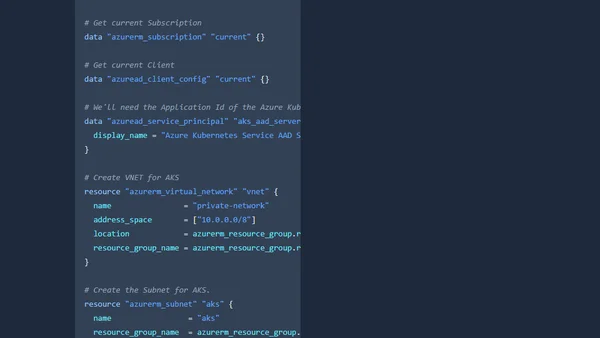
AKS: Disable local accounts with Terraform
Guide to disabling local accounts on Azure Kubernetes Service (AKS) clusters using Terraform for improved security and auditability.

Guide to disabling local accounts on Azure Kubernetes Service (AKS) clusters using Terraform for improved security and auditability.
A blogger shares their 2022 goals for writing, media production, and software development, focusing on accountability and personal growth.
A Laravel security tip emphasizing the critical importance of validating all user input to prevent unexpected behavior and security vulnerabilities.
Explains why using user accounts for Azure Logic App connections is a security risk and recommends using managed identities instead.
Signal's new sponsorship model is a sustainable alternative to ad-based revenue, ensuring user privacy and long-term viability.
Using Python's pytm framework to threat model the security flaws in the fictional systems of Jurassic Park.
Analyzes the security flaws in Flatpak's all-or-nothing permissions model and compares it to more granular systems like iOS.
A technical guide explaining how to implement authentication and authorization in any backend language or framework, covering user models, signup/login routes, and session vs JWT auth.
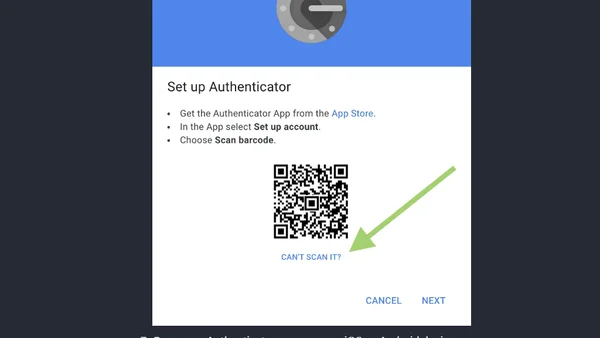
A technical guide on automating the bypass of two-factor authentication (2FA) for use in scripts and automated testing.
A roundup of DevOps news and tools, including GitHub Releases beta, npm security updates, composite actions, and container vulnerability scanning.
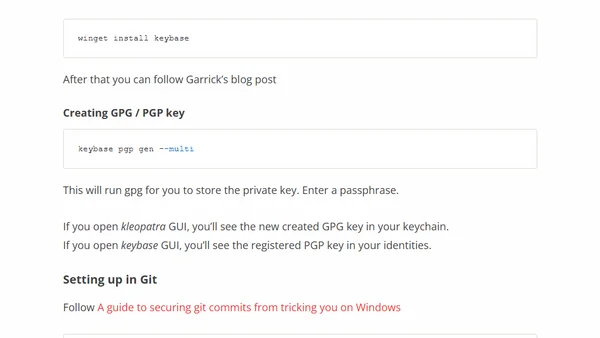
A step-by-step guide to setting up signed Git commits using Keybase and GPG on Windows 10, including installation and configuration.
A quick guide to manually patching the OMIGOD vulnerability in Azure-hosted Linux VMs by updating the OMI package.
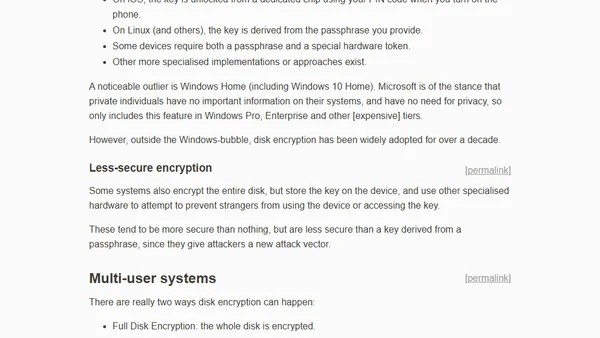
Explains disk encryption basics for non-technical users, covering why it's needed, how it works, and different implementation types.
