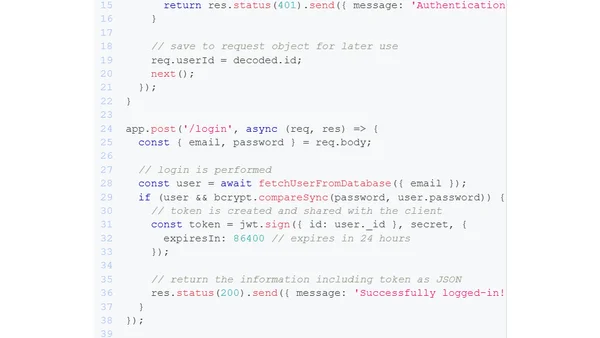
Sessions vs Tokens: How to authenticate in Node.js
A technical comparison of session-based and token-based authentication methods, with implementation examples and best practices for Node.js.

A technical comparison of session-based and token-based authentication methods, with implementation examples and best practices for Node.js.
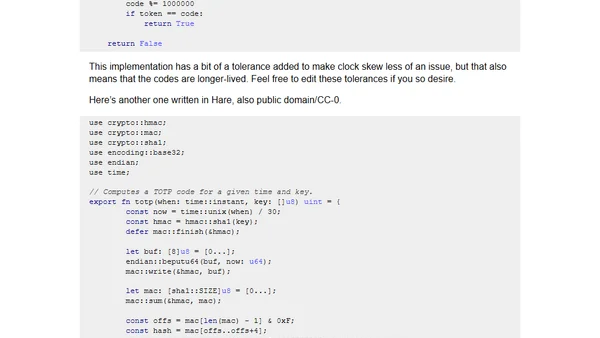
A technical guide explaining how to implement TOTP-based two-factor authentication, including code examples in Python and Hare.
Discusses security risks in Angular HTTP interceptors, especially when exposing authentication tokens, and provides examples from common implementations.
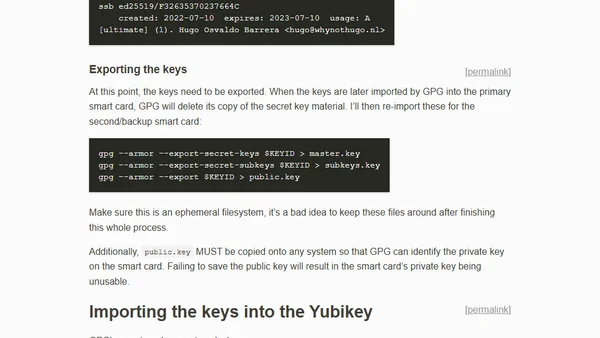
A technical guide on setting up and using a Yubikey hardware token for GPG encryption and signing, covering key generation and smart card configuration.
A comprehensive guide to implementing OAuth 2.0 authorization with multiple providers (Google, GitHub, Amazon) in a Node.js backend using Passport.js.
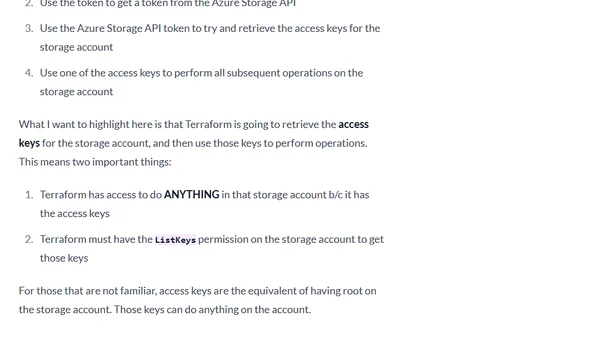
Guide on using OIDC authentication with Terraform's AzureRM backend to secure GitHub Actions workflows and manage storage permissions.
A guide on transferring a Google Fi eSIM to a new iPhone, including steps and security considerations for travelers.
A comprehensive guide to all OAuth 2.0 grant types, explaining their flows and use cases for secure application authorization.
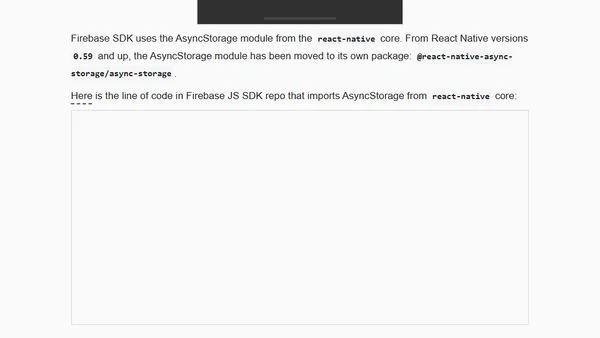
A guide to fixing AsyncStorage warnings when using Firebase JS SDK with React Native by properly configuring the auth persistence layer.
