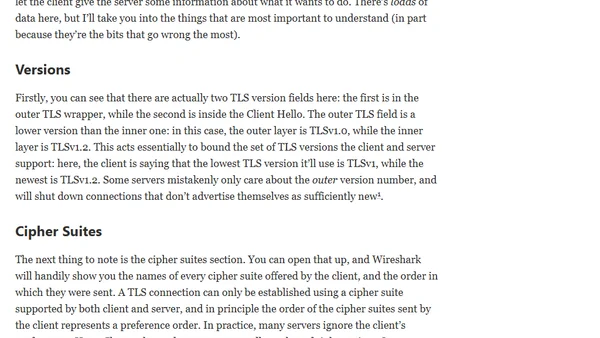
Debugging With Wireshark: TLS
A guide on using Wireshark to debug and analyze TLS handshakes, helping to decipher cryptic errors and understand network protocol issues.

A guide on using Wireshark to debug and analyze TLS handshakes, helping to decipher cryptic errors and understand network protocol issues.
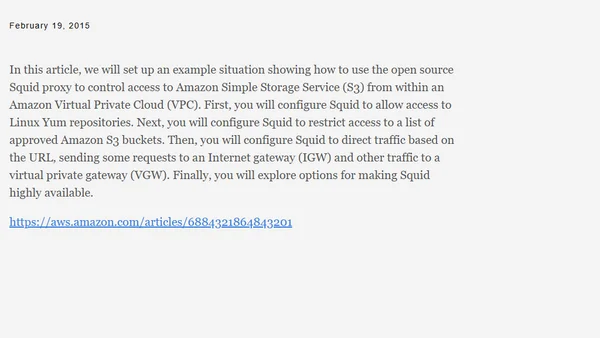
A technical guide on configuring Squid proxy to control and route access to Amazon S3 buckets and Yum repositories within an AWS VPC.
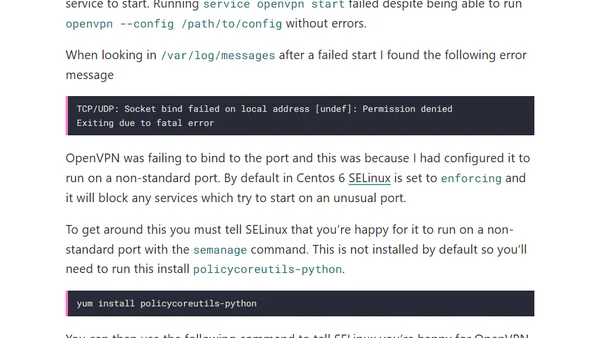
Guide to configuring OpenVPN on a non-standard port with SELinux on CentOS 6, resolving permission and binding errors.
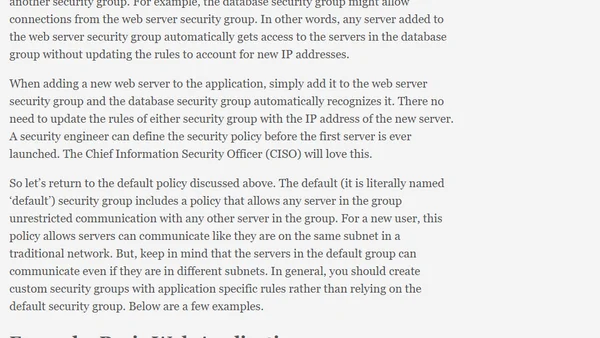
Compares AWS Security Groups to traditional firewalls and outlines best practices for developing an effective security group policy.
A review of the book 'Learning Pentesting for Android Devices,' covering mobile security, reverse engineering, and network forensics for security professionals.
A roundup of interesting Python projects, including Lans.py, CherryMusic, Python Wheels, Dataset, and Openpyxl.
A guide to organized FreeRADIUS 1 & 2 sample configuration files, located in the contrib/configs directory.
Explains the eight common but false assumptions developers make when building distributed systems, leading to major issues.
A 2003 review of Vonage IP telephony service, covering features, portability, security concerns, and practical setup tips.