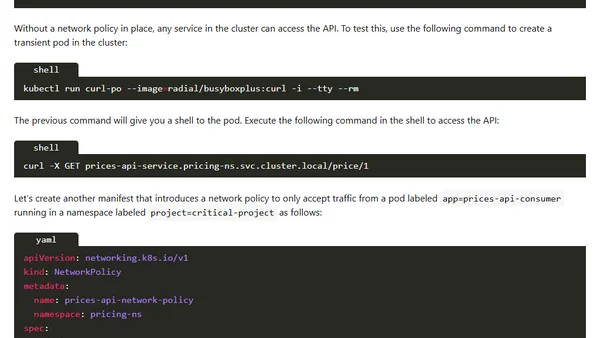
Explains how to use Kubernetes Network Policies to restrict communication between microservices for improved security.
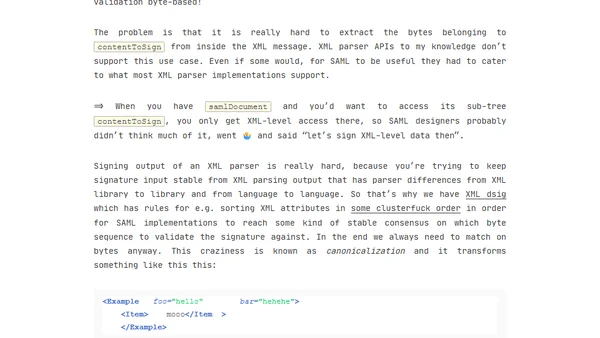
A critical analysis of SAML security, arguing its design is inherently insecure due to malleable signature computation, with examples of real-world vulnerabilities.
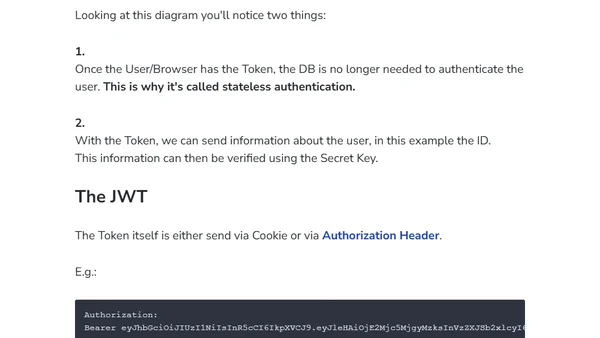
A beginner-friendly introduction to JSON Web Tokens (JWT), explaining their structure, use for stateless authentication, and basic flow.
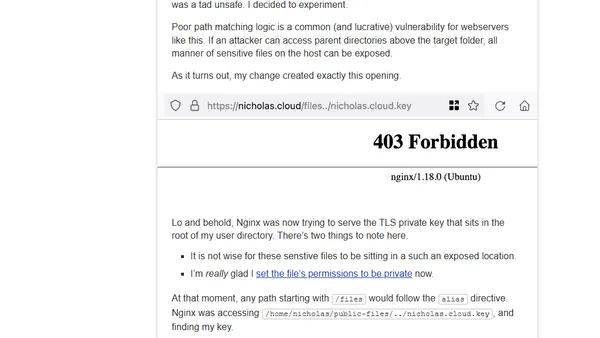
A developer's cautionary tale about a security vulnerability introduced by a seemingly minor change to an Nginx alias directive configuration.
Critique of npm audit's flaws, arguing its default rollout was rushed and harmful to front-end development workflows.
Explores the benefits and security advantages of using Generation 2 virtual machines in Azure, focusing on the upcoming Trusted Launch feature.
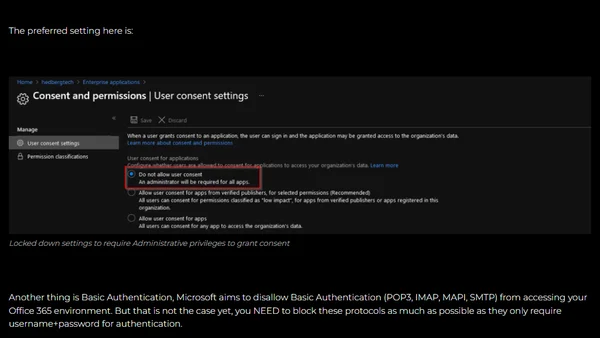
A security-focused guide listing eight critical areas to monitor and secure in Azure Active Directory to prevent breaches.