Jesse's 2025 TLA+ Community Event Notes
Summary of talks from the 2025 TLA+ Community Event, focusing on formal methods and model-guided fuzzing for distributed systems.

Summary of talks from the 2025 TLA+ Community Event, focusing on formal methods and model-guided fuzzing for distributed systems.

Explores how long to run deterministic and non-deterministic tests to find bugs, analyzing fuzzing efficiency and exponential cost models.
A guide to creating a reproducible Nix workflow for fuzz testing the netconsd network daemon using persistent mode.
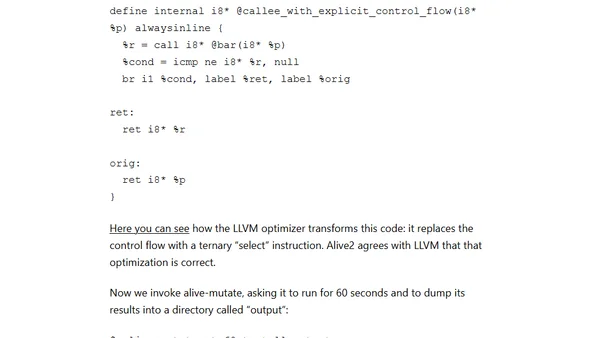
Explores a hybrid fuzzing approach combining mutation-based fuzzing with formal methods (Alive2) to find bugs in LLVM optimization passes.
Analysis of fuzzing ImageMagick and GraphicsMagick with OSS-Fuzz, revealing hundreds of security bugs despite prior audits.
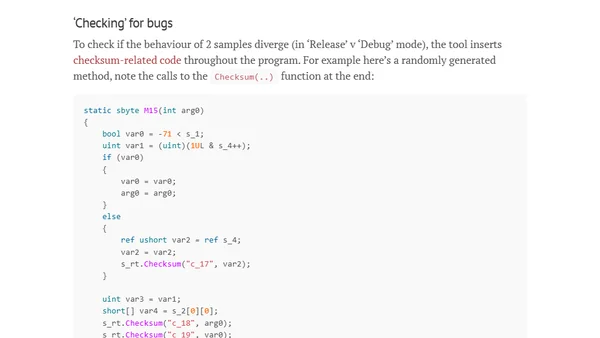
Explores the Fuzzlyn project, a fuzzer that generates random C# programs to find bugs in the .NET JIT compiler by comparing Debug and Release outputs.
Argues that memory unsafety is a widespread, unnamed vulnerability causing thousands of bugs, and advocates for adopting memory-safe languages like Rust.
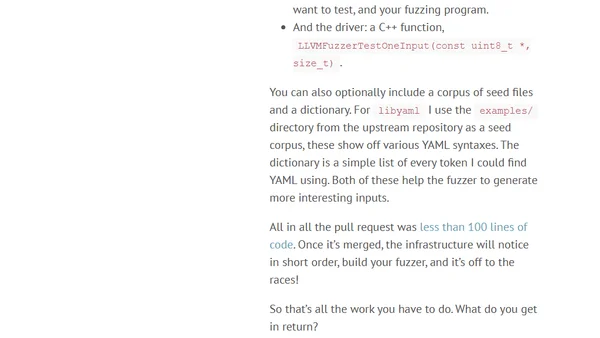
A developer's initial experience using Google's OSS-Fuzz project to perform large-scale fuzz testing on the open-source libyaml library.
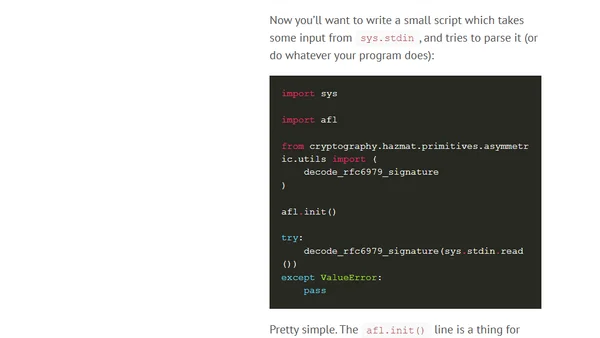
A guide to using the AFL fuzzing tool to test Python code for bugs and security vulnerabilities by generating random inputs.