Writing a lisp compiler from scratch in JavaScript: 3. LLVM
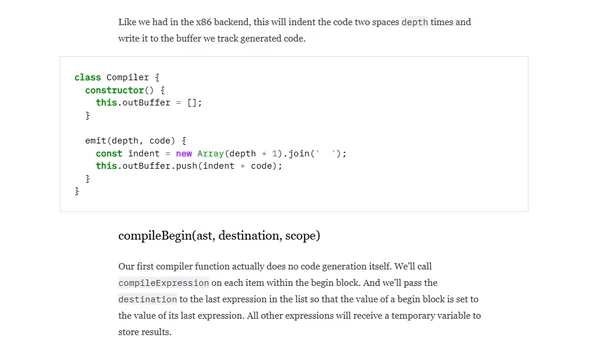
Extending a Lisp compiler to generate LLVM IR instead of x86 assembly, covering IR basics, function definitions, and backend architecture.

Extending a Lisp compiler to generate LLVM IR instead of x86 assembly, covering IR basics, function definitions, and backend architecture.
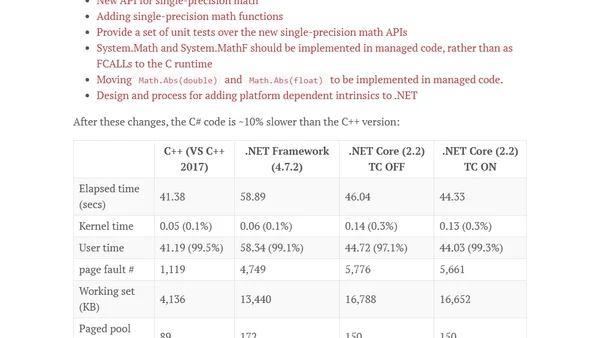
Explores whether C# qualifies as a low-level language by porting a C++ raytracer to C# and analyzing performance, value types, and systems programming.
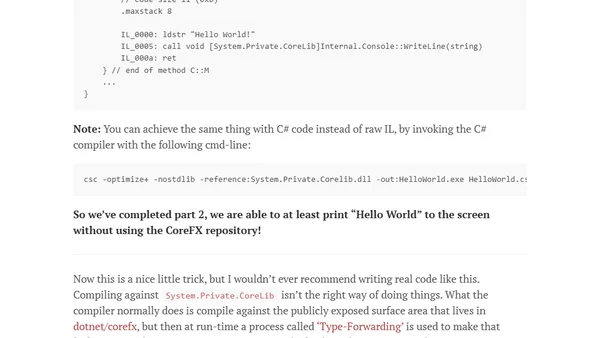
A deep dive into the .NET Core Runtime, exploring its components and building a 'Hello World' app from the raw CoreCLR source.

A curated list of blogs and resources for developers to learn about the low-level internals and performance of the .NET runtime and CLR.

An introduction to CPU branch prediction, explaining its purpose and classic algorithms to understand modern research.

