Multitenancy Techniques for EF Core
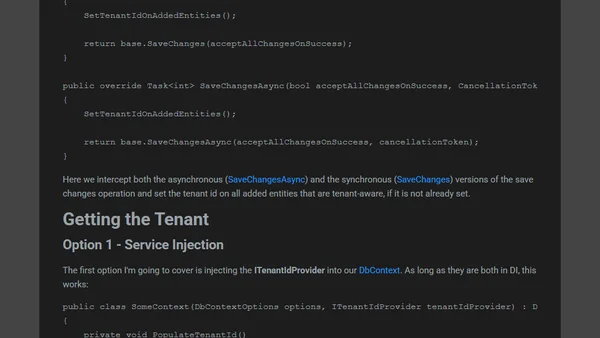
Explores three techniques for implementing multitenancy in EF Core applications, focusing on tenant isolation strategies and context configuration.

Explores three techniques for implementing multitenancy in EF Core applications, focusing on tenant isolation strategies and context configuration.

Explores advanced techniques attackers use to bypass SQL Server data access auditing and provides mitigation strategies to close security gaps.

Explores methods to bypass data access auditing in Microsoft SQL Server and provides guidance on how to close these security gaps.
Explains the Repository design pattern in C#/.NET, covering its purpose, basic implementation, benefits, and potential drawbacks.
A manifesto proposing Upspin, a global file system to restore user data ownership and enable seamless sharing between programs and people.
A tutorial on using ROpenSci packages to connect to and retrieve data from online scientific repositories.
![[Entity Framework v4] Identity map pattern](https://alldevblogs.blob.core.windows.net/thumbs/article-7bc5cda01785-full-5636e833.webp)
Explains the Identity Map pattern in Entity Framework v4, a key ORM concept for preventing duplicate object instances and ensuring data consistency.
Discusses the continued relevance of the Data Access Object (DAO) pattern in modern software development, even when using OR Mappers like JPA.
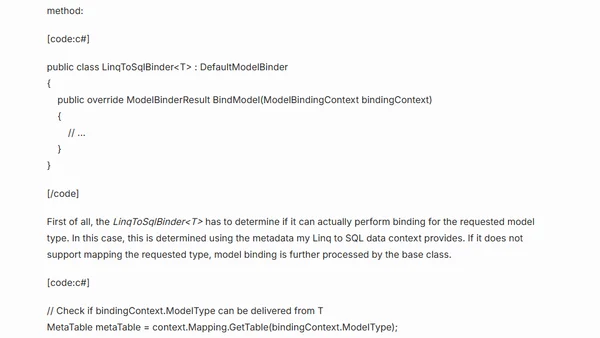
A tutorial on creating a custom ASP.NET MVC ModelBinder to automatically bind Linq to SQL entities from URL parameters, reducing controller code.
A summary of a talk by Spring JDBC lead Thomas Risberg on performance tuning for data access in Spring applications, covering JDBC, transactions, and ORM configuration.