Connecting to a Private AKS Cluster with Azure Bastion – No Jump Box Needed!
A guide on using Azure Bastion to securely connect to a private AKS cluster without needing a jump box VM, simplifying access and management.

A guide on using Azure Bastion to securely connect to a private AKS cluster without needing a jump box VM, simplifying access and management.
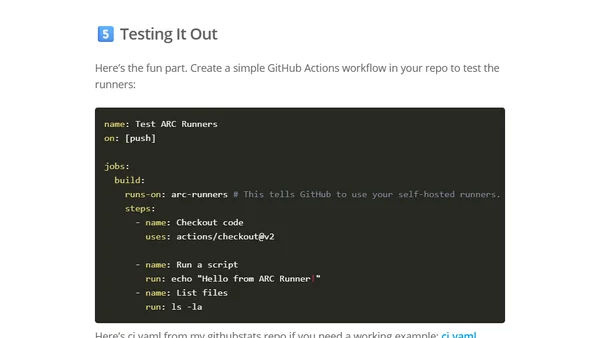
A guide to deploying self-hosted GitHub Actions runners on a home Kubernetes cluster using the Actions Runner Controller (ARC).
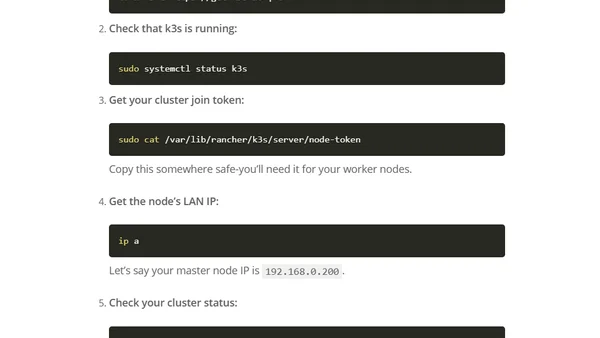
A guide to building a powerful home Kubernetes cluster using old laptops, Ubuntu Server, and the lightweight k3s distribution for development and CI/CD.
Analyzes performance and reliability challenges of Kubernetes List API calls at massive scale, explaining high-risk patterns and recent improvements.
![Any kubectl command throws "Unhandled Error" err="couldn't get current server API group list: Get "http://localhost:8080/api?timeout=32s": dial tcp [::1]:8080: connect: connection refused" - what do?](https://alldevblogs.blob.core.windows.net/thumbs/article-cfa76fb7e918-full-787fa002.webp)
Fixing kubectl connection errors when commands fail with 'connection refused' on localhost:8080.
Explores using SPIFFE workload identity for AI agents, highlighting technical gaps in current Kubernetes implementations for non-deterministic agent behavior.
Explains how Envoy Proxy enables Zero Trust Architecture in cloud-native environments through mTLS, RBAC, and centralized traffic control.
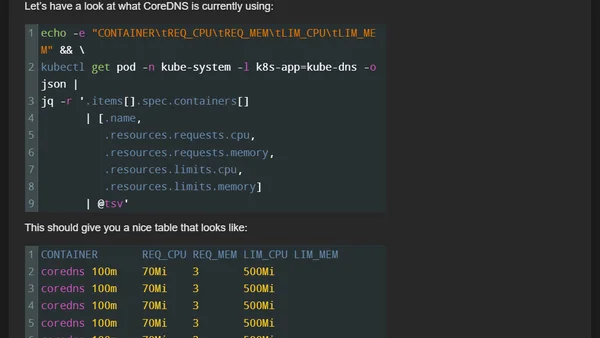
Explains how to use Azure Kubernetes Service's new preview feature for cost-optimized scaling of system add-ons using the managed Vertical Pod Autoscaler.
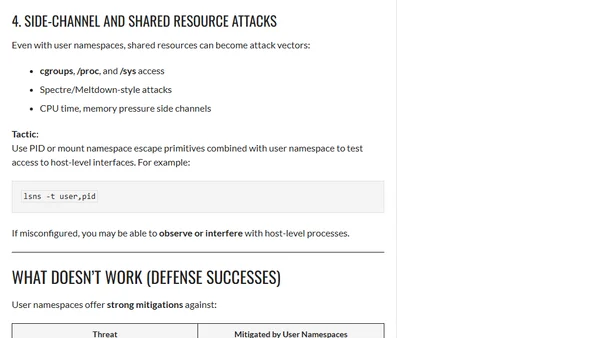
Analyzes Kubernetes User Namespaces from an offensive security perspective, covering isolation benefits, potential misconfigurations, and escape vectors.
A guide to fixing the 'Identity not found' error when logging into Azure CLI using AKS workload identity.
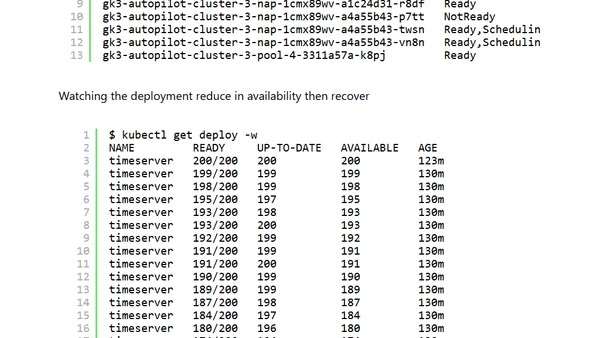
A guide to simulating a zonal failure on Google Kubernetes Engine (GKE) Autopilot using kubectl commands and a custom script.
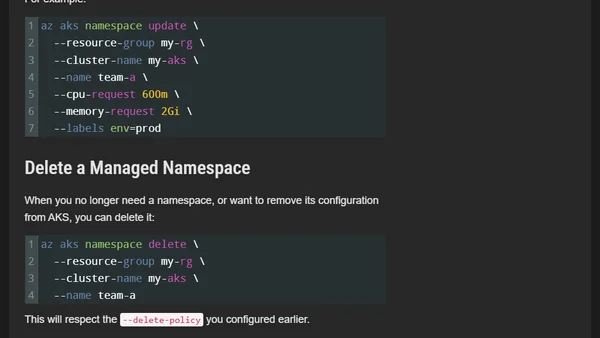
Explores the new Managed Namespaces preview feature in Azure Kubernetes Service (AKS), covering its purpose and how to use it.
A developer shares their journey to speaking at KubeCon EU 2025, presenting on shifting security down into the platform, and key takeaways from the event.