Explores the .NET IL Interpreter, its purpose for CLR bring-up and learning, and how to enable it in the CoreCLR source code.
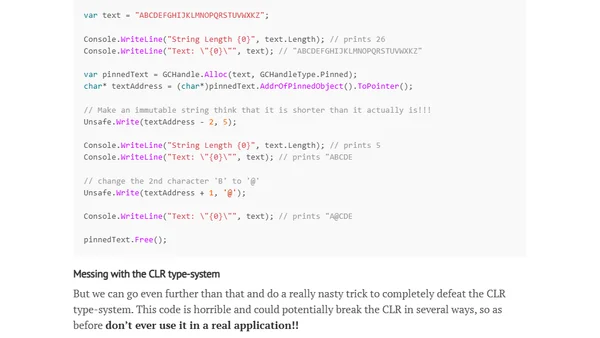
Explores the System.Runtime.CompilerServices.Unsafe API in .NET for low-level, high-performance pointer manipulation while bypassing standard type safety.
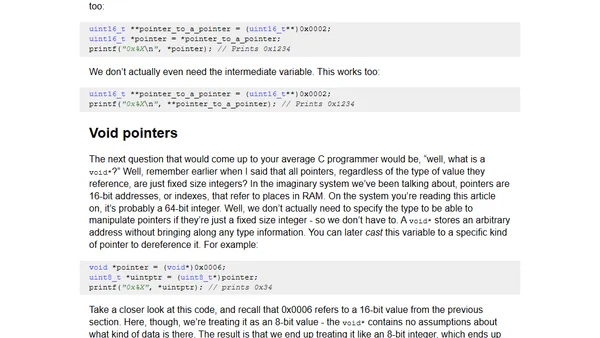
A technical tutorial explaining the fundamentals of pointers in C programming, covering memory addresses, dereferencing, and data representation.
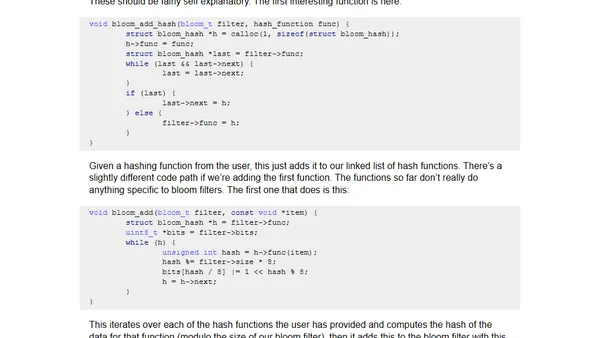
A technical guide presenting an improved Bloom filter implementation in C, focusing on custom hashing and efficient bit-level operations.
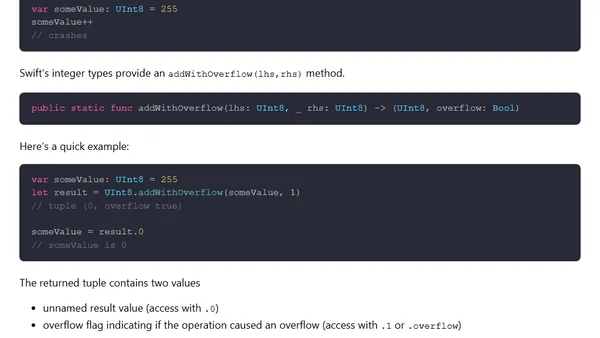
Explains how Swift handles integer overflow using specific methods like addWithOverflow, preventing crashes.
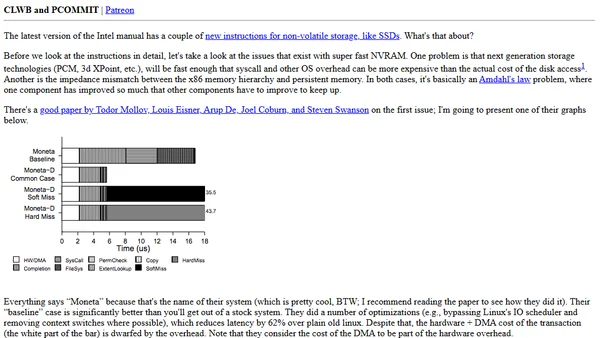
Explains new Intel CLWB and PCOMMIT instructions for managing non-volatile memory (NVRAM) and overcoming performance bottlenecks.
Explains how HdrHistogram's .NET port controls class field layout to minimize overhead for low-latency performance measurement.
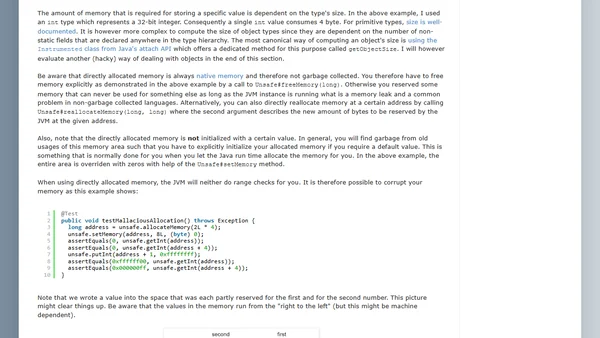
Explains the sun.misc.Unsafe class in Java, its uses for low-level programming, and its future in the Java API.
Lithium is an x86 assembler written in Clojure, created as a fun side project to generate bare metal code.
Explains why checking native byte order in code is usually wrong and demonstrates portable, endianness-agnostic data extraction techniques.