Hunt for and Exploit the libSSH Authentication Bypass (CVE-2018-10933)
Read OriginalThis technical article provides a step-by-step guide for security professionals to hunt for and exploit the critical libSSH authentication bypass vulnerability (CVE-2018-10933). It details methods to identify SSH services, fingerprint libSSH instances, confirm vulnerability, and gain shell access using both manual techniques and Metasploit, including scripts and Kibana visualizations.
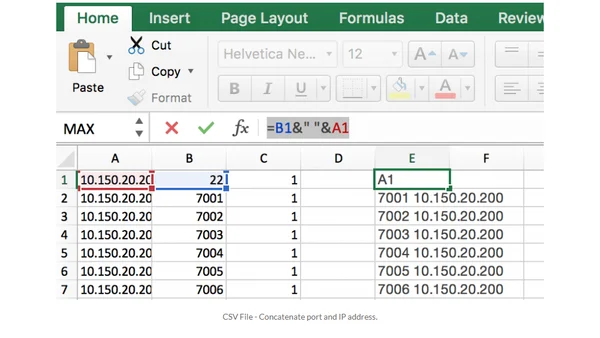
Comments
No comments yet
Be the first to share your thoughts!
Browser Extension
Get instant access to AllDevBlogs from your browser
Top of the Week
1
Quoting Thariq Shihipar
Simon Willison
•
2 votes
2
Top picks — 2026 January
Paweł Grzybek
•
1 votes
3
In Praise of –dry-run
Henrik Warne
•
1 votes
4
Deep Learning is Powerful Because It Makes Hard Things Easy - Reflections 10 Years On
Ferenc Huszár
•
1 votes
5
Vibe coding your first iOS app
William Denniss
•
1 votes
6
AGI, ASI, A*I – Do we have all we need to get there?
John D. Cook
•
1 votes
7
Dew Drop – January 15, 2026 (#4583)
Alvin Ashcraft
•
1 votes