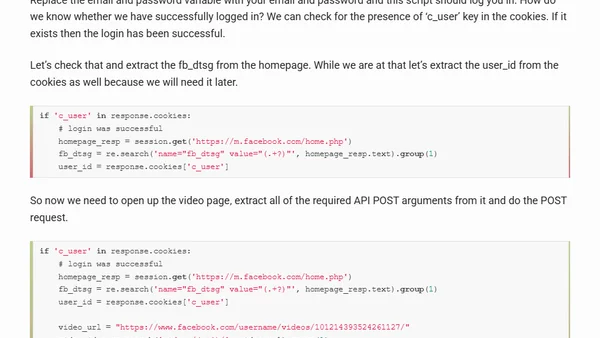
Reverse Engineering Facebook API: Private Video Downloader
A technical guide on reverse engineering the Facebook API to download private videos using Python and browser analysis.

A technical guide on reverse engineering the Facebook API to download private videos using Python and browser analysis.
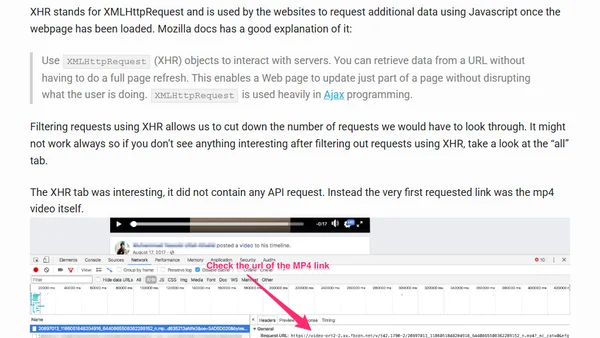
A technical guide on reverse engineering Facebook to create a tool for downloading public videos by analyzing network requests.
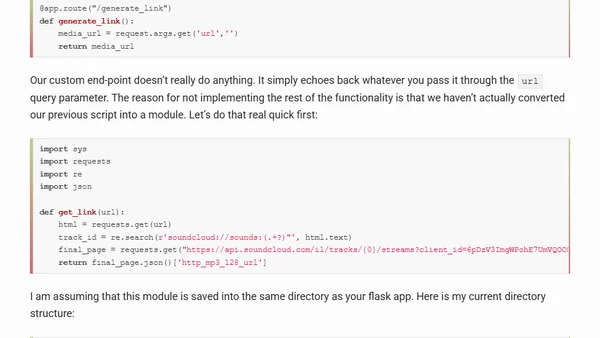
A guide on reverse engineering the Soundcloud API to bypass download restrictions using Python.
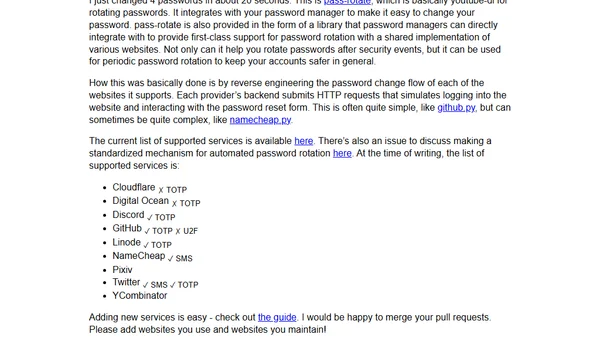
Introducing pass-rotate, a tool for bulk password rotation after security breaches, automating password changes across multiple websites.
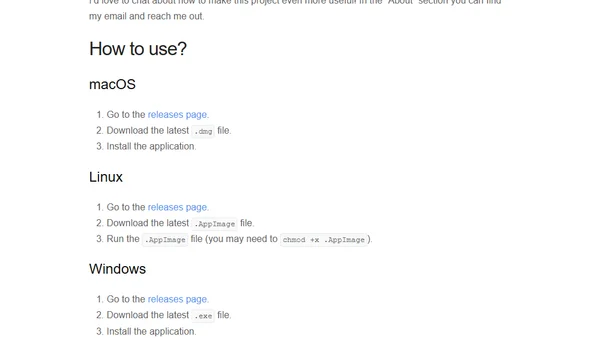
Introducing ngrev, a reverse engineering tool for Angular that visualizes project structure to help developers understand and optimize large codebases.
