Thoughts on Conway's Law and the software stack
Explores how Conway's Law reveals communication gaps between hardware, firmware, kernel, and software layers, using examples like Spectre and Kubernetes.
Jessie Frazelle is a technologist and author specializing in hardware, software, and data center technologies. She writes about chip design, mechanical CAD, energy systems, 3D printing, and security in computing.
67 articles from this blog

Explores how Conway's Law reveals communication gaps between hardware, firmware, kernel, and software layers, using examples like Spectre and Kubernetes.

A developer shares their learning process by exploring the RISC-V instruction set architecture, explaining ISAs and RISC principles.
A software engineer defines the qualities of a Distinguished Engineer, focusing on technical leadership, continuous learning, and empowering others.
A technical blog discussing unikernels on RISC-V, open firmware, and hardware security topics from tech conferences.
A software engineer's curated list of recommended books, focusing on romanticized tech history, non-fiction, and personal development.
A developer's updated reflections on Intel SGX technology, considering its original DRM purpose and new use cases for secure cloud execution.
A passionate blog post about the power and creative uses of the LD_PRELOAD environment variable in Linux.
Reflects on the end of Moore's Law and the passion-driven era of garage computer builders, drawing parallels to modern tech culture.
A developer explores open-source firmware projects like OpenBMC and u-bmc, discusses Intel Management Engine security, and shares insights from the Theranos book.
A design doc for a secure, multi-tenant container orchestrator to run isolated third-party code, focusing on security layers and OS requirements.
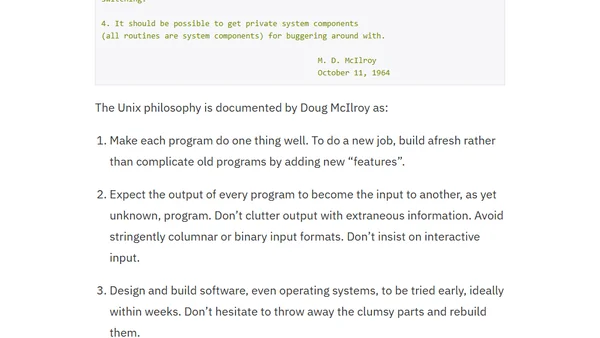
An exploration of the Unix pipe command, its history, and the philosophy of simple, composable tools in software design.
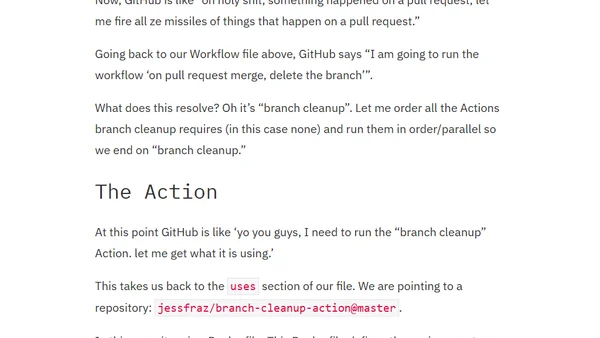
A technical walkthrough explaining how GitHub Actions work, from event triggers to workflow execution, using a branch cleanup example.
Argues that Kubernetes is often unnecessary complexity and suggests simpler container orchestration alternatives for specific use cases.
A guide to installing and using the WireGuard VPN with Docker containers, including kernel module installation and tool usage.
A compilation of technical talks on open source firmware, container security, Intel SGX, and cloud-native infrastructure from 2017-2019.
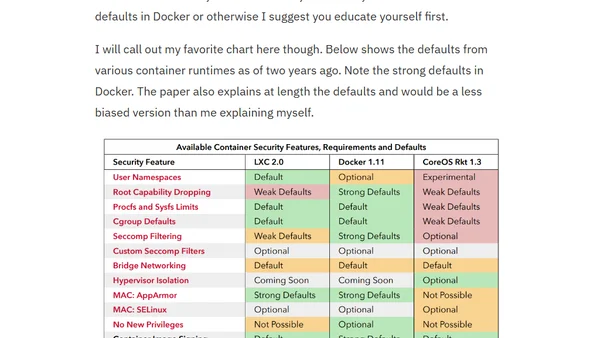
A critique of container security messaging, arguing that existing defaults like Seccomp and AppArmor provide robust, multi-layered sandboxing.
Explores the challenges and security implications of implementing hard multi-tenancy in Kubernetes, where tenants are untrusted and isolated.
Explores methods for building secure, unprivileged container images within Kubernetes clusters without compromising security.
A developer explores using Linux's BINFMT_MISC to run scripts in any language via containers, building on a Cloudflare post about scripting in Go.
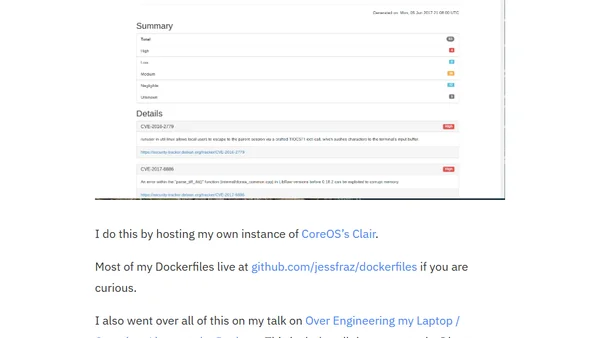
A developer details their personal infrastructure setup, including a self-hosted Jenkins CI server, private Docker registry, and various automation tools.