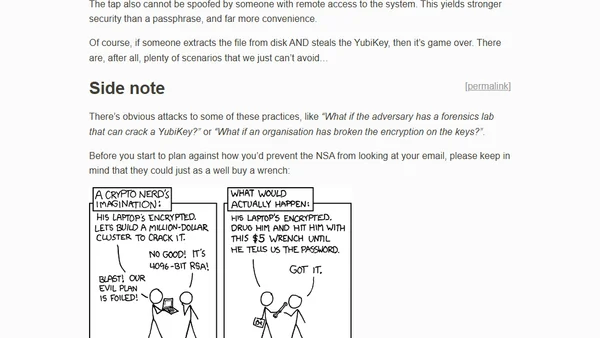
A developer shares practical tips and warnings for using YubiKeys for 2FA, SSH authentication, and sudo prompts to enhance security.
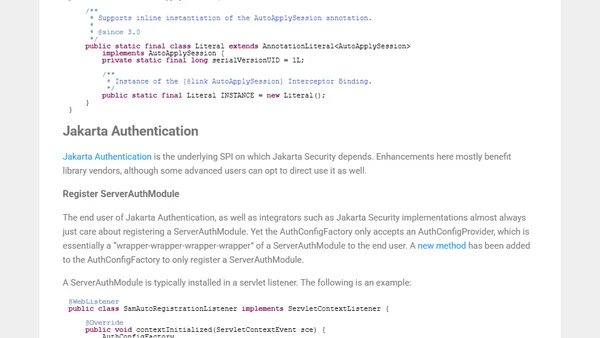
Jakarta Security 3's major update introduces OpenID Connect authentication, alongside its core API and underlying SPIs for Jakarta EE.
A guide to implementing efficient authentication state reuse in Playwright end-to-end tests to avoid repeated logins and speed up test suites.
A technical guide explaining how to authenticate and connect to an Azure AD B2C tenant using Azure CLI and PowerShell Az module.
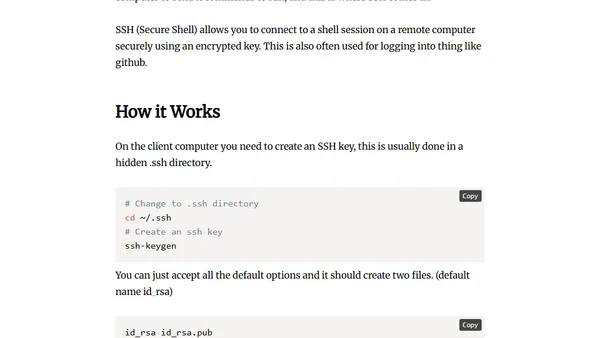
Explains SSH (Secure Shell), its purpose for secure remote computer connections, and how to generate and use SSH keys.
A critical analysis of Plaid's security model, arguing its credential collection widget undermines decades of online banking security best practices.
Exploring Azure AD B2C's 'Seamless Migration' feature for moving user identities to the cloud with minimal friction.
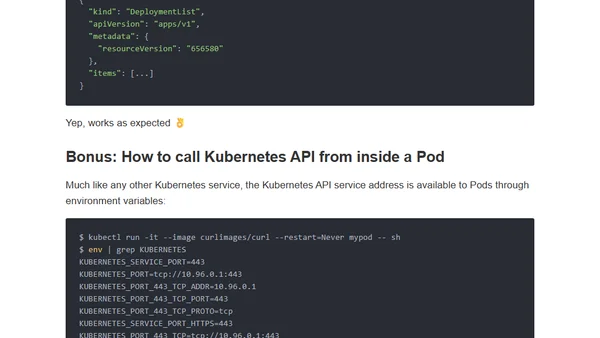
A guide to calling the Kubernetes API directly using HTTP clients like curl, covering authentication, server discovery, and CRUD operations.

A tutorial on implementing a one-to-many database relationship with user authentication using the Masonite framework in Python.
A developer-focused guide on password management best practices, including secure storage, length recommendations, and multi-factor authentication.
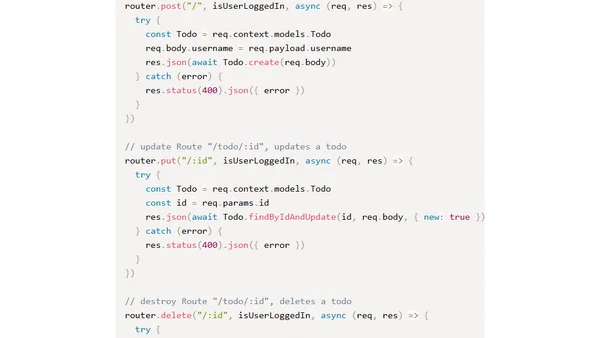
A tutorial on implementing JWT authentication in an Express.js API, with examples using both MongoDB and PostgreSQL databases.