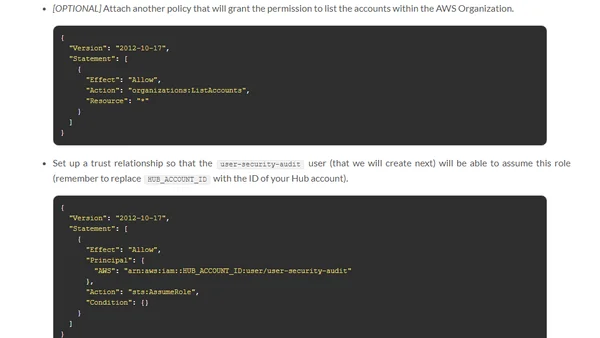
Cross Account Auditing in AWS and GCP
A guide to setting up cross-account security auditing for AWS and GCP environments using hub-and-spoke models and IAM roles.

A guide to setting up cross-account security auditing for AWS and GCP environments using hub-and-spoke models and IAM roles.
Guide to integrating Azure App Service with Azure Front Door Premium using Private Link for secure, private connectivity without complex DNS or endpoint management.
Microsoft's new SC-900 Security Fundamentals certification covers cloud security, identity, and compliance concepts for IT professionals.
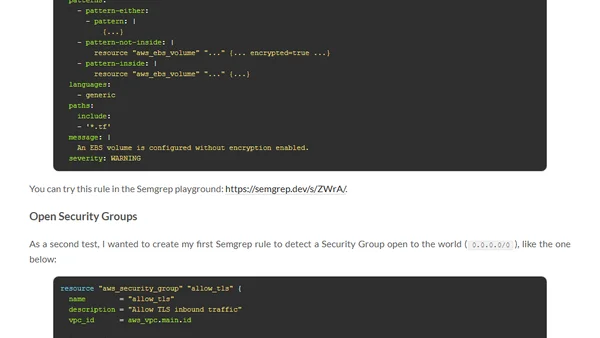
Explores using Semgrep, a static analysis tool, to find security vulnerabilities in Infrastructure as Code like Terraform and Kubernetes configurations.

Announcing CloudSecDocs.com, a public collection of technical notes and cheatsheets for cloud-native technologies, DevOps, and security.
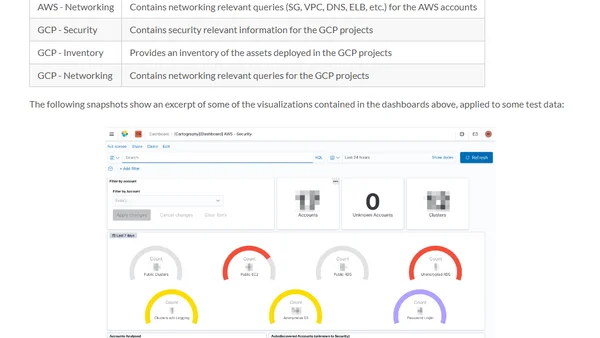
A guide to integrating Cartography with Elasticsearch for continuous monitoring and drift detection of cloud assets in multi-cloud environments.

