the inevitability of website breaches, lists major hacks, and explains how to assess your risk and prepare for security incidents.
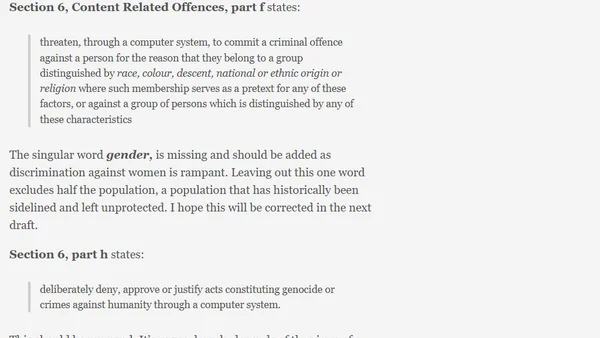
Analysis of Kenya's proposed ICT law amendments, focusing on cybersecurity, electronic transactions, and potential issues in the draft regulations.
Essential security practices for freelance developers, covering device locking, password management, and multi-factor authentication.
A cautionary analysis of the Code Spaces hack, explaining how similar cloud security breaches can happen on AWS, Azure, or any host, and outlining basic mitigation steps.
A tech news roundup covering a wireless medical chip breakthrough, the 40th anniversary of the Rubik's Cube, and issues in web payments and cybersecurity.
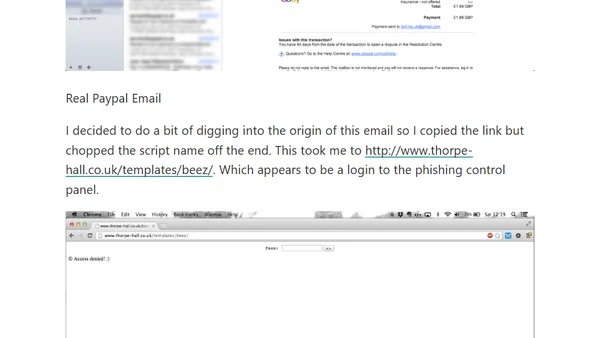
A detailed analysis of a convincing PayPal phishing email, including how to spot the fakes and the discovery of a compromised website.
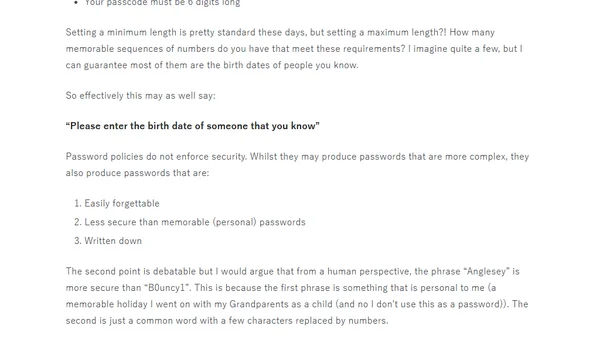
Critique of counterproductive password policies, using Barclaycard as an example, and suggestions for more user-friendly, secure authentication.
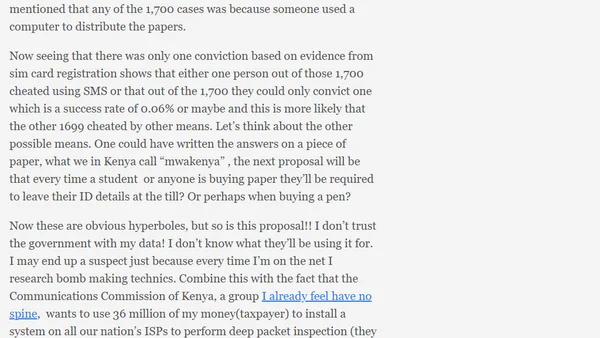
Critique of Kenyan government proposals for internet cafe user logging and ISP deep packet inspection, framed as privacy overreach in the name of cybersecurity.