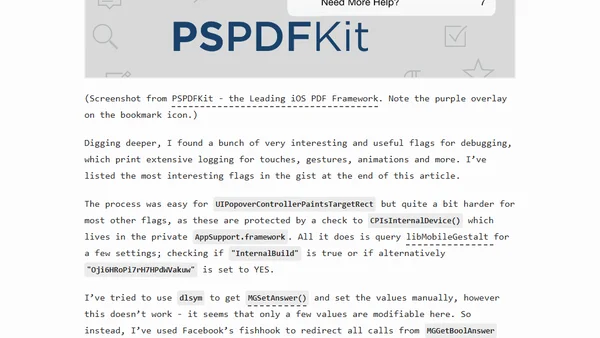
Explores hidden UIKit debug flags and internal preferences for iOS development, including methods to enable advanced logging.
A review of the book 'Learning Pentesting for Android Devices,' covering mobile security, reverse engineering, and network forensics for security professionals.
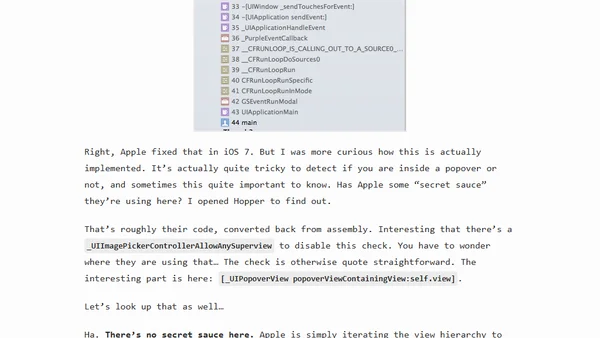
Introduces Aspects, an AOP library for iOS, and demonstrates using it to hack and debug Apple's private popover detection logic.
A guide to editing binary files directly, explaining why it's useful and demonstrating basic techniques with simple tools.
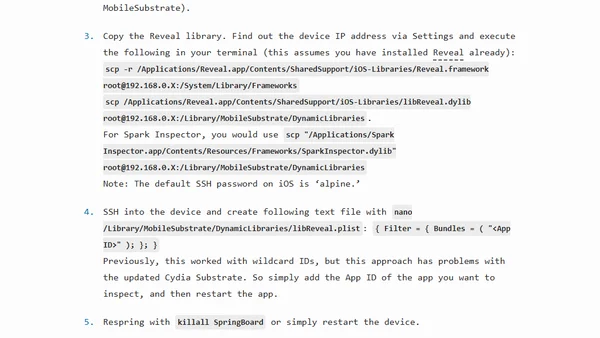
A technical guide on using jailbroken iOS devices and tools like Reveal to inspect the view hierarchy of third-party apps for learning and debugging.
A technical guide on using Python and tools like rtmpdump to reverse engineer and download songs from Myspace.
A summary of a whitepaper detailing new techniques for reverse-engineering Python applications like Dropbox, including security bypasses.
A developer reverse-engineers Office 2013 to change its ALL CAPS menus to lowercase, detailing the debugging and patching process.
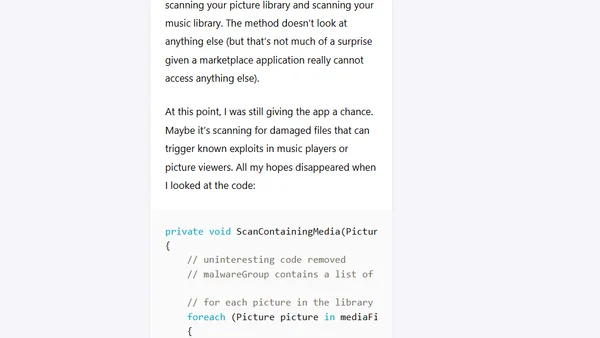
Analysis of the AVG Mobilation antivirus app for Windows Phone, revealing it as a non-functional port with humorous, ineffective scanning code.
Discusses the ethics and consequences of anti-cracking measures in software, advising against deceptive practices that harm user trust.
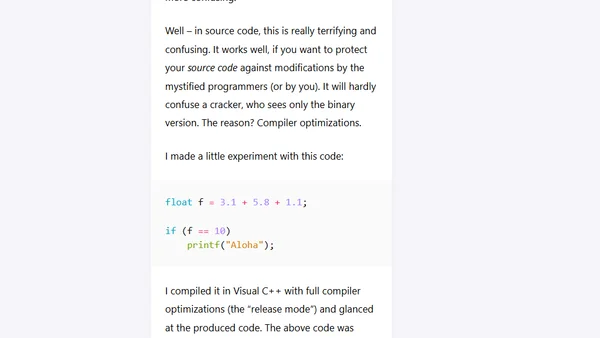
A programmer examines how compiler optimizations can defeat simple anti-cracking code tricks, using a floating-point example.
Explores advanced self-modifying code techniques like polymorphism and metamorphism for software protection and anti-debugging.