Analyzing Workload Identity Activity Through Token-Based Hunting
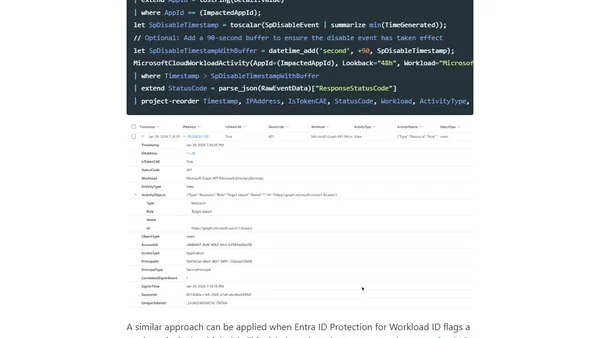
Read OriginalThis article details the creation and use of a custom KQL function, 'MicrosoftCloudWorkloadActivity', for security monitoring. It explains how to hunt for anomalous token usage by non-human identities (applications, service principals) in Microsoft Entra, covering the query's logic, data sources, and its importance due to the high risk and limited security controls for workload identities.
0 comments
Comments
No comments yet
Be the first to share your thoughts!
Browser Extension
Get instant access to AllDevBlogs from your browser
Top of the Week
1
2
Better react-hook-form Smart Form Components
Maarten Hus
•
2 votes
3
AGI, ASI, A*I – Do we have all we need to get there?
John D. Cook
•
1 votes
4
Quoting Thariq Shihipar
Simon Willison
•
1 votes
5
Dew Drop – January 15, 2026 (#4583)
Alvin Ashcraft
•
1 votes
6
Using Browser Apis In React Practical Guide
Jivbcoop
•
1 votes