Essential Cryptography for JavaScript Developers
Announcing a new book for JavaScript developers on practical cryptography, covering hashing, encryption, and digital signatures.

Announcing a new book for JavaScript developers on practical cryptography, covering hashing, encryption, and digital signatures.
Monthly update on free software projects including godocs.io release, programming language progress, and SourceHut platform improvements.

A developer's monthly update on their programming language's progress, including new cryptography features, standard library modules, and team expansion.
A developer's monthly update on progress in a new programming language, including cryptography, C library linking, SDL2 bindings, and work on SourceHut's GraphQL API.
A developer's monthly update on FOSS projects, including SourceHut's anniversary, a new programming language delay, and progress on various tools.
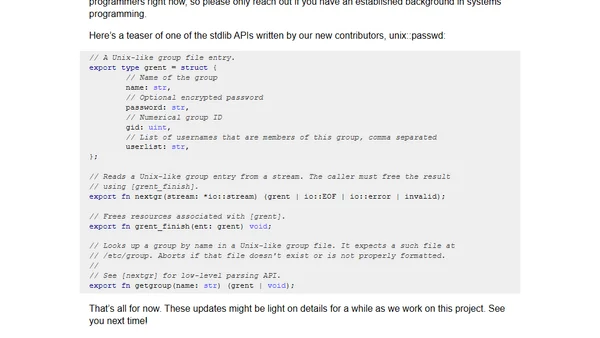
A developer's monthly update focusing on a private programming language project, seeking experienced contributors for cryptography, date/time, and networking tasks.
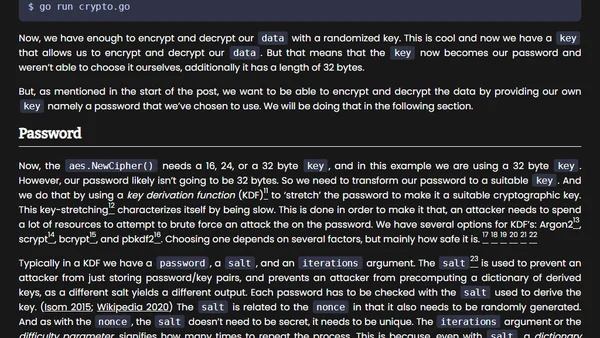
A tutorial on implementing password-based encryption in Go, covering key derivation and AES-GCM for secure data handling.
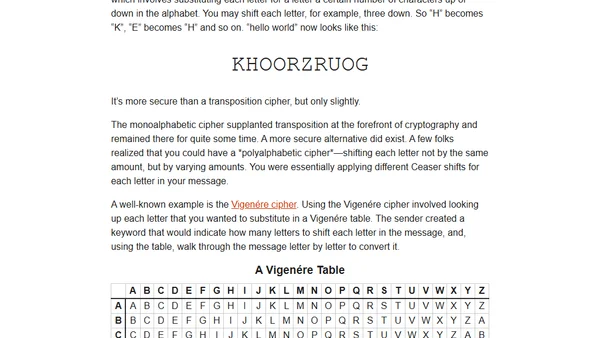
A reflection on teaching basic cryptography to children, highlighting the importance of usable security through historical ciphers like the rail fence and Caesar cipher.
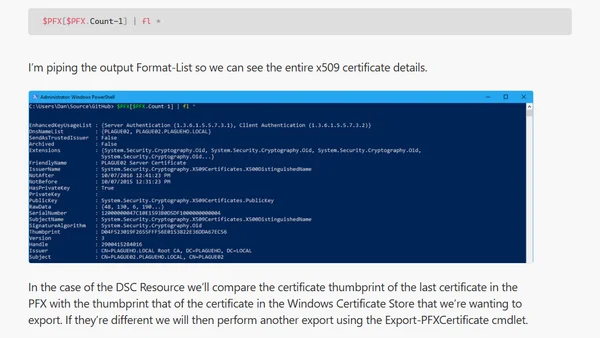
A technical guide on using PowerShell to read, analyze, and validate certificates within PFX files, including trust chain inspection.
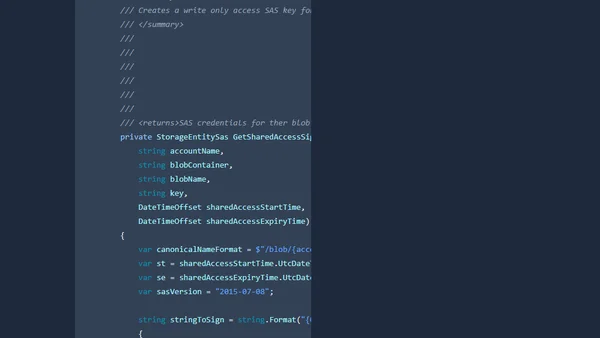
A technical guide on generating write-only Shared Access Signature (SAS) keys for Azure Blob Storage using .NET Core.
A developer explores parallel computing by writing a Go program to brute-force crack the WWII Enigma cipher, inspired by Alan Turing's work.
Analyzes the TV show Continuum to discuss real-world surveillance, IoT security risks, and the erosion of privacy in a connected world.
A technical talk on the challenges and proper implementation of TLS/SSL for secure communications, presented at multiple Python conferences.
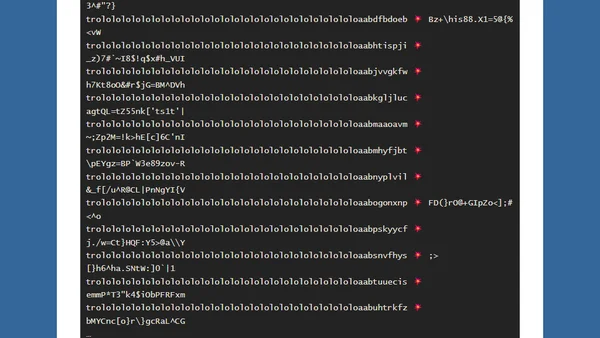
Explains how and why two different strings produce the same PBKDF2-HMAC-SHA1 hash, detailing the cryptographic property behind the collision.

An article explaining cryptography and data security concepts, including a notable section on steganography.
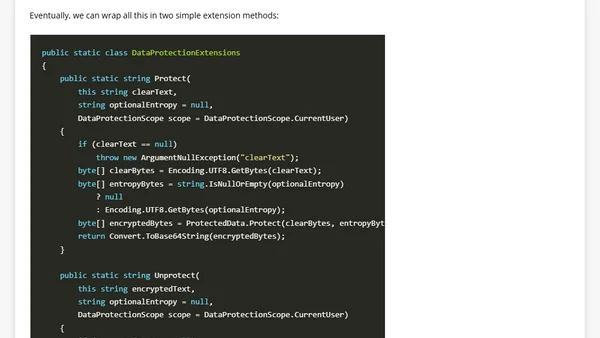
Explains how to securely store passwords in .NET using Windows Data Protection API (DPAPI) and the ProtectedData class.