A recap of KubeCon NA 2024 highlighting key trends in cloud-native tech: WebAssembly (WASM), Platform Engineering, and Security.
A speaker shares their experience presenting on Kubernetes security at the KubeHuddle Toronto 2024 community conference.

Compares two Kubernetes tools for integrating external secret managers: Secrets Store CSI Driver and External Secrets Operator.
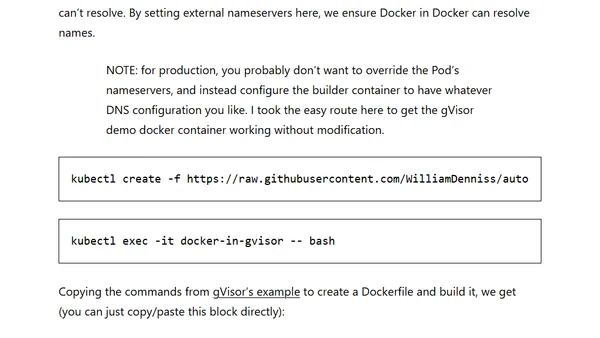
A guide to running Docker-in-Docker workloads securely on GKE Autopilot using the gVisor sandbox, including cluster configuration steps.

A developer shares their experience and key takeaways from attending and speaking at Cloud Native Security Con 2024 in Seattle.
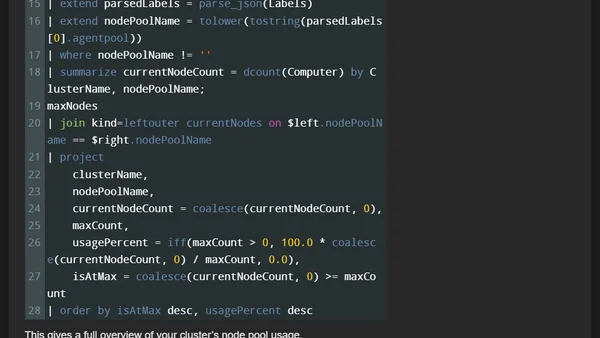
Guide to creating a dynamic Azure alert for AKS node pools that triggers when a pool reaches its maximum autoscaling node count.
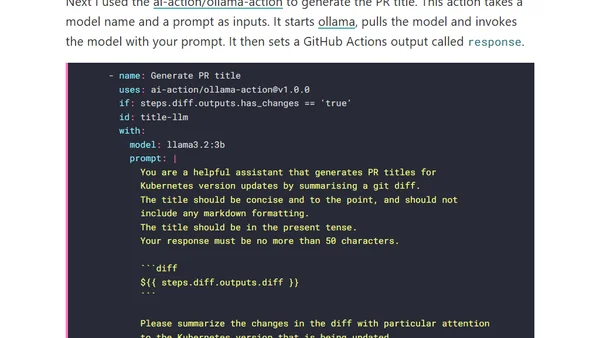
A developer explains how to use an open-source LLM within a GitHub Actions workflow to generate descriptive titles for automated Pull Requests.