Using Docker-in-Docker for your CI or testing environment? Think twice.
Read OriginalThis technical article analyzes the use of Docker-in-Docker (DinD) for CI pipelines and testing environments. Originally created for Docker development, DinD can cause issues with security modules (SELinux/AppArmor) and storage drivers. The updated post recommends bind-mounting the Docker socket as an alternative and discusses modern solutions like rootless containers and sysbox for safer, privileged container execution.
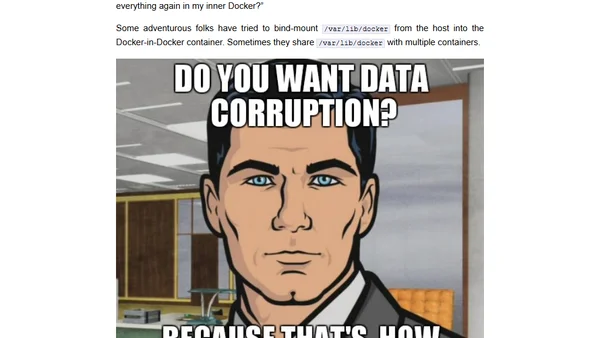
Comments
No comments yet
Be the first to share your thoughts!
Browser Extension
Get instant access to AllDevBlogs from your browser
Top of the Week
1
2
Better react-hook-form Smart Form Components
Maarten Hus
•
2 votes
3
AGI, ASI, A*I – Do we have all we need to get there?
John D. Cook
•
1 votes
4
Quoting Thariq Shihipar
Simon Willison
•
1 votes
5
Dew Drop – January 15, 2026 (#4583)
Alvin Ashcraft
•
1 votes
6
Using Browser Apis In React Practical Guide
Jivbcoop
•
1 votes