A guide to essential security practices for protecting SQL Server instances running on Azure Virtual Machines, focusing on encryption and access controls.
Explores secure credential management in Azure using Managed Identities to avoid storing secrets in code or configuration.
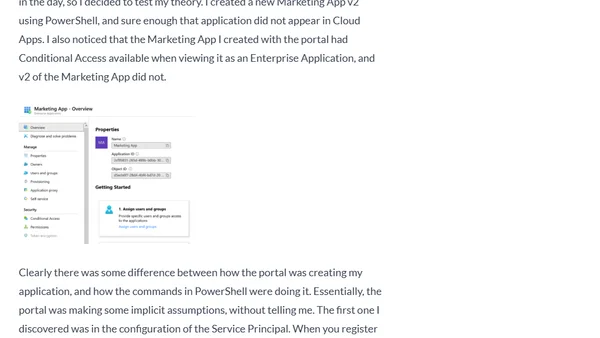
A technical guide on troubleshooting Conditional Access policies for Azure AD applications, focusing on why some apps don't appear in policy menus.
Explores secure credential management for cloud apps using Azure Managed Identities to avoid hardcoded secrets in code and source control.
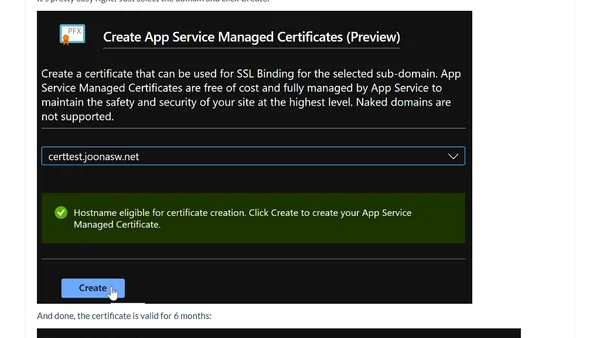
Guide to enabling free, managed HTTPS certificates for custom domains in Azure App Service, including limitations and setup steps.
A guide to getting started with Azure Sentinel, Microsoft's cloud-native SIEM and SOAR solution, covering setup, data connectors, and initial configuration.
Announcing a new weekly newsletter curating cloud-native security news and updates for professionals.
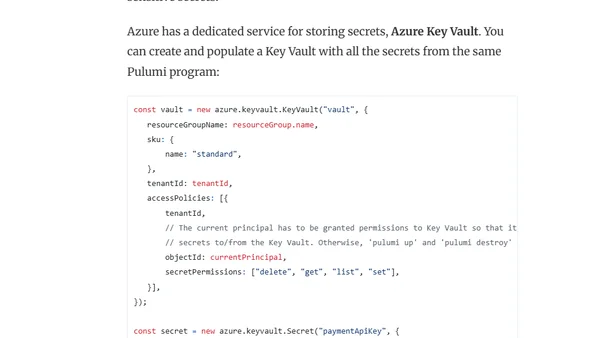
A guide exploring seven methods for securely managing application secrets and configuration values in .NET Core applications deployed on Azure.
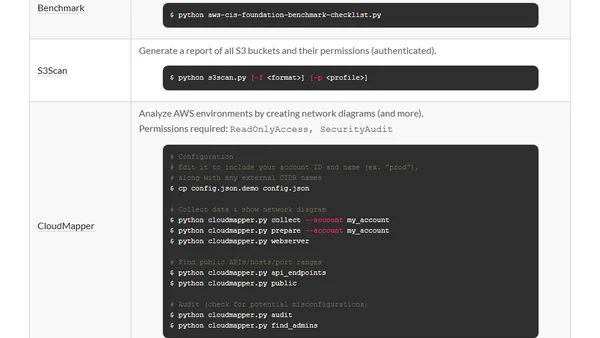
A curated list of security auditing and offensive tools for Docker, Kubernetes, AWS, GCP, and Git, with usage guides and an Ansible role.
A developer's critical questions for evaluating cloud providers, focusing on problem-solving, security implementation, and customer-driven development.
Explores how Conway's Law reveals communication gaps between hardware, firmware, kernel, and software layers, using examples like Spectre and Kubernetes.
Summary of July 2018 updates to Azure AD Managed Service Identity, including new user-assigned identities and supported services.
An analysis of AWS Secrets Manager, focusing on its secret rotation capabilities and comparing it to SSM Parameter Store.
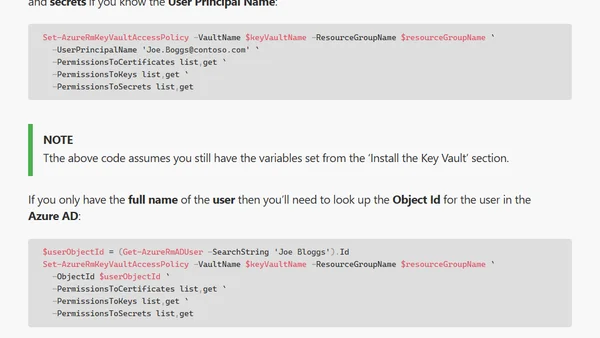
A technical tutorial on setting up and managing Azure Key Vault using PowerShell, covering installation, access policies, and key/